
Early adopters delay IoT purchases over security concerns
While people are still excited about Internet of Things technology, many are delaying buying over concerns about privacy and security.
A new survey from cyber security company F-Secure shows that 63 percent of early adopters are looking to purchase new devices, but 50 percent have delayed an IoT purchase because of security concerns.

Consumers will stop spending with businesses after a breach
New research finds that that 83 percent of consumers will stop spending with a business for several months in the immediate aftermath of a security breach or a hack.
More than a fifth (21 percent) will never return to a brand or a business post-breach, representing a significant loss of revenue, according to the study from secure payments provider PCI Pal.

Web applications leave companies vulnerable to breaches
Insecure and outdated web applications are a core source of high-profile data breaches among FT 500 global companies according to new research from web security company High-Tech Bridge.
The study reveals that abandoned, shadow and legacy web applications more or less nullify corporate cybersecurity spending and undermine compliance.

Want to find the biggest cloud security threat? Look in the mirror [Q&A]
It seems not a day goes by without a new cloud data breach making headlines. And though the victims change, the attack details remain the same. Why do organizations keep repeating the same cloud security mistakes? And how can we break free from this vicious cycle?
We spoke to Zach Malone, security engineer at security management specialist FireMon, who discusses these issues and tells us why, to identify the biggest threat to cloud security, we need to look in the mirror.

Mozilla partners with ProtonVPN to offer security-conscious Firefox users a VPN
Mozilla has announced a partnership with ProtonVPN as it explores new ways to keep people safe online.
Starting today, a select group of Firefox users in the US will see an ad for ProtonVPN encouraging them to take out a monthly subscription with the service. It's an experiment that is part of Mozilla's attempt to explore new revenue streams to help keep Firefox funded.

Thycotic launches free security toolkit for the higher education sector
Universities and colleges are uniquely attractive to cyber criminals, because a constantly changing population and the use of large numbers of BYOD machines means lots of potential vulnerabilities.
Privileged access management specialist Thycotic is releasing a free Cyber Security Toolkit for College Students and Families, aimed at providing an essential guide to help schools build an understanding of cyber best practices throughout their entire community.

How to spot a fake Twitter follower
Earlier this year we covered some research from Duo Security published into the activities of Twitter bots. The company has now followed this with a look at how fake Twitter followers operate.
Traditional fake followers are challenging to detect on an individual level since they have very little (if any) activity other than following other accounts. However, because fakes operate in groups created by the same bot owner they do tend to share characteristics.

Industrial control systems offer a soft target for attackers
Security gaps in key areas such as plain-text passwords, direct connections to the internet, and weak anti-virus protections are leaving industrial control systems vulnerable to attack according to a new report.
The study from ICS security company CyberX also shows that although the use of Windows XP has declined over the last year there are still older, unpatchable, Windows systems in slightly more than half of all industrial sites.

Password Check Required Immediately -- and more of 2018's most successful phishing subject lines
Which subject lines make a person most likely to click a link in a phishing email? Security awareness training company KnowBe4 has analyzed data from simulated phishing tests and 'in the wild' emails to find out.
The most successful lines play on user's desire to remain secure with subjects relating to password checks the most clicked. On social media, messages about tagging or new profile views are most likely to be clicked.

Free tool allows Office 365 users to test their email threat detection
Email is still one of the most common ways for attackers to target individuals or businesses, whether it’s through phishing attacks or delivering malware. Although you may have protection measures in place it can be hard to know if they’re working effectively.
Intelligence-led security company FireEye is launching a new capability that allows organizations to evaluate email threat detection efficacy with a no-charge evaluation service

The life of an ethical hacker [Q&A]
We often hear the term 'ethical hacker', but what exactly does this involve and is it something you can actually make a career out of?
We spoke to Jim O'Gorman president of online penetration testing training provider Offensive Security to find out what being an ethical hacker is all about and what skills you need if you want to become one.

Creating the next generation of cybersecurity leaders
In today’s cybersecurity landscape, the value of good cybersecurity tools is undeniable. What is more valuable are the people behind the tools -- however, the amount of open cybersecurity positions worldwide is growing year over year. Currently, there are more than 300,000 open cybersecurity roles in the U.S. alone, but by 2021, Cybersecurity Ventures expects that number will reach 3.5 million.
This gap is felt by cybersecurity leaders; in fact, a recent study found that more than 70 percent of the cybersecurity decision makers agree that their organizations do not have the staff or necessary resources to monitor all cybersecurity threats that their organizations face. With the number of cybersecurity openings growing yearly and the sophistication and frequency of cyberattacks increasing, in order to build the cybersecurity leaders of tomorrow, business leaders must turn their attention to things that they can control: investing in the right solutions and their staff.
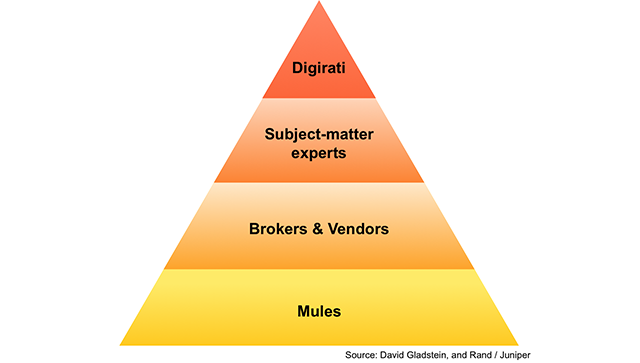
Can the infosec community ever be as well-organized as digital criminals?
Brian Gladstein, a security marketing strategist at Carbon Black, discussed the question posed in this headline at RSA Conference 2018. In his presentation entitled "Endpoint Security and the Cloud: How to Apply Predictive Analytics and Big Data," Gladstein observes that digital crime is structured like an economy consisting of several tiers. At the top is the "Digirati," a term used by Gladstein for the class of high-ranking controllers responsible for executing digital attacks. The Digirati consists of the ones who hide on the network and gather information, usage patterns, and intel. They then share this information and build upon what knowledge they’ve already gathered from other actors in the online criminal community.
Below the Digirati are the subject matter experts. Malware writers, identity collectors, and individuals who hoard zero-day vulnerabilities and other exploits sit on this level of the digital crime economy. These individuals oftentimes sell access to their goods and services to the next tier, which consists of botnet owners, cashiers, spammers, and other brokers and vendors.

Enterprise security teams struggle to balance budgets against demands
Businesses are increasingly moving more of their operations to the cloud and this leads to a greater focus on securing these workloads.
Cloud infrastructure security company Threat Stack has released a new report created by Vanson Bourne which shows 54 percent of businesses are worried that they will soon outgrow their security solutions.

Webroot launches VPN to protect Wi-Fi users
Many people rely on connecting to Wi-Fi networks when they are out and about, but using public hotspots does present a significant security risk.
The best way to protect yourself is to use a VPN and cybersecurity company Webroot is launching its own in the form of Webroot WiFi Security, to provide security and privacy for users who connect to WiFi networks using Windows, Mac, and Android operating systems.