
Firewalla Orange is a pocket-sized WiFi 7 router with multi-gigabit firewall
Firewalla has announced Firewalla Orange, a portable multi-gigabit firewall and WiFi 7 router built to bring Zero Trust protection to networks in homes, offices, and travel setups. It’s the latest product in the company’s range of cybersecurity devices that includes Firewalla Purple and Firewalla Gold SE.
The new product delivers an advanced security stack that includes intrusion prevention, VqLAN microsegmentation, device isolation, GEO-IP filtering, VLAN support, and Active Protect rules that shut down threats in real time. It’s rated for more than 2Gbps of packet processing, so can support cloud services, smart home devices, and remote work activity.
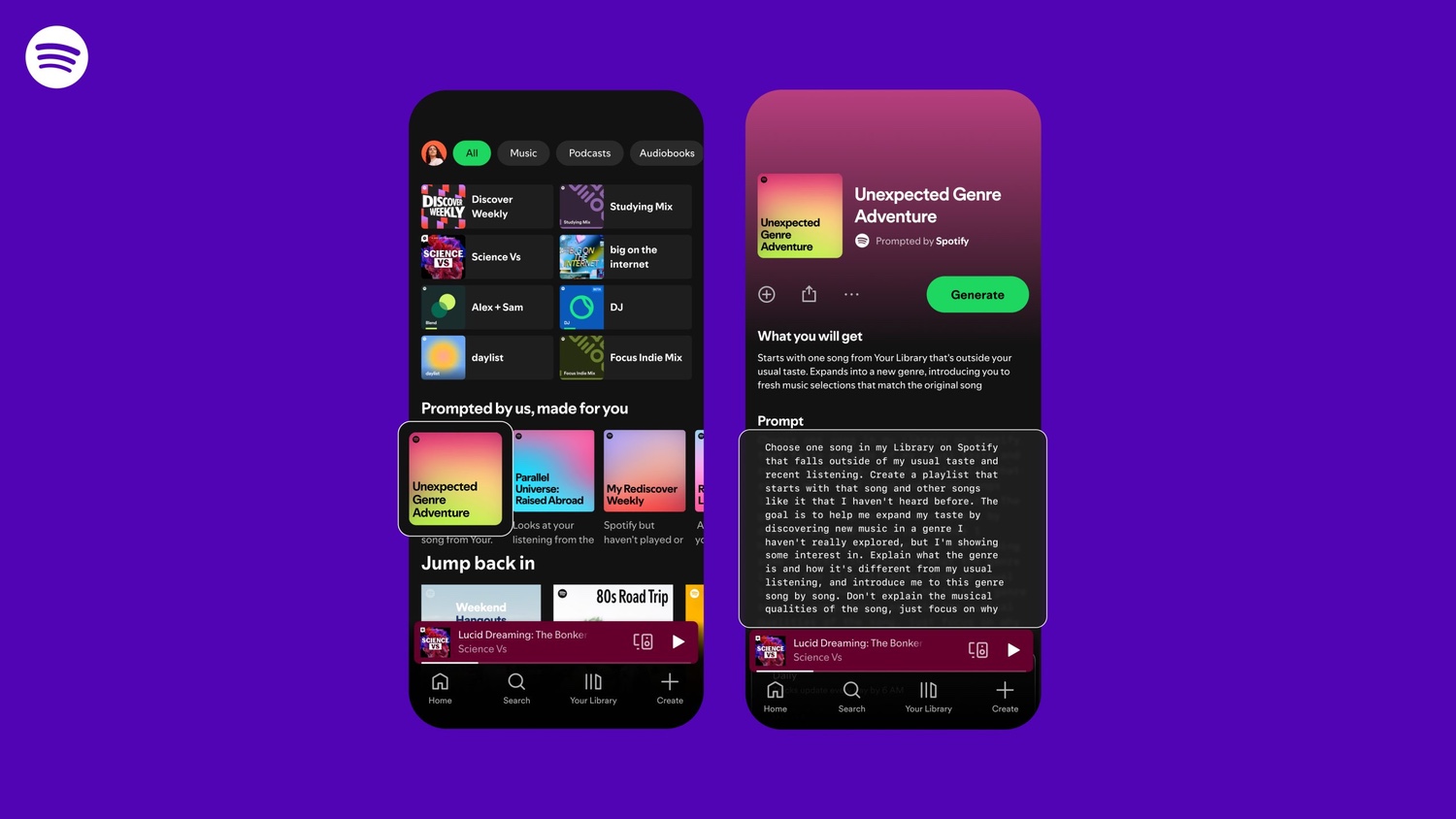
Spotify is testing a new prompt-powered playlist feature
Spotify has announced that it is testing a new playlist creation option that build on the familiarity people have developed with the likes of ChatGPT. Called Prompted Playlist, the feature gives users a way to create personalized playlists while still benefitting from some AI input.
This is just the latest in a long time of playlist creation options offered by Spotify, and the company says that the idea is to not only push the boundaries of listening, but also to give users greater control.
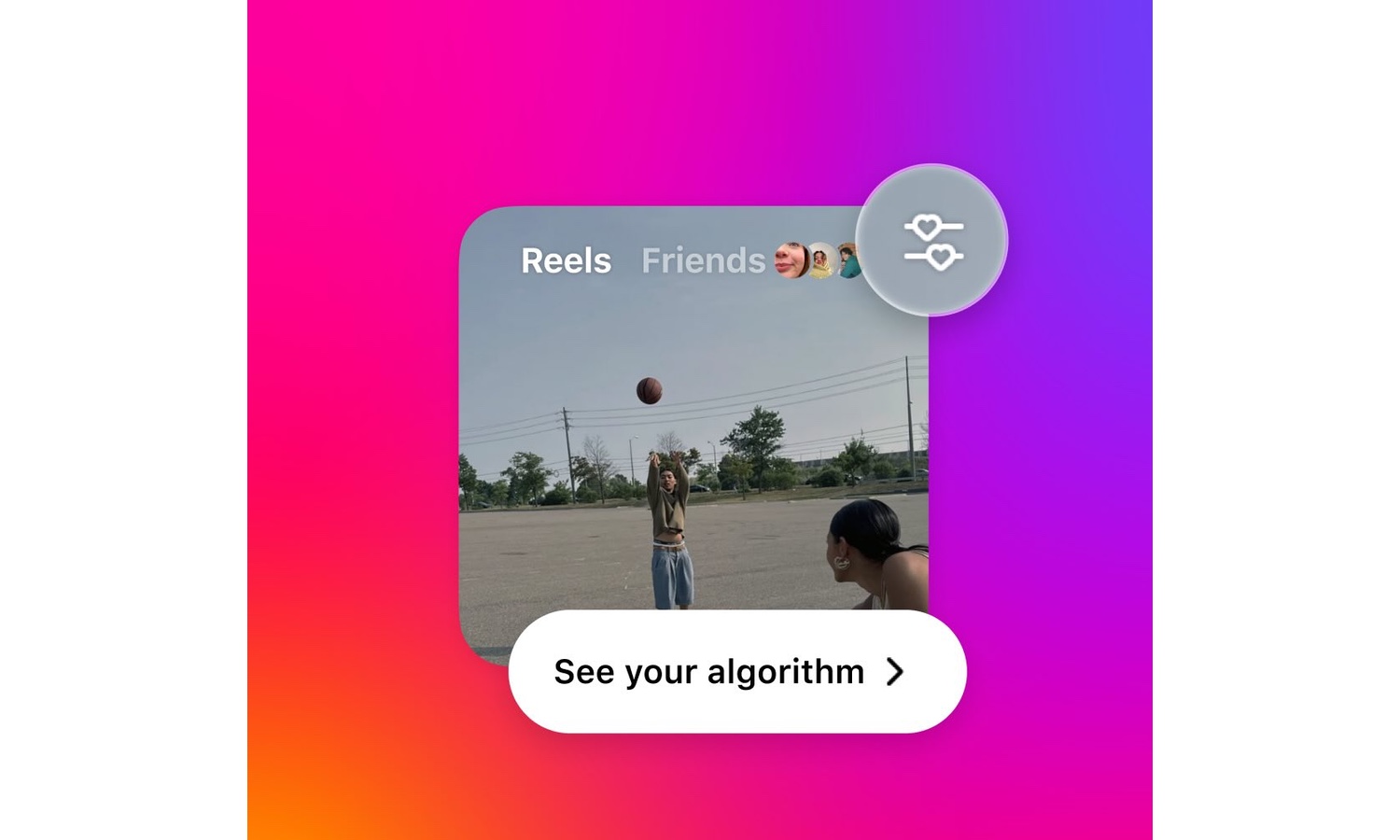
Meta is giving all US Instagram users control over the Reels algorithm
After testing giving users control over the algorithm that controls the display of Reels on Instagram, Meta has now rolled out this personalization feature to everyone in the US.
With algorithms so easily thrown off by a rogue period of viewing, these new controls give users a way to redirect the algorithm back in the direction they would prefer. It is a quick and easy way to make it clear the type of content you are definitely interested in, as well as indicating the stuff that you really don’t want to see.
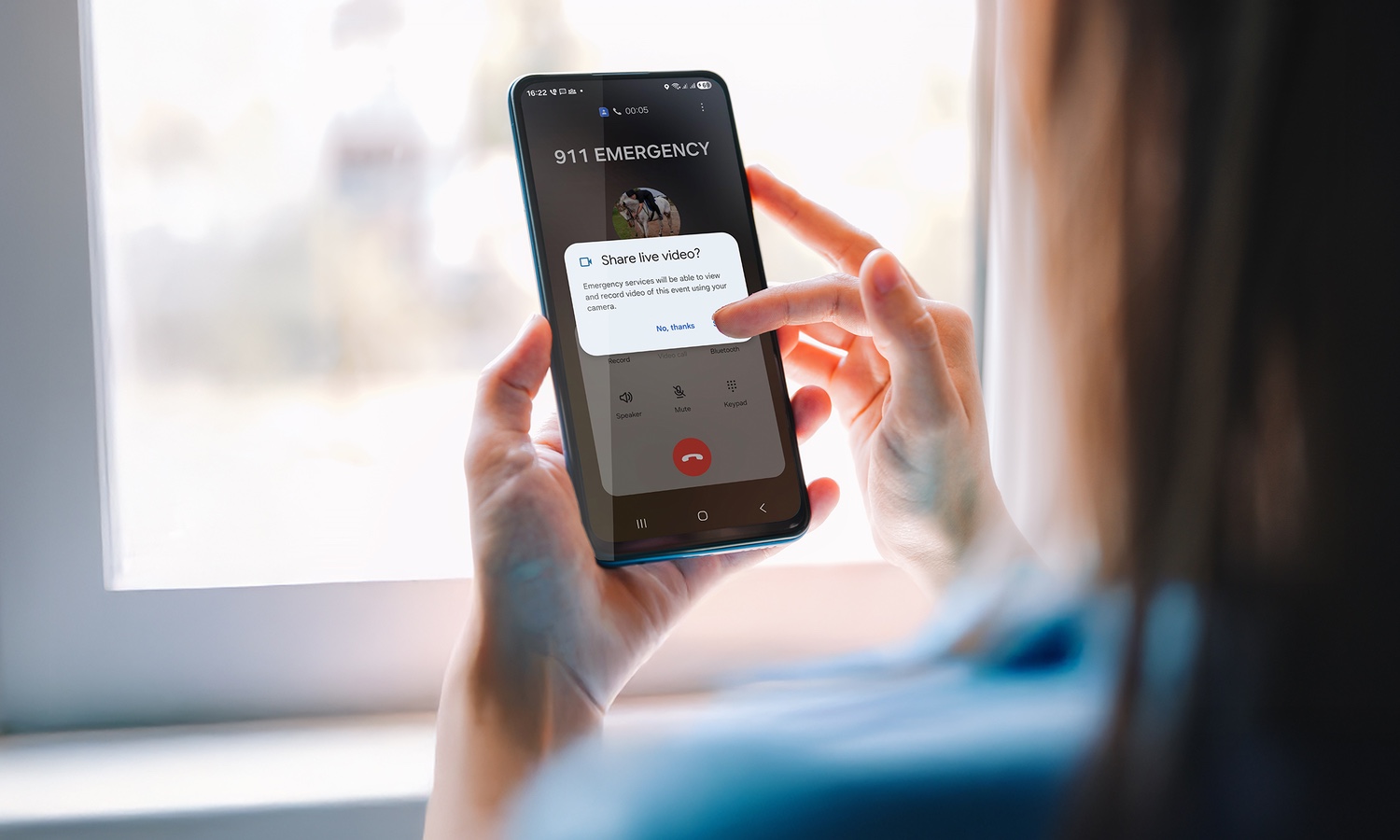
Google launches Android Emergency Live Video to assist 911 calls
Google has launched a new feature for Android users that makes it possible to share live video with emergency services. Android Emergency Live Video is meant to help 911 call handlers get a better idea of what is going on in an emergency situation.
The feature is available in the US, and it works with Motorola’s 911 command center software which is used in more than half of North America’s public safety answering points (PSAPs).
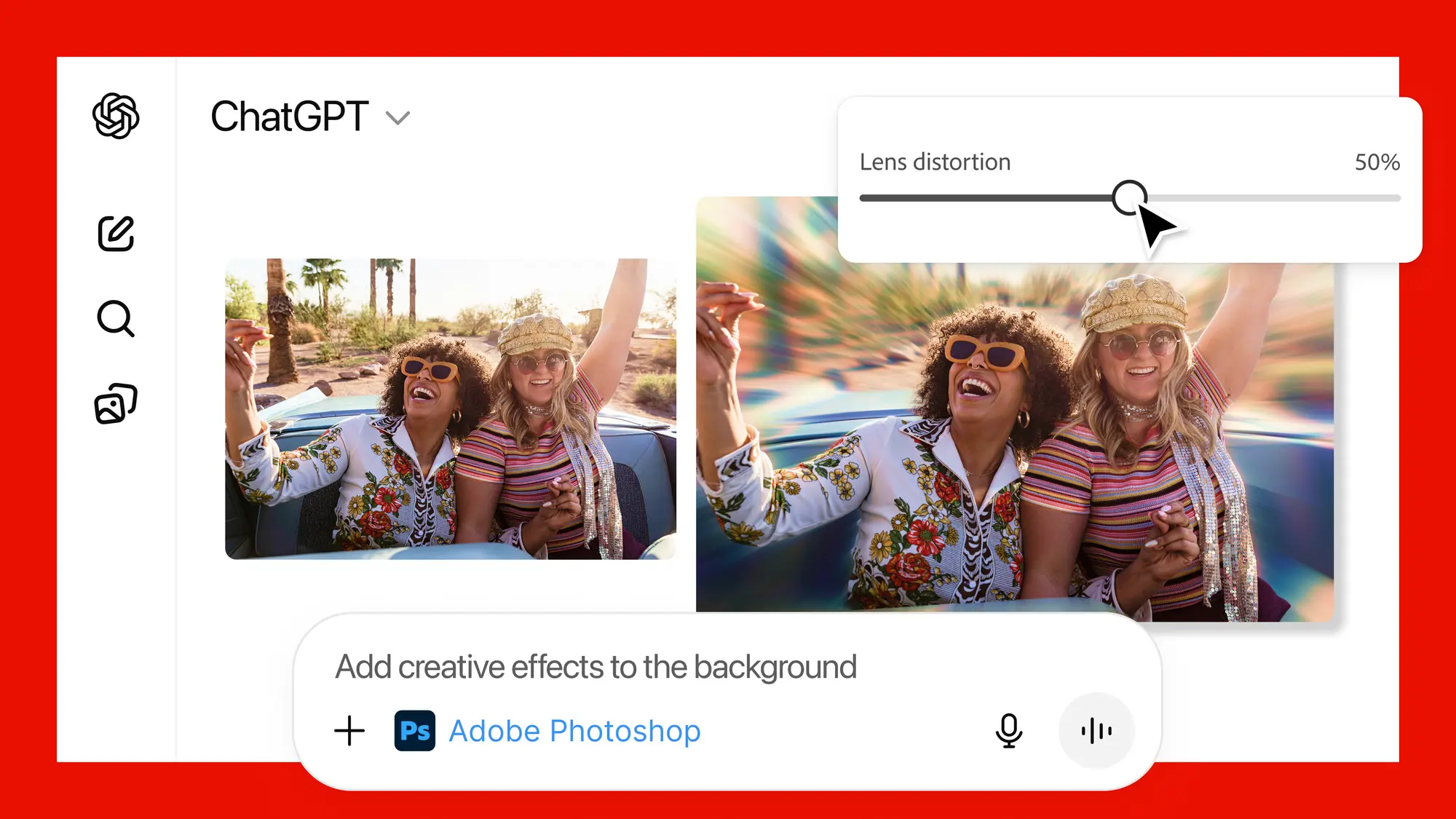
Adobe launches Photoshop, Express and Acrobat inside ChatGPT -- for free
Adobe has launched Photoshop, Adobe Express and Acrobat inside ChatGPT, giving the AI platform’s 800 million weekly users direct access to its most popular creative and productivity tools.
The integration combines Adobe’s image editing knowhow with ChatGPT’s conversational interface, allowing people to edit photos, design content and transform documents simply by describing what they want to do.

Asus ROG launches Raikiri II Xbox wireless controller in the US
Asus ROG (Republic of Gamers) has announced the US retail availability of the Raikiri II Xbox Wireless controller, the company’s first Xbox certified wireless gamepad. On sale through Best Buy, it supports Xbox Series X, Xbox Series S, Windows PCs, and several of Asus' handheld systems including the ROG Ally and Ally X.
The controller uses tunneling magnetoresistance joysticks rather than traditional mechanical designs in order to reduce drift and improve motion accuracy and energy efficiency. It promises a 1000Hz polling rate in both wired and 2.4GHz wireless modes on PC, supported by ROG's SpeedNova wireless technology, which reduces input latency.

Bugcrowd boosts security resilience with new AI features
With attackers moving faster using AI tools and attack surfaces growing more complex, security teams need solutions that remove manual work, deliver secure, context-aware intelligence instantly, and help them shift toward a pre-emptive security model.
This is why Bugcrowd is launching new functionality in the form of Bugcrowd AI Triage Assistant and Bugcrowd AI Analytics, to bring unprecedented speed and intelligence and insights to the process of building security resilience.

Cyber experts warn AI will accelerate attacks and overwhelm defenders in 2026
Cybersecurity experts are offering warnings about the year ahead, and while they come from different backgrounds and companies, their predictions all point to AI changing the nature of attacks, speeding up intrusions and forcing defenders to rethink how they work.
Most analysts expect 2026 to be the first time that AI-driven incidents outpace what the majority of teams can respond to manually, and some see the biggest changes coming from attackers who use fully autonomous systems.

New research institute reveals real-world lessons from AI projects
Work AI specialist Glean has today announced the launch of the Work AI Institute, a first-of-its-kind research initiative dedicated to decoding what actually drives results when companies commit to operating with AI projects at the core of their businesses.
The Work AI Institute brings together leading researchers from Stanford, Harvard, UC Berkeley, Notre Dame, University College London, Emory, and UNC Charlotte to answer the pressing question: What’s really working with AI at work? The Institute blends academic rigor with real-world data, experimentation, and end user insights to help enterprises separate signals from noise and accelerate meaningful AI impact.

Kioxia announces the Exceria Pro G2 -- its fastest consumer SSD to date
Kioxia has taken the wraps of the Exceria Pro G2 SSD, a new flagship in its Exceria personal SSD range. The drive targets enthusiasts and professional users who need very high throughput from PCIe 5.0 storage, and uses the the Japanese memory maker’s BiCS Flash TLC 3D memory and an updated performance controller.
The Exceria Pro G2 reaches sequential read speeds of up to 14,900MB/s and write speeds of up to 13,700MB/s, placing it among the fastest consumer SSDs announced to date. The drive also promises solid random read and write performance, reaching up to 2.3m random read IOPS and 1.95m random write IOPS, which helps improve responsiveness when handling large projects, media assets, and modern games.

Cloud infrastructure is becoming a barrier to growth
Research released today reveals that cloud infrastructure has become the second-largest expense for tech companies, following headcount; averaging 10 percent of revenue and increasing rapidly. What’s more nearly 90 percent of companies report that it's directly affecting profitability.
The study from Cloud Capital surveyed 100 CFOs and senior financial decision makers within SaaS and technology businesses of up to 1,000 employees across the US and UK.

Mozilla expands Firefox’s translation and custom icon availability
It is far from uncommon for the Android and iOS versions of the same app to have different features, and Firefox is no different in this regard. Now Mozilla is leveling the playing field by bringing a previously Android-only feature to iPhone users, and an iOS-only option to its Android app.
While it may seem a little strange considering the widespread availability of the option in other web browsers, the iOS version of Firefox has not featured a web translation option. Now this changes. But there is also a nice change to Android users.

Why concentrating data in AI models demands greater vigilance [Q&A]
Data that was once scattered across sprawling systems and silos -- providing natural obstacles to attackers -- is now concentrated and highly portable within AI models. This fundamental shift redefines the challenge of digital security.
We spoke to Dr. Luigi Caramico, CTO and co-founder of DataKrypto, to discuss how organizations can repond to this challenge.

Strip the AI from Windows 11 with this handy script
If you hate the endless AI that Microsoft is cramming into Windows 11, you are far from alone. While the company may believe that everything can be enhanced with artificial intelligence, there are plenty of users who are yet to be convinced.
Now, there are certainly steps you can take to avoid the AI-ificiation of Windows 11 – including sticking with Windows 10 – but it can take time to implement all of the necessary settings. If only someone has created a script to automate the disabling of AI in Windows 11. Oh… they have. Here it is.
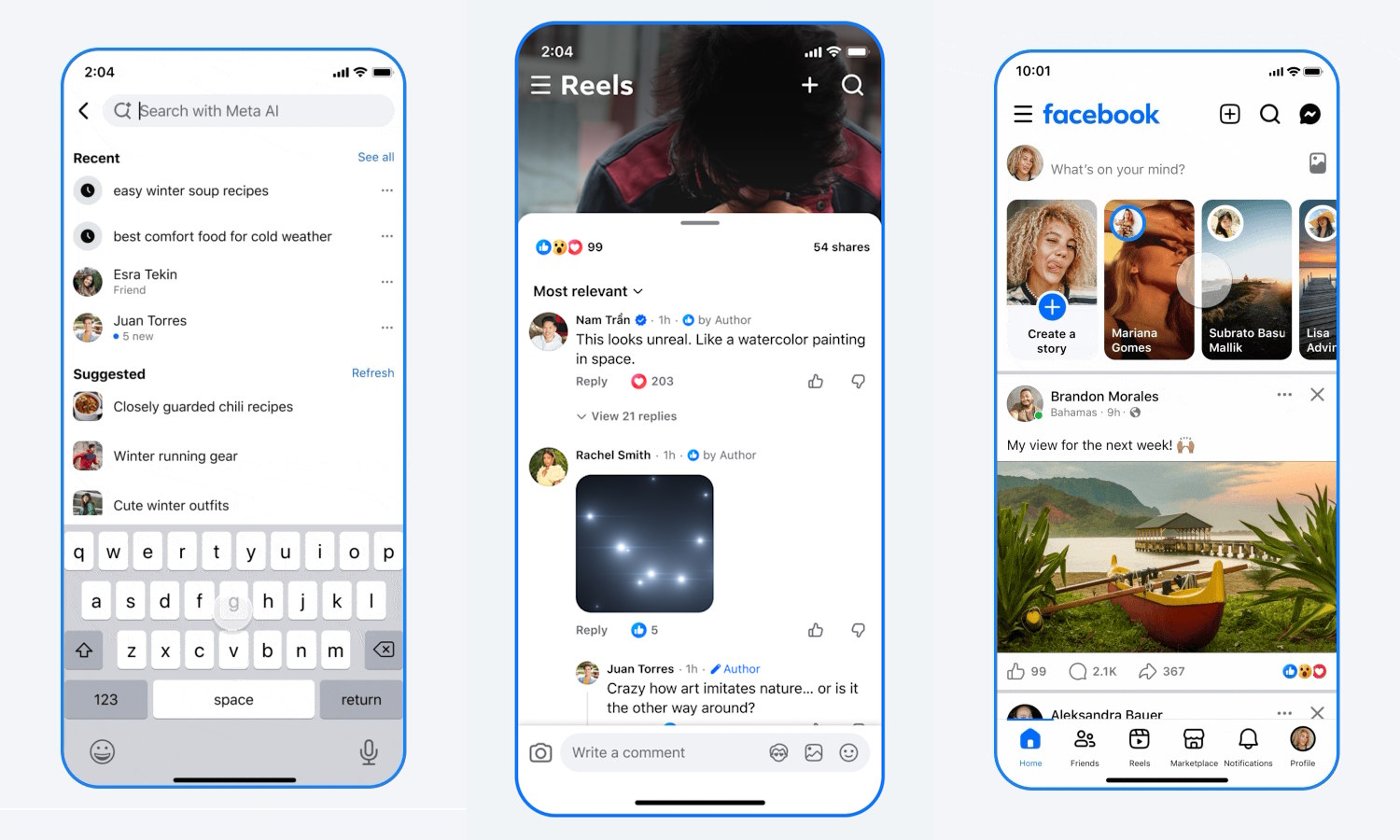
Facebook rolls out new Feed, search, and navigation designs
Meta has announced a series of major design changes to Facebook which it will be hoping will help it to maintain a place of significance in a swamped social media world. The changes are pretty much across the board, but changes to Feeds are likely to be most noticeable.
Revamps to the Feed, search, and navigation systems are consumer facing, but Facebook has not forgotten creators. Improvements have been made to streamline the creation of both Feed posts and Stories.