
Infostealers account for surge in identity-enabled attacks
Analysis of almost 93,000 threats detected within more than 308 petabytes of security telemetry by Red Canary shows infostealer malware infections on the rise across both Windows and macOS platforms.
Used to gather identity information and other data at scale, in 2024 LummaC2 was the most prevalent stealer detected in 2024, operating under a malware-as-a-service model, and selling for anywhere from $250 per month to a one-time payment of $20,000.

Number of compromised credentials up by 33 percent
The latest Global Threat Intelligence Report (GTIR) from Flashpoint finds that threat actors compromised over 3.2 billion credentials in 2024, a 33 percent increase from the year before.
Of these 75 percent or 2.1 billion, were sourced from information stealing malware, a dangerous new twist on an older threat that has infected over 23 million devices worldwide.

The cost conundrum of cloud computing
For most businesses, change is driven by the need to reduce risk and innovate, while optimizing cost and return on investment. In the case of cloud adoption, the powerful functionality offered by these platforms enable businesses to streamline, optimise, and make their workflows more efficient which, in turn, helps reduce costs. Organizations are always looking for the best solutions for optimizing efficiency and reducing costs, particularly in uncertain economic times.
Yet, in reality, migrating to the cloud does not always bring the cost optimization and savings that an organization is looking to benefit from. Depending on which cloud solution is being evaluated, along with how the solution is designed, built, and deployed, the result may not deliver on the project’s original goals.

Seamless cloud migration: Building an AI-optimized future
Implementing cloud services with AI technologies, such as Microsoft Copilot, is fundamental for IT providers seeking to offer advanced solutions. However, with greater dependence on AI-generated tools to foster innovation and productivity in organizations, the necessity of enabling cloud environments to host these sophisticated capabilities has become paramount.
Their successful integration, however, comes at the expense of having additional investments in computing power, data analytics, and intelligent security solutions that shield sensitive information from unauthorized access. Many companies first need to accomplish a cloud migration to improve the security posture of the infrastructure before implementing AI.

PNY CS2342 M.2 2230 NVMe PCIe Gen4 x4 SSD delivers fast speeds in a tiny package
PNY has announced its latest solid state drive -- the diminutive CS2342. This M.2 2230 NVMe PCIe Gen4 x4 SSD is impressively fast, with read speeds hitting up to 7,300MB/s and write speeds reaching 6,000MB/s.
Available in 1TB and 2TB capacities, the CS2342 is primarily designed for gamers looking to upgrade devices like the Steam Deck, ASUS ROG Ally, or MSI Claw. With that said, it’s not only compatible with gaming handhelds -- this drive will technically also work in laptops and desktops.

Organizations struggle with too many data loss prevention alerts
A new report finds 78 percent of organizations report being challenged by administering and maintaining existing data loss prevention technology solutions and policies, and 94 percent report using at least two tools and, on average, more than three tools with DLP capabilities, resulting in significant man-hours to administer and maintain multiple solutions.
The study from DLP specialist MIND and Enterprise Strategy Group also shows 91 percent of organizations say it's important to reduce alert noise produced by their current DLP controls due to simple, poor and outdated classification schemes.

Trust in digital services in decline
A new survey of over 14,000 consumers across 14 countries finds that most industries experienced a decline in consumer trust compared to last year.
The latest Digital Trust Index from Thales shows banking tops the index for the second year in a row, but levels of trust have fallen among Gen Z customers.

TikTok launches Security Checkup tool to help users keep their accounts protected
Embattled social platform TikTok has announced a new Security Checkup tool. It has been designed as a one-stop dashboard where users can check and update all of their account security settings.
The security tool is similar to those provided by the likes of Google and Meta, and it helps to promote the idea of users being proactive in ensuring account security. Importantly, there is a lot of hand-holding to eliminate the feeling of intimidation that some people may otherwise have felt about security issues such as passkeys and two-step verification.
GIMP 3.0 is here -- the best free Photoshop alternative just got a huge upgrade
When I suggest to someone that they switch to Linux, they often ask me the same question -- will I be able to run Adobe Photoshop? The answer, of course, is no (for the most part). However, I always follow up by suggesting the totally free (and open source) GIMP. For some people, GIMP isn’t just comparable to Photoshop -- it is superior.
And now, following an agonizing seven years of development, GIMP 3.0 has finally arrived for Windows, macOS, and Linux. This open-source program has been completely overhauled with a modernized interface, non-destructive editing, expanded file format support, and major performance improvements.

TRIBIT StormBox Lava Bluetooth speaker brings 80W of booming bass and 24-hour battery life
TRIBIT has launched its latest Bluetooth speaker -- the StormBox Lava. Packed with 80W of room-filling sound, ultra-deep bass, and rugged durability, it is designed to keep the music going whether you’re at home, by the pool, or out on an adventure.
This speaker isn’t messing around when it comes to sound. With dual 30W neodymium magnet woofers and dual 10W silk dome tweeters, the StormBox Lava delivers crisp highs, rich mids, and floor-shaking bass. TRIBIT’s XBass technology pushes the low end all the way down to 43Hz, so every beat hits with solid depth and power. In addition, the 360-degree sound dispersion means you should get an immersive audio experience from any angle.

AI growth drives demand for more data center bandwidth
The rapid growth of AI workloads is driving a major transformation in data center network infrastructure according to a new study from Ciena.
The research, conducted by Censuswide, surveyed more than 1,300 data center decision makers across 13 countries. 53 percent of respondents believe AI workloads will place the biggest demand on data center interconnect (DCI) infrastructure over the next two to three years, more than cloud computing (51 percent) and big data analytics (44 percent).
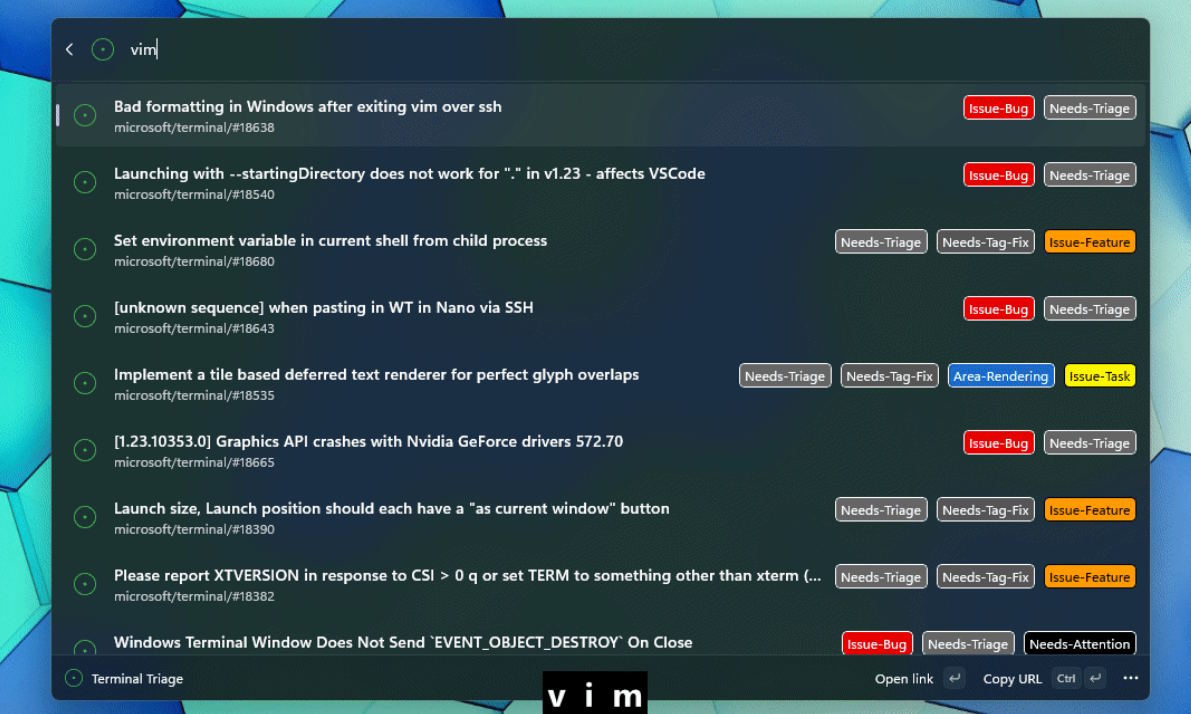
If you’re a fan of PowerToys Run, you’ll absolutely love the upcoming Windows Command Palette module
There is a lot -- and we mean a lot -- to love about PowerToys, and one of the most popular components of the utility collection is PowerToys Run. Loved by power users, this module is a super-powered launcher, search tool, terminal, command line, and more all wrapped up in one.
And soon it could be bettered. We’re not talking about an update version of PowerToys Run with new capabilities, but a completely new module -- Windows Command Palette. Also known as CmdPal, Windows Command Palette is described as the “next iteration of PowerToys Run”.

How GenAI is set to change procurement [Q&A]
In recent years generative AI has made its way into many areas of business, helping to transform and streamline processes. However, its potential in the procurement space remains relatively unexplored.
We talked to Kevin Frechette, CEO of Fairmarkit, to find out how enterprises can exploit GenAI to gain agility, efficiency, and smarter decision-making in their sourcing decisions.

Debian Linux 12.10 drops just in time for St. Patrick’s Day with security fixes
St. Patrick’s Day is all about luck (plus corned beef and cabbage, of course), but when it comes to your Linux system, relying on luck isn’t exactly the best security strategy. Thankfully, Debian 12.10 has arrived just in time for the big Catholic holiday, bringing a fresh batch of security fixes and system updates to keep “bookworm” running smoothly.
If you’ve been keeping up with security updates from security.debian.org, you’re probably already covered on most of these fixes. But for those who haven’t, it’s time to update. Just point your package manager to a Debian mirror, and you’re good to go. New installation images will are available here if you’re starting from scratch.

Need to search terabytes of enterprise data? Tips for getting quickly to that 4-leaf clover
If you find yourself in a springtime clover field hunting for that rare 4-leaf clover, the journey is the reward. Not so if you and your team are hunched over your desks hunting 4-leaf clovers in terabytes of enterprise data. While combing through millions of files is never a “walk in the park,” enterprise search makes this process exponentially more pleasant.
To enable instant concurrent searching across terabytes, enterprise search first has to index the data. Indexing is simple: just tell the indexer the folders, emails archives and the like to index, and the software will take it from there. (This article uses dtSearch for its specifics on enterprise search but there are other comparable products on the market.) Tip: the files to index can be local or remote like SharePoint attachments, OneDrive / Office 365 files, etc. that appear as part of the Windows folder system.