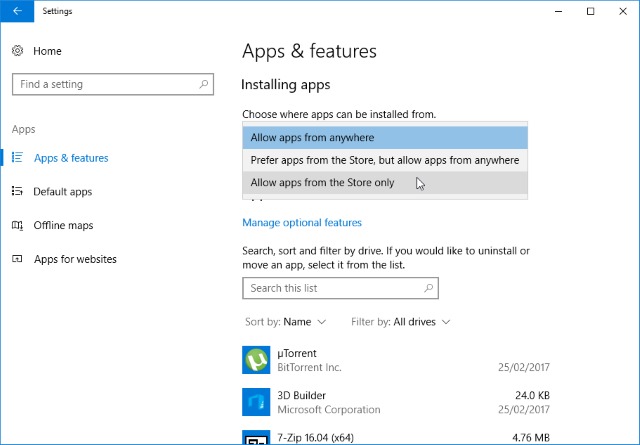
How to block the installation of non-Windows Store apps in Windows 10
If you want to keep your computer secure and clutter-free, it's important to keep an eye on what gets installed. This is fairly easy if you're the only person to use your computer, but less so if you share it with kids or other members of your household. To make it easier to lock down Windows 10 Creators Update, you can block the installation of all software that doesn't come from the Windows Store.
Why would you want to do this? Well, blocking non-Windows Store software means blocking traditional programs, and these are the ones that are more liable to be malicious or pose a security threat. Apps that have made it into the Windows Store have -- in theory -- been vetted to some degree, and are less able to wreak havoc. Here's what you need to do.
Google releases details of unpatched Internet Explorer and Microsoft Edge vulnerability
Not content with publishing details of an unpatched Windows bug, Google has now gone public with a security vulnerability in both Microsoft Edge and Internet Explorer. Going under the description of "Type confusion in HandleColumnBreakOnColumnSpanningElement", the bug has the potential to allow an attacker to execute malicious code.
The vulnerability has been assigned the code CVE-2017-0037, and details of the flaw have been published under the terms of Google's Project Zero. Microsoft was notified about the problem 90 days ago, and as the company failed to patch it Google has made the problem public.

Cloudbleed: Cloudflare leaks sensitive data, many major websites affected
Security researchers from Google's Project Zero have uncovered a critical bug in Cloudflare which allowed sensitive data -- like passwords, cookies and encryption keys -- from many hosted websites to leak online.
Patreon, Y Combinator, Medium, 4chan, Yelp, OKCupid, Zendesk, Uber and 23and Me are among the most-important affected websites. This security issue is so important that it is now being referred to as cloudbleed.
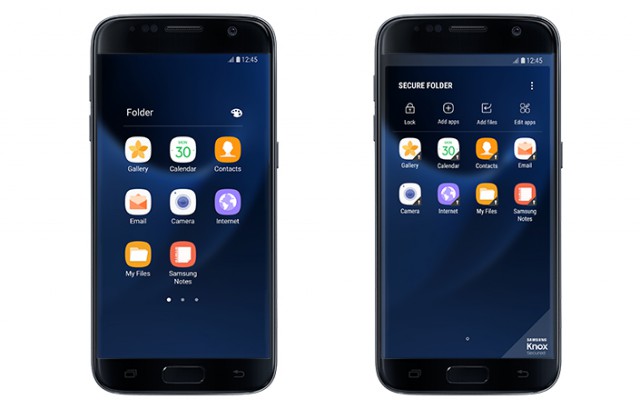
Samsung Secure Folder for Android safeguards your private data
If you want to secure your Galaxy smartphone, the first thing that you should do is set up a screen lock. But what if you want to go a bit further, and protect specific things on the device? Well, Samsung just released Secure Folder, which gives you a "private, encrypted space" to store sensitive data in.
Secure Folder is derived from Knox, the company's secure platform for business users, and can be seen as a consumer-focused iteration. It acts as a sandbox for apps and data and works with existing authentication options to keep them safe.

Dropbox releases open-source Slack bot
Dropbox is looking to tackle unauthorized access and other security incidents in the workplace with a chatbot. Called Securitybot, it that can automatically grab alerts from security monitoring tools and verify incidents with other employers.
The company says that through the use of the chatbot, which is open source, it will no longer be necessary to manually reach out to employees to verify access, every time someone enters a sensitive part of the system.

New DDoS capabilities uncovered in Necurs botnet
The Necurs botnet is one of the largest around at the moment and is principally known for sending spam including the Locky ransomware.
However, new research from BitSight's Anubis Labs has uncovered a new component being loaded in infected systems that allows it to use bots to enable proxy communications and perform DDoS attacks.

Organizations failing to address security pain points
Cyber-attacks against organizations in 2017 will continue to be as successful as they were last year, because organizations aren't addressing the pain points they had last year, a new report says.
Fujitsu's "Blind spots and security basics -- letting your guard down could cost you in 2017" report says that attacks over encrypted channels will continue to be missed, due to the lack of SSL inspection capabilities.

Google has broken SHA-1 encryption
After two years of research, Google has shown that it has successfully broken SHA-1 encryption. The company is yet to release details of how it achieved the first SHA-1 "collision", but has released a proof of concept.
In keeping with its own disclosure policy, details of how the encryption was effectively broken will be released after 90 days. In the meantime, you can take a look at two specially-crafted PDF files that have identical SHA-1 hashes but different content (the definition of a collision).

Red Hat: 'use after free' vulnerability found in Linux kernel's DCCP protocol IPV6 implementation
Red Hat Product Security has published details of an "important" security vulnerability in the Linux kernel. The IPv6 implementation of the DCCP protocol means that it is possible for a local, unprivileged user to alter kernel memory and escalate their privileges.
Known as the "use-after-free" flaw, CVE-2017-6074 affects a number of Red Hat products including Red Hat Enterprise Linux 6, Red Hat Enterprise Linux 7 and Red Hat Openshift Online v2. Mitigating factors include the requirement for a potential attacker to have access to a local account on a machine, and for IPV6 to be enabled, but it is still something that will be of concern to Linux users.

Organizations can avoid 94 percent of critical Microsoft vulnerabilities just by killing admin rights
When vulnerabilities are found in Microsoft products, collective breaths are held until the company releases security bulletins. But analysis of security issues by software manufacture Avecto shows that the overwhelming majority of these vulnerabilities can be mitigated against by simply removing administrator right from users.
Avecto CEO Mark Austin and CTO Marco Peretti say that organizations need to address the problem of "over privileged users". The duo say that this would help to avoid the security problems caused by 94 percent of critical vulnerabilities in Microsoft products. The research also found that Windows 10 had the highest proportion of vulnerabilities of any operating system.

PCs still at risk from end-of-life programs
The latest software vulnerability report from Secunia Research at Flexera Software reveals that the average US private PC user has 75 installed programs on their PC, 7.4 percent of which are no longer patched by the vendor.
More detailed analysis of the findings shows that 7.5 percent of users had unpatched Windows operating systems in the final quarter of 2016, up from 6.1 percent in Q3 of 2016 and down from 9.9 percent in Q4, 2015.

Half of 2016’s phishing attacks aimed to steal money
Almost half (47.48 percent) of all phishing attacks in 2016 were aimed at stealing victim's money, and the amount of financial phishing attacks increased by 13.14 percent according to a new report.
The study by Kaspersky Lab analyzed attacks registered in 2016 by the company's heuristic detection technologies.

Windows 10's strong security will make mobile devices a more attractive target
As enterprises move to Windows 10, and take full advantage of the advanced security features offered in the operating system and in Microsoft Edge, cyber criminals will increasingly look towards the mobile ecosystem for exploits.
This is according to Fujitsu's latest report, which believes 2017 will see an even bigger increase in attacks against the mobile world.

Kaspersky launches 'secure operating system' -- with no trace of Linux in it
Every once in a while a major software company takes us by surprise by releasing an operating system of its own. Kaspersky has done just that with its new KasperskyOS, which is designed for control systems, Internet of Things devices, and network devices. The most intriguing thing about the 14-year project? It has no Linux underpinnings.
If you want to create your own operating system, basing it on Linux is an obvious choice. The open-source kernel is tried and true, after all, and best of all it's free, so if you want a solid foundation it is a great option. But, "for different applications and purposes," Kaspersky went a different route.

Americans at risk of identity theft as they file their tax returns
As we move into the tax return season a new study reveals that attitudes to identity theft and a pattern of poor practices are leaving much of the public vulnerable.
Data security and ID theft protection company CyberScout has carried out its second annual Tax Season Risk Report and finds 58 percent of Americans are not worried about tax fraud in spite of federal reports of 787,000 confirmed identity theft returns in 2016, totaling more than $4 billion in potential fraud.