Best Windows apps this week
Five-hundred-and-sixty-eight in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft announced plans to retire the Tips app on Windows. Three Windows services will also be removed because of security concerns.
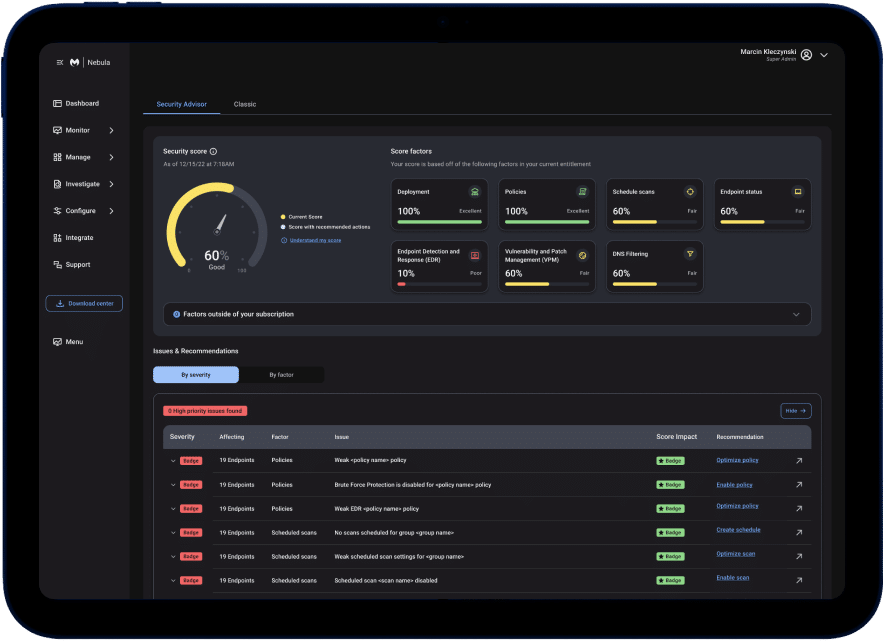
Malwarebytes for Business rebrands as 'ThreatDown'
In a bid to distinguish between its consumer and business offerings, Malwarebytes is relaunching its endpoint security platform for business as ThreatDown.
ThreatDown comes with a new Security Advisor dashboard and is available as a number of bundles that combine protection, threat intelligence, and expertise for IT-constrained organizations, reducing complexity and offering user-friendly security solutions.
Microsoft celebrates two decades of delivering scheduled Windows updates on Patch Tuesday
Patch Tuesday, the second Tuesday of each month when Microsoft releases updates for Windows, has been with us for a long time now. In fact, Microsoft has been using the predictable schedule for releasing patches for no less than 20 years.
The emergence of Patch Tuesday -- a day anticipated for its bug-fixing and dreaded for its bug-introductions -- dates back to the days of Bill Gates and Windows Vista. In celebrating the incredible landmark of two decades of update releases on a reliable timetable, Microsoft has shared some of the history behind it and reiterated the importance of updating the operating system in this way.

How contextual analysis can offer insight into the human element behind cyber threats [Q&A]
Cyber threats can come in many forms, over email, messaging platforms or social media. But what they all have in common is that they seek to exploit human weaknesses.
We spoke to Chris Lehman, CEO of SafeGuard Cyber, to discover how contextual analysis of business conversations can help determine if a conversation is benign or if something suspicious is taking place, allowing action to be taken.

Monoprice launches 40-inch CrystalPro Ultrawide QHD 144Hz USB-C monitor
Monoprice is at it again, folks -- this time with an affordable monitor that promises not just to improve your computing experience, but to completely transform it. Introducing the CrystalPro 40-inch Ultrawide Quad HD IPS panel productivity monitor. If you thought your current screen was sufficient, prepare to have your expectations shattered and your productivity amplified by the impressive 3440x1440 resolution.
Let’s talk real estate -- screen real estate, that is. The CrystalPro’s expansive 40-inch Ultrawide display isn’t just a luxury; it’s a game changer. Gone are the days of alt-tabbing through cramped windows. This monitor lets you spread out your projects for side-by-side efficiency that’ll have you wondering how you ever managed with less space.

Get '500 Great Ways to Save For Dummies' (worth $12) for FREE
With high prices for everything from food to gas, how can you make ends meet -- and still have enough for the things you love?
500 Great Ways to Save For Dummies is packed with creative ideas for cutting costs in small and big ways, in dozens of categories, ranging from groceries and healthcare to education, travel, and major purchases.

SABRENT launches 5-Bay USB-C Docking Station for 2.5-inch SATA HDDs and SSDs with integrated cooling fan (DS-5R15)
If you're in the market to expand your storage without the headache of fiddling with internal SATA ports, the SABRENT 5-Bay USB-C Docking Station (DS-5R15) might just be your ticket to a hassle-free upgrade. This sleek device is all about flexibility and ease, allowing you to stack up to five 2.5-inch SATA HDDs or SSDs -- each up to a towering 15mm in height -- into your tech arsenal.
The true beauty of the DS-5R15 lies in its simplicity: tool-free, hot-swappable, and plug-and-play. That's right, no more screwdrivers, no more shutting down to add or swap out drives. It's as easy as a USB-C connection, with the added bonus of a robust 10Gbps transfer speed courtesy of USB 3.2 Gen 2x1 technology. And don't fret over power; this docking station comes with a 12V/3A external power supply to ensure fast, stable and reliable data transfers.

Governance and security are top priorities for data teams
With ever more organizations rushing to adopt AI solutions, a new report suggests that implementing stronger data governance and security controls will be a higher priority for data teams as we head into 2024.
The report from data security company Immuta finds that only half of respondents say their organization's data security strategy is keeping up with AI's rate of evolution.

Get 'Causal Artificial Intelligence' (worth $21) for FREE
In Causal Artificial Intelligence: The Next Step in Effective, Efficient, and Practical AI, a team of dedicated tech executives delivers a business-focused approach based on a deep and engaging exploration of the models and data used in causal AI.
The book’s discussions include both accessible and understandable technical detail and business context and concepts that frame causal AI in familiar business settings.

WhatsApp now lets you hide your IP address, but there are a couple of catches
In a sea of messaging apps, WhatsApp remains one of the most widely used, its popularity buoyed by end-to-end encryption. Meta has now added a new feature aimed at "those who are particularly privacy-conscious".
There is a new option to protect your IP address by hiding it from other WhatsApp users during calls. This is important as IP addresses can reveal quite a lot, including location. While the new call relaying privacy measures are likely to be welcomed, there are a couple of significant caveats to keep in mind.
Organizations plan to use more AI in the next few years
A new survey from Snow Software reveals that 72 percent of IT leaders believe their organization will be using more AI in the next two to three years.
The poll of 800 IT leaders from the United States, United Kingdom, Germany and Australia set out to assess how IT decision makers' priorities have shifted over the past 12 months and outline their top areas of focus as they head into the new year.

Microsoft to stop giving users Tips for Windows 11
Microsoft is far from being a stranger to killing off features in Windows, and this even holds true for the latest version of the operating system, Windows 11. It is usually the case that things that are removed are old, broken, or pose a security risk -- such as recently removed services like WebDAV -- but not always.
The latest victim of Microsoft's deprecation drive is the Tips app that has been used for years to provide users with helpful information and advice about getting the best from Windows.

Microsoft looks likely to bring AI assistant Copilot to Windows 10
Windows Copilot has been available to users of Windows 11 for a little while now, as Microsoft continues its march into the world of artificial intelligence. Now it seems that the company is looking bring the AI-powered assistant to Windows 10 as well.
This is, in some regards, a little surprising -- particularly given the age of Windows 10. But there are still over a billion Windows 10 users out there, so it makes a lot of sense for Microsoft to tap into this to extend the userbase for Copilot.

Taylor Swift is Apple Music 2023 Artist of the Year
Apple Music has crowned Taylor Swift as Artist of the Year for 2023, a testament to her unwavering popularity and the sheer volume of her streaming success. With a record-setting 65 songs on Apple Music's Global Daily Top 100 within just ten months, Swift's reach has proven more expansive than ever. Her heartfelt gratitude to fans underscores the symbiotic relationship that has fueled her stratospheric rise this year.
The significance of Swift's achievement is not just in the digital streams but also in the cultural moments she's created: from concert euphoria to the rebirth of older tracks as chart-toppers. The "Eras Tour" alone saw a 61 percent global increase in Swift's streams, solidifying her as a live performance powerhouse.

Five tips to inform your AI and data science strategy and maximize your investments
Data science and AI leaders are rushing to accelerate new technology adoption. According to Forrester, generative AI alone will see an average annual growth rate of 36 percent for the next seven years, taking 55 percent of the AI software market. The analyst firm also estimates that by 2030, $79 billion will be spent annually on specialized generative AI applications and $42 billion will be spent annually on generalized generative AI use cases.
Even if Forrester is off by a few billion dollars, moving fast is still critical to achieving success, but so is having an optimal AI strategy. Leaders must ensure that practitioners have the technology they need to innovate. At the same time, they must ensure innovation does not exceed budgets or introduce new risks.


