
Know the benefits of becoming a sustainable business
In business, sustainability refers to doing business without negatively impacting the environment, community, or society. Sustainability in an industry generally addresses two main categories: The effect business has on the environment and the effect business has on society.
Making environmentally conscious decisions is unavoidable for business and sustainability because it can impact the environment.

How to ensure a smooth transition as a new CTO
Beginning a CTO role can be a daunting prospect, especially if you’re completely new to the company. There are lots of plates to spin, people to meet and ways of working to get used to, so it’s crucial you’re on top of your game from the outset.
In effect, those first few months in the position are about learning as much as possible in a short space of time. This learning process should encompass all elements of the business, including the company itself, its culture and your colleagues. Below, we have outlined six key areas that new CTOs can focus on, to make your transition into the role as smooth as possible.
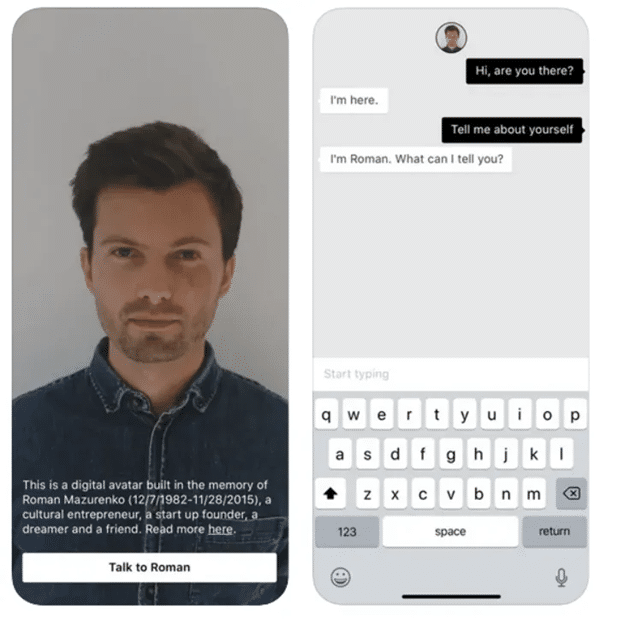
Digital afterlife: A chance to live forever or never rest in peace?
Have you ever thought about what happens after your physical shell expires? What legacy will you leave and what becomes of it with time? We can give our tangible belongings to friends and family. If the work is copyrighted, the protection will usually extend well beyond the author’s lifespan.
The law has, however, yet to catch up with the times as we also share, store and use tons of information online. That encompasses our digital identity, which is often left unattended after death, lingering at the digital graveyard at the mercy of tech giants.

Should you invest in the tech industry in a recession?
What makes a good investment during a recession? Is investing in the tech industry safe when the economy is low? Read on to learn how to use what previous recessions have taught us to choose your tech investments wisely.
If we want to know how the tech industry stands to weather the future, the first step is to look to the past. Let’s take a look at the last three U.S. recessions and their effects.

Three steps to making a cloud smart investment
Today, many businesses are transitioning to cloud to modernize environments, improve system reliability, advance their digital business initiatives, and support the new realities compelled by the pandemic, such as working from home. According to Gartner, "cloud is the powerhouse that drives today’s digital organizations". In fact, its growth has been little short of meteoric, with a staggering $494.7 billion spend and 20.4 Percent predicted growth in 2022.
Cloud is driving increased security, increased performance, better customer experience and better value for money in tech investment, and it continues to be widely adopted by global business. But organizations are becoming more prudent and strategic in their cloud investments, centering desired business and technical outcomes when selecting the cloud model that best fits their individual needs.

3 major risks enterprises face in the era of digital interconnectivity
Today, enterprise-scale companies are more interconnected than ever. People, applications, servers, networks, and devices in different departments and even in different parts of the world are constantly exchanging information in both the public and private cloud. That’s not a bad thing. In fact, most organizations strive for this kind of silo-less interconnectivity. Desirable as it may be, however, it’s not risk-free.
There are cybercriminals ready to exploit any vulnerability in an organization’s digital defences. That much should be obvious from the 60 000-plus reports of fraud and cybercrime that came from UK businesses in 2021. It’s critical, therefore, that organizations do everything possible to understand and mitigate those risks.

Amazon's robot workforce could doom the American worker
The year is 2030. Most humans have been replaced by machines in U.S. warehouses and factories. Millions of Americans are out of work and struggling to find jobs as robots pack, sort, ship, and carry out the myriad duties that just ten years ago were the purview of living, breathing workers. There are little job prospects in sight for these workers as automation has completely taken over numerous industries.
As fictitious as this sounds, it is not a scene out of a science-fiction novel, but instead a scenario that could occur in the very near future. Take, for example, Amazon’s recent launch of Proteus -- the company’s first fully autonomous mobile robot. This should signal that much of the company’s workforce faces extinction by automation in the coming years.

The risk-based approach to vulnerability patching: How to do it right
As businesses continue to produce and switch over to digital products, we see more cyberattacks and software flaws exploited for nefarious purposes. The number of small flaws in software that cause major issues can quickly get out of hand. Machine learning has produced a process known as risk-based vulnerability patching to help avoid this issue.
This article will discuss what a risk-based approach is, the patching processes, solutions to negate the risk of each issue, and a management plan for every part of the process. Sections will be broken down by the type of software and each part of the risk management process.

Taking the risk-based approach to vulnerability patching
As one of the most effective ways to prevent attacks on IT assets, it is universally acknowledged and known that patching vulnerabilities is a critical process. But as the volume of vulnerabilities discovered in the tools we use continues to proliferate -- and the speed at which they are being weaponized increases -- patching is becoming a complex and difficult task for security teams. During the 2021 calendar year alone, more than 20,000 individual vulnerabilities were discovered and announced, and by May 2022, more than 10,000 issues had been released. The number of vulnerabilities being discovered and disclosed is not slowing down, it is accelerating.
While the security community’s ability and attention towards discovering vulnerabilities has matured, the scale of these issues has - in tandem - become overwhelming. So what can organizations do to stay afloat in today’s "sink-or-swim" threat landscape?

Disaster recovery planning: A successful framework for strategy and execution
The rise in cyber incidents is set to continue on its meteoric trajectory over the next decade. Ransomware attacks on a business, consumer, or a device are anticipated to take place every two seconds by 2031 -- a worrying escalation from every 11 seconds in 2021. And by 2025, damages are projected to reach a staggering $15 trillion annually, up from $3 trillion in 2015, according to Cybersecurity Ventures.
At the same time, users demand better performance and user experience year-after-year, and the subsequently increased threat landscape poses real challenges in connectivity and data security. 'Insider threat' also poses a considerable risk, with 80 percent of breaches involving privileged credentials misuse or abuse and malicious insider activity from recent employees.

AIOps needs a new (customer-focused) approach
IT infrastructure has become incredibly complicated -- intensified by the investment in digital transformations encouraged by the pandemic. One of the unintended consequences? IT teams and incident responders are stressed, and stretched farther than ever. PagerDuty’s The State of Digital Operations lays out the increased burden on these teams, the results in terms of burnout, and the impact having a more mature digital operations can have on minimizing that stress.
AIOps is an essential component to any mature digital organization, and it’s clear a new approach is needed. The sheer volume of IT events, from changes, warnings and incidents, to tickets for more routine activity are increasing 70 percent year-on-year. At a moment when increases in budgets won’t keep pace with the explosion of incidents or the complexity of IT infrastructure (if the budgets aren’t being reduced outright), leveraging AIOps to serve teams and customers is critical.

Your IT systems touch multiple networks -- what's your cyber hygiene plan?
The world is becoming more connected via the use of cloud computing services and Internet of Things (IoT) devices. Over the last decade, we have watched cybercrimes skyrocket before our very eyes. Corporations today cannot afford to rely on basic firewalls and antivirus software to ensure data is protected. It is essential to create a more powerful cybersecurity ecosystem.
How big is the threat against data? First, take a look at how much data we are talking about here. By the year 2025, we can expect there to be 175 zettabytes of data across the internet and networked computer systems. Think streaming video, dating apps, your private healthcare information, banking data, social media posts, and messages. The list can go on.

Why merchants don't need to buy fraud insurance to cover everything
The discipline of fraud prevention has changed dramatically over the past five years and continues to evolve rapidly. Consequently, former truths about fraud prevention are increasingly becoming outdated myths. Legacy vendors propagate these myths to maintain relevance, but industry leaders understand the distinction and are moving forward.
In this article, the common myth we’ll tackle is that a merchant should buy fraud insurance to cover everything -- this is typically touted in the market as a 'chargeback guarantee.' On the surface, the simplicity is appealing; the vendor is claiming to solve merchants’ fraud problems by taking liability for chargebacks, returns abuse, Item Not Received abuse, and potentially more. But the statement is very much a myth for, at the very least, five important reasons:

Key considerations prior to adopting SaaS
As organizations have adapted to the evolving digital landscape, there has been a meteoric rise in popularity of Software-as-a-Service (SaaS) as a business model. This is best illustrated by Gartner’s predicted increase in worldwide SaaS end-user spending value to reach $176.6 billion in 2022. The analyst firm further predicts worldwide public cloud spending to reach almost $500 billion by the end of 2022.
Affordability and flexibility are the principal drivers for businesses to move their data environment and applications from their own infrastructure to centrally located services on a remote cloud network. However, trusting arguably their most important asset -- their data -- with an outside entity often raises some concerns around data governance, compliance, costs, and beyond. Before making an investment, it’s sensible to carry out a self-assessment process on the basis of ten most commonly asked questions:

The benefits of robotics: Which industries are reaping the rewards?
Industrial robots are taking over. Well, they’re becoming much more common in the workplace. In fact, according to a report by the International Federation of Robotics, the number of robots in factories has almost doubled in recent years.
The 2021 World Robot Report shows that the global number of robots per 10,000 employees has risen from 66 to 126 between 2015–2020. So which sectors are reaping the rewards? Here, we’ll explore just this, shining a light on industries benefiting the most from robotics.

