
A zero-trust strategy starts with identity
At this point in the history of cybersecurity, the concept of a network perimeter seems almost quaint. The perimeter was like a moat or castle wall designed to keep the bad guys out. But the days of employees and all their digital tools residing within an isolated secure area are long gone.
Today, the walls have crumbled, and the moat has dried up. Now we live in a world where people can and do work from anywhere. And they need access to resources that may be located on premises, in the cloud, or even in multiple clouds. The dramatic changes in how people work mean you can’t use location to determine who can and can’t be trusted. Today’s new demands require a new security model. And that model has a name, zero trust.

The role of IT is changing: Here's how enterprises need to adjust
The way we work has transformed. Increased digitalization, hybrid and fully remote work styles, and the integration of new and emerging technologies are all individual challenges in themselves -- but now, organizations and business leaders are expected to adapt to these changes simultaneously or risk falling behind.
This presents many issues for IT departments. The normalization of remote and hybrid teams and competitive industry pressures are major contributing factors to the increasingly prominent role IT needs to have in strategic decision-making.

Webchats: Will growth continue in a post-pandemic world?
Keeping communication open with customers is an important part of any business process, and we’ve seen a lot of change in how we do it. UK businesses are growing fast, and so are the ways they react to customer service inquiries, with efficiency and ease front of mind.
With virtual customer demand heightened even more during the COVID-19 pandemic, live chats and chatbots have become something businesses value for their communication. Chatbots especially have had an emphasis placed on their value, being considered forward-thinking.

How to innovate faster with API management: Why API utilization must improve to meet transformation demands
There is an urgent need to make application programming interfaces (APIs) efficient and utilized more effectively. This need is being driven by the rapidly increased rate of digitization that customers and business lines are demanding from CIOs and CTOs. APIs are a powerful tool that can be employed to deliver competitive advantage and market differentiation, the two biggest demands being placed on the technology team.
The Covid-19 pandemic has accelerated the digitization of society and, therefore, vertical markets. In order to remain competitive, organizations have increased the pace at which they are digitizing their business processes, which had begun prior to 2020 but sped up significantly in response to the pandemic. Management consultancy McKinsey reports that businesses with high-performance technology teams have achieved market differentiation. Technology in these organizations creates revenue and allows the business to adapt to market changes. Three-quarters of organizations with high-performance technology teams told McKinsey that digital transformation projects had achieved cost reduction and improvements in the employee experience and two-thirds of surveyed businesses had increased revenue from existing channels; half had created new revenue streams -- typically digital channels.

The three AI technologies powering checkout-free retail
Checkout-free shopping is revolutionizing the retail space, cutting down on time wasted in line and improving customer experience while shopping. Though the idea of checkout-free technology powering your shopping trips may seem like a far-off technology, it actually utilizes three established technological components that work together to provide a smooth and frictionless shopping experience.
Each of these technologies, deep learning, sensor fusion, and computer vision, work synergistically to make futuristic-seeming technology part of our everyday lives.

RPA is not a silver bullet: Why no-code holds the key to digital transformation success
If the UK’s businesses didn’t need to modernize before the pandemic, they certainly do now. The existential crisis many were plunged into over the past two years has reinforced the resolve of boardrooms everywhere that digital transformation is the future. When deployed effectively, it helps to deliver the agility that every business craves, whilst driving the operational efficiencies and productivity gains essential to survival in a period of high inflation and rising costs.
In this context, robotic process automation (RPA) can be a useful tool. But when deployed the wrong way, or in isolation, it may actually end up worsening legacy dependencies rather than alleviating them. Instead, organizations need to think about the bigger picture -- by bringing together apps, automation and extensible integration in a single no-code platform. That’s the best way to achieve modernization at a pace that fits the business.

The evolution of identity-based fraud: Why ATO attacks are at the top of the list
Digital identity is the new currency, and adversaries are chasing wealth. Research shows that 61 percent of data breaches are the result of compromised credentials. This is a common fraudster tactic, whereby using legitimate credentials allows them to avoid detection as they gather intelligence and stolen data that will allow them to undertake further fraudulent transactions.
Fundamental to the defense of systems is access control, but it has its limits. Attackers are continuously trying to circumnavigate these systems to access accounts, with login and payment flows frequently targeted. This is why many organizations have invested in anti-fraud technologies to detect and mitigate against such attacks.

Why do we continue to rely on the 'weakest link' to protect our organizations' email?
Email security continues to be a top concern of organizations, with 94 percent of all cyber attacks being delivered through email. As the most frequently used communication channel across all industries -- no wonder threat actors love exploiting it!
The conventional approach to email security is failing. Our latest research found that an average of 75 malicious messages per 100 mailboxes slip past traditional email security filters every month. Consequently, organizations put employees through countless hours of security training with hopes they spot and report these threats to security operations centers. The so-called Human Firewall.

Drawing clearer insights from the cloud
Many companies are finding an outsized return on their technology investment in a familiar place: their data. That's because the increasing sophistication of cloud analytics is helping more companies unlock value from their information. It’s a trend that’s pushing revenue in the big data and business analytics sector to nearly $275 billion in 2022, according to Statista.
While that number is impressive, the return on investment to organizations that leverage cloud analytics correctly is incalculably greater. Properly specified and executed, cloud analytics platforms can gather, process and analyze enormous quantities of data with ever-increasing speed and efficiency, helping organizations gather in-depth insights on every aspect of their operations.

Automation in cybersecurity: Overcoming barriers
"Automation" has become a buzzword in cybersecurity circles. That is not surprising in an environment where security specialists are in short supply and under intense pressure to defend the business against a huge variety of threats from innumerable different sources. Using technology to do at least some of the work seems like a no-brainer. Nevertheless, it seems that organizations are finding it hard to get the right approach to cybersecurity automation.
Threat Quotient conducted research last year that found resources, time and a lack of trust in outcomes are preventing companies from realizing the benefits of automation. In a recent webinar, myself, Nabil Adouani, CEO of Strange Bee and co-founder of The Hive Project, and our Global VP of Threat Intelligence Engineering Chris Jacobs discussed the current state of automation, the expectations around what automation can actually achieve, and what this means for implementation in the real world.

Biggest issue for manufacturers: Matching the selling approach to customer demands
Through every industrial revolution, from 18th-century coal and steam to today’s 21st-century digital cloud, manufacturers have adapted their operations to the modern technological standard. Today, with e-commerce rapidly transforming how consumers shop, manufacturers face an urgent need to shift their traditional sales strategy and services to meet rising expectations for a seamless buying experience -- especially for complex enterprise products.
Sales teams have addressed this pressure for the past decade with popular configure price quote (CPQ) platforms. However, the more options and buying channels customers seek and companies' products fulfill, the more burdens CPQ software faces in connecting these complex buying cycles. To improve time to market, sell solutions more effectively and gain competitive advantages through customized selling experiences, a significant upgrade in CPQ technology is needed to mesh businesses' and customers’ multiple needs.
Standards change
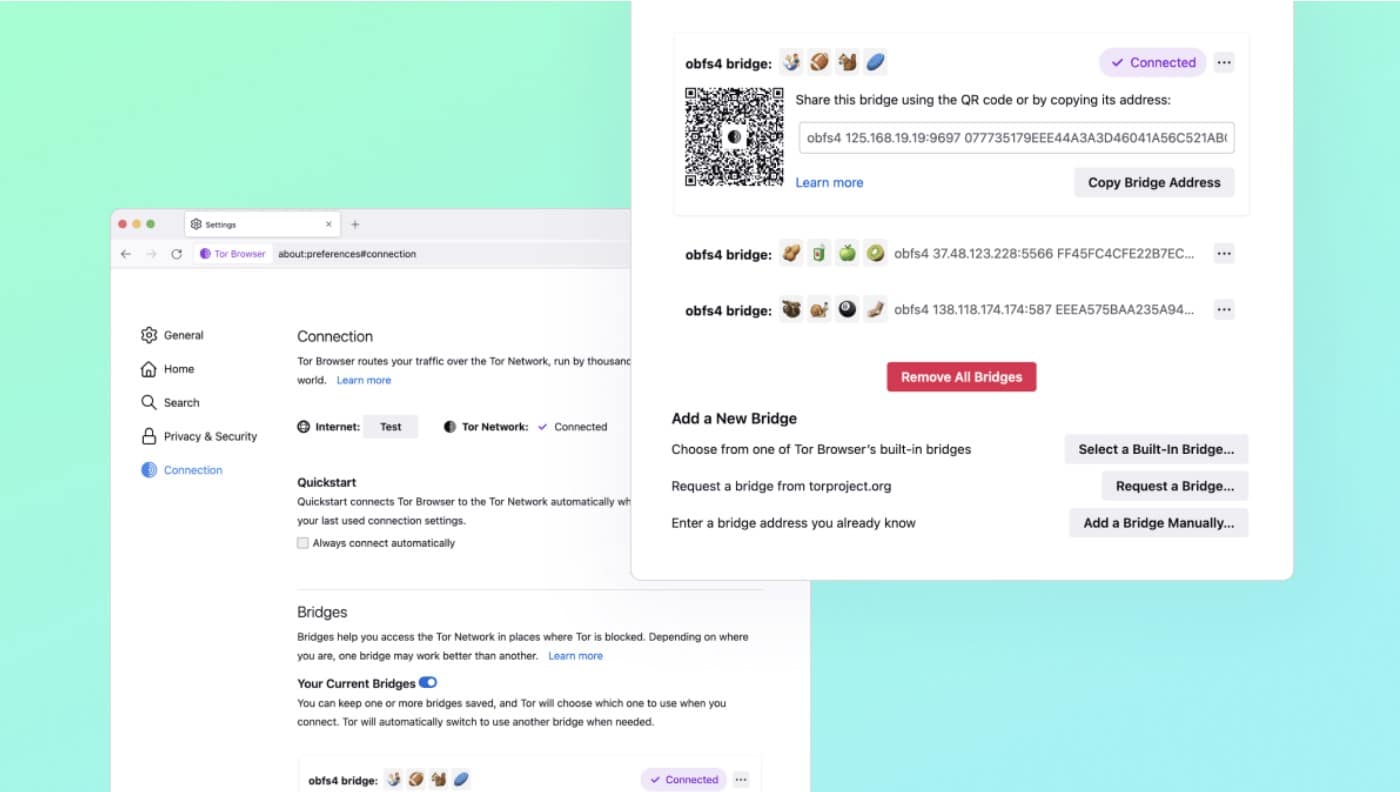
Tor Browser 11.5 is here with HTTPS-Only Mode by default and Automatic censorship circumvention
For anyone concerned about privacy and security online, Tor Browser is an extremely important alternative to mainstream browsers. Designed to help keep users anonymous and to bypass restrictions put in place by governments, version 11.5 has landed complete with even more powerful options.
Over the years, it has become easier and easier to use Tor Browser, with complex configuration options being made available to the average user without the need for special knowledge. With the release of version 11.5 of the software, things have been made even easier thanks to the introduction of automatic censorship detection and circumvention with the new Connection Assist feature.

Why is the public sector a prime target for cybercriminals?
According to a report by the UK’s National Cyber Security Centre, almost half of all recorded UK cyber incidents between September 2020 and August 2021 targeted the public sector. Public sector cybersecurity is being put to the test and it’s imperative that public sector organizations properly protect the sensitive data that is in their possession.
Back in October 2020, Hackney Borough Council in London suffered a serious ransomware attack which took many of its services and IT systems offline. The attack cost the council millions of pounds and today, more than 18 months later, data is still missing across many services. In February 2022, the Information Commissioner’s Office ordered Hackney Borough Council to disclose information regarding what cybersecurity training its staff had received prior to the attack, when they were required to work from home due to the Covid-19 pandemic.

SQL Server: Recovering operations after a disaster
Datacenters disappear. Not often, but it happens. Hurricane Sandy in 2012 swallowed whole datacenters in Lower Manhattan. Hurricanes Irma and Maria wiped out virtually all the datacenters in Puerto Rico in 2017. Cloud datacenters are not immune, either. The Azure Central Region outage of 2018 occurred after a lightning strike queued up a sequence of automated responses that failed in a spectacularly Rube Goldberg-like manner and proceeded to take multiple Azure availability zones offline for the better part of a day.
Sometimes it’s possible to anticipate the arrival of a disaster; other times, the disaster arrives without warning. Either way, the production infrastructure your organization depends on is going to be offline for some time. That does not, however, mean that your operations must go offline. It means that you need to have a disaster recovery (DR) plan in place that can provide an alternative means of keeping your operations running when your primary infrastructure is out of commission.

Top tips for investors looking to navigate the current crypto winter
The crypto market has experienced a lot of turbulence in 2022 -- and we’re barely over the halfway mark. From Luna’s extraordinary fall from grace to Bitcoin dipping below the $20,000 mark for the first time since late 2020 -- investors have been riding a financial rollercoaster in the past few months.
Despite the doom and gloom outlook of many, confidence remains amongst investors as we head into a 'crypto winter'. Latest research from Bank of America, which included findings from 160 of its clients -- indicates that blockchain technology and the digital asset ecosystem are here to stay, and investors aren’t deterred by the state of the market. Unsurprisingly, as a result, the bank’s leadership remains optimistic for mainstream digital asset adoption in the future.

