
Digital transformation with four underutilized cloud-based capabilities
Making the most productive use of an organization’s digital resources is a vital ingredient for success in today’s ultra-competitive business landscape. Companies are challenged to extract the maximum value from their data assets when using exclusively in-house computing solutions.
This article will discuss cloud-based solutions and methods businesses can adopt to enhance their organization’s digital transformation. Failure to recognize and act on the potential benefits of these cloud technologies can leave a company struggling to keep up with more proactive market rivals.

What is the future of cryptocurrency regulation?
The cryptocurrency industry rose to prominence in the United States in 2014. Since then, people have debated whether the U.S. government should get involved in regulating the new form of commerce and to what extent.
On one hand, Congress doesn’t want to stifle the innovation resulting from the burgeoning crypto industry. On the other, regulation would increase safety and encourage investors to feel more confident in cryptocurrency. The future of crypto is up in the air, but professionals agree that any regulation would have to be done delicately.

Business intelligence to support a post-pandemic mindset
The 'management versus employee' battle on WFH continues -- but have managers recognized why hybrid working has become such a problem? Without face-to-face interaction, remote workers have far less trust in the information provided by distant colleagues -- or distant business partners/ suppliers/ customers. And that is leading to a breakdown in relationships across the board.
Furthermore, the pandemic has exacerbated differences in working attitudes: for every ambitious individual wanting to make a fast impact on the business before moving on to the next challenge, there is another taking the quiet quitting approach, coasting along doing just enough to get by. How do the former engage the latter or monitor their progress to ensure key tasks are done -- especially when they have zero trust in the business information currently available? The stand-off will be both inevitable and painful -- especially given the continued challenge to recruit talent.
Parallels Desktop 18 rolls out more compatibility, performance improvements
It’s that time of year again when a major new version of Parallels Desktop hits the stores with the promise of improved compatibility and performance. This time around, Parallels Desktop 18.0 promises to maximize the use of Apple’s M1 Ultra chip with the potential to deliver up to 96 percent faster Windows 11 VMs on a Mac Studio.
In addition to unlocking the extra power of the M1 Ultra chip -- which will allow users to assign additional resources to their virtual machines to deliver those performance improvements, Parallels Desktop 18 also promises full support for Apple’s ProMotion display, allowing for automatic refresh rate changes.

How to create a faster feedback loop through progressive deployment
Using continuous deployment and progressive deployment for software updates accelerate feedback loops to improve development speed and software quality, giving your company a competitive advantage. In our fast-paced world, early and frequent software deployments increase business performance and revenue. Automated deployments enable faster and more reliable updates.
Companies that have generated higher release rates outpaced growth in companies that have not, achieving four to five times faster revenue growth and 20 percent higher operating returns. But those software updates must be high-quality and satisfy users’ needs. An increasing number of customers aren’t giving brands a second chance -- 32 percent of all U.S. customers would stop doing business with a brand they loved after one bad experience. In addition, reliable software is imperative because outages and downtime caused by failed deployments can cost companies anywhere between $100,000 to $5 million per hour.

Cybercrime doesn't take vacation: How to work securely this summer season
As global travel restrictions continue to ease this summer, many will wander to new destinations. Recent research anticipates that 208 million American adults (80.84 percent) plan to travel this summer with more than 20 percent of those planning to travel internationally. While this is a positive forecast for the travel and hospitality sector, for cybersecurity, it presents a host of potential risks. Insecure WiFi connections and personal device usage, to name a few.
As malicious activity proliferates and cybercriminals become more discrete and persistent with their attack methods, organizations and their employees must be vigilant at all times, unfortunately even when on vacation. Simply checking company emails on a personal device while connected to public WiFi at a café or airport could have massive repercussions for an organization. Employees must always take precautions, as cybercriminals will be looking to exploit organizations during employee downtime. While it is best to completely avoid bringing your corporate devices on vacation, fortunately, there are measures that we can all take to reduce our risk of falling victim to an attack while working from unfamiliar locations.

Reprogramming the enterprise: How IT teams aim to keep pace with demand
Over the past two decades, the role of IT in the enterprise has shifted from peripheral to strategic. Businesses are now digital-first and technology plays an integral role in driving innovation, differentiation, and sharpening the competitive edge. The past two years have not only shown us what digital channels are capable of, it has placed them front-and-center in the battle for customer engagement. This has forced yet more rapid evolution in enterprises. They are striving to build teams that can respond to the demand for seamless, multi-channel customer experience while fending off competition from disruptive digital native start-ups.
Recently we conducted research among senior IT decision-makers to uncover the key areas of focus, the challenges, and how they are writing new rules for the digital era. The results show how IT teams are effectively reprogramming the enterprise and drawing on new technologies as they seek to deliver outstanding digital experiences with reassuring security levels, while also wrestling with the challenges of talent shortages in the industry.

Apple's rumored VR headset will be huge for the enterprise: Here's what IT needs to be thinking about now
After many years of speculation, Apple’s entrance into the VR/AR market is finally imminent. CEO Tim Cook hinted in an interview last month that he is "incredibly excited about AR" and to "stay tuned" to see what Apple has to offer. The Board has allegedly tested a headset out. The latest rumors suggest that Apple will unveil something by January 2023.
Whenever it happens, Apple releasing some sort of VR/AR device will be an absolute game changer for the industry. Apple moves markets. Its technology is always excellent. It knows how to drive mass appeal. Apple’s headset will, without a doubt, help push XR to widespread adoption, and maybe not in ways you’d expect. When people think of Apple products, their mind typically goes to consumer technology -- but it’s actually the enterprise that will likely come first in reaping the benefits of this new headset.

How to improve collaboration between developers and product owners
Technical teams sometimes have difficulties getting along, as the scope of work across a project can be so diverse. In any profession, if a team member doesn’t understand the value of what their colleague brings to the group, this can cause conflict, so close and frequent communication is key.
Research from Harvard Business Review supports this philosophy, with high-performing teams reaching out to each other ten times per day, compared to an average of six. This shows how regular check-ins strengthen bonds within the group, which subsequently reduces errors and disagreements as everyone has a clear idea about each person’s role in the team.

Why are enterprises overspending on the cloud?
Cloud services have grown exponentially in recent years, with businesses embracing the solutions to provide scalability, agility, and access to new applications. Most organizations have already embraced the cloud or are planning to do so -- and the increased movement of infrastructure to the cloud is described as “inevitable” by 95 percent of enterprises polled recently.
Despite this momentum, enterprises are growing frustrated with some limitations of cloud services and are starting to wonder if more can be achieved. Cloud is not always meeting businesses’ expectations, with inadequate management tools, issues with accessing data, and inflexible pricing plans often resulting in dissatisfied customers.

Small businesses often left hanging by ransomware scourge
Ransomware is hitting small businesses hard. But most of the legislation, regulations, and headlines focus on large businesses. The math is simple -- large businesses impact many end-users, and they have lots of money to pay lobbyists, so they wind up stealing the show when it comes to ransomware. But what about the local print shop, deli, or accounting office? Even though small businesses are suffering from ransomware 70 percent more often than large businesses (according to the Cyber Edge 2022 Cyberthreat Report), government regulations haven’t changed to accommodate them.
The U.S. Justice Department recently released a strategic plan that will investigate 65 percent of all reported ransomware attacks by 2023, but there are a few problems with this. First, the Justice Department -- or anyone else for that matter -- has no accurate accounting of how many attacks are actually occurring. Because so many attacks go unreported, there isn’t a way to certify how many ransomware attacks happen each year. Second, even if we assign credibility to 65 percent of ransomware cases, how can we or the government use this information effectively to reduce attacks? Finally, what about unreported ransomware attacks (which account for most of the attacks) on 44 percent of the U.S.’s economy: small businesses?

Four ways IT leaders can disrupt public safety with new tech
Most industries, from education to manufacturing, are inundated with technical solutions. But there's one space you'd be surprised is still firmly in the 20th century: public safety. That's right, your cops and EMTs are running software that was cutting edge in the early 2000s. This means a few things for the IT industry.
First, it means these groups are facing a massive and necessary upgrade cycle. That translates into a significant opportunity for those interested in the first responder market.
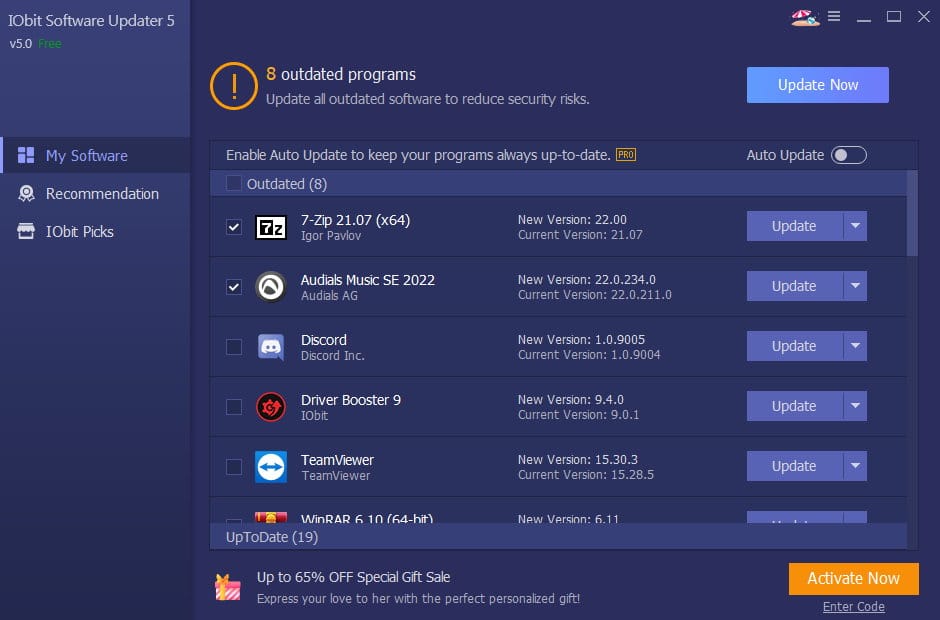
IObit Software Updater 5 keeps your apps updated to boost system security
It is very easy to keep Windows up to date -- so easy, in fact, that you hardly need to do anything. Just make sure that the Automatic Updates feature of Windows Update is enabled, and everything will happen in the background. IObit Software Updater does much the same for the apps you have installed as well.
While there are some apps that will update automatically -- including, but not limited to, those installed from the Microsoft Store -- it is certainly not the case for all software. And this is where IObit Software Updater can help, ensuring that all of the software you have installed is up to date, so you not only benefit from the latest features and options, but also the highest level of security. IObit Software Updater 5.0 is now here, complete with support for scores of additional applications.

How to use SIGKILL to rapidly terminate containers in Kubernetes
Originating from Linux, which uses a Unix operating system, SIGKILL is a common command that developers use to terminate absolutely any process. Most commonly, if anything needs to be shut down immediately as it's causing damage to the system itself, then SIGKILL is the go-to signal to use.
Alongside Linux, SIGKILL has also found itself into any developer platform that manages container systems, with the most popular example of this being Kubernetes. As one of the most drastic signals that you can execute, SIGKILL will instantly terminate a process, without giving the system the opportunity to block or ignore the signal. With this, absolutely any processes that are connected to the process you’ve killed will also terminate.

Cyber insurance may be cyberficial, but…
Insurance might be one of the least liked, but most valued purchases within a business when you need to use it. In previous decades, it was needed against fire, theft, and other tangible threats to a business, yet as cyber-attacks are becoming an inevitable, frequent occurrence, the demand for cyber insurance is at an all-time high.
However, qualifying for cyber insurance coverage is easier said than done. Businesses not only have to manage the soaring cost of premiums, but also meet a long list of complex criteria that deems their current security strategy and implementation eligible for financial protection.

