Improving remediation in practice -- five ways get ahead on fixes
Remediating security issues and potential software vulnerabilities is one of the fastest ways to improve security and prevent attacks. It’s a standard process for security teams, and it should make the job easier for everyone involved. Yet many of the security issues that we see exploited remain known software vulnerabilities -- in Qualys' Top 20 Security Vulnerability Research this year, the top five most common exploits include a privilege escalation issue in the Zerologon protocol, remote code execution (RCE) problems in Microsoft Office and Wordpad from 2017 and even an RCE with Microsoft Windows Common Controls from 2012. These issues still exist, and have been targeted by threat actors this year.
So why are these old problems still present in production systems years after patches have been released, and why have they not been fixed? What is holding IT teams back around this backlog of vulnerabilities, and how can teams improve their processes to get ahead of these problems in future?

TEAMGROUP unveils T-CREATE MASTER DDR5 OC R-DIMM RAM
In an era where the need for high-performance computing is ever-present, T-CREATE, a dedicated sub-brand of the renowned memory provider TEAMGROUP, unveils its latest offering -- the T-CREATE MASTER DDR5 OC R-DIMM. This overclocking DDR5 ECC Registered DIMM memory is tailored for workstations and servers.
The T-CREATE MASTER series is designed for professionals who grapple with large-scale projects, data analytics, and multiple specialized applications. The newly launched MASTER DDR5 OC R-DIMM stands out with its one-piece heat spreader, replete with ventilation holes, ensuring efficient heat dissipation courtesy of its thermally conductive silicone. And with on-die ECC, professionals can trust in its stable performance.
Best Windows apps this week
Five-hundred-and-sixty-one in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
The fourth Moment update for Windows 11 will be released alongside the non-security updates preview. This is not the Windows 11 version 23H2 feature update, which will be released later this year according to Microsoft.

The rise in mobile device security threats and the growing attack surface [Q&A]
Both government agencies and corporations are being tasked with developing strategies for protecting mobile devices from an increasing wave of attacks. CISOs and business leaders are asking themselves not only how they can use mobile devices to make employees more productive, but also how to realize the full potential of a mobile-powered business.
As leaders execute their mobile-powered businesses, they will also need to parallel these initiatives with mobile-first security strategies to address the fast-growing attack surfaces that bad actors are increasingly jumping on. We spoke to Shridhar Mittal, CEO of Zimperium to discover more.
Microsoft is adding even more recommended content to the Start menu in Windows 11
Over the years, the Start menu has evolved from a handy place to house shortcuts to apps and system settings into the slightly chaotic mess users are now presented with in Windows 11. The Windows 11 Start menu is still home to shortcuts -- and more -- but Microsoft has taken a different approach when compared to previous versions of the operating system.
One of the more controversial aspects is the Recommended section. This is used for various things, from highlighting recently installed apps to, more divisively, advertising apps Microsoft would like you to install. And now the company is experimenting with adding even more recommended content.

VIZIO kicks off Football Season with affordable Quantum 4K QLED Smart TV
Just in time for the 2023-2024 football season, VIZIO has launched a new television. Say hello to the Quantum 4K QLED Smart TV, a high-end yet incredibly affordable television that is set to redefine the way we watch and play. And guess what? It's available today in 65" (M65Q6-L4) and 75" (M75Q6-L4) sizes.
When it comes to picture quality, the Quantum 4K QLED Smart TV is nothing short of breathtaking. We're talking over 1 billion shades thanks to Quantum Color, brighter brights, wider viewing angles, and crisper contrasts. Whether you're cheering for your favorite team or in the middle of a heated game of Madden, the Quantum's visual brilliance will make every moment pop.
Windows 11.2 is the Microsoft operating system you want, but can't have
Microsoft today announced its upcoming huge update to Windows 11, with 150 new features, including -- naturally! -- Copilot, its AI assistant, which is going to be everywhere this fall.
Not everyone wants AI invading their operating system, however. Some people would just be happy with a version of Windows 11 that works and offers a decent selection of powerful features. Those people, would prefer Windows 11.2.
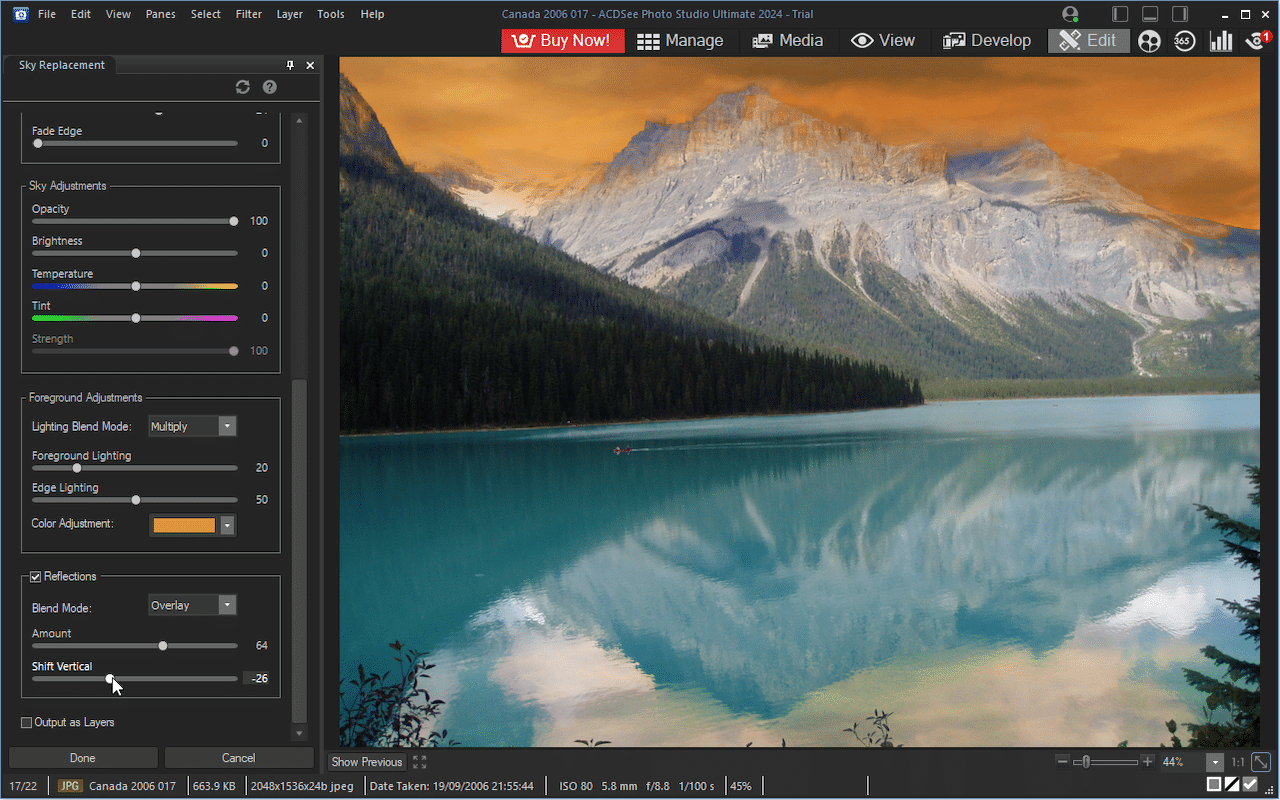
ACDSee Photo Studio 2024 celebrates 30th anniversary with new AI-powered features
Canadian digital editing and management developer ACD Systems has celebrated its 30th anniversary with the release of ACDSee Photo Studio Home 2024 and its bigger siblings, ACDSee Photo Studio Professional 2024 and ACDSee Photo Studio Ultimate 2024.
The company’s flagship product comes with the twin promise of new AI-powered features and what it dubs "significant" improvements.

Microsoft's massive Windows 11 update, featuring Copilot AI, begins rolling out on September 26th!
Although today's big Microsoft event was mostly supposed to focus on new Surface devices, the company devoted a lot of time to AI, which shouldn’t come as much of a surprise to anyone.
Copilot, Microsoft’s AI-powered companion, is coming to pretty much everywhere, including Windows 11, Bing, Edge, and Microsoft 365 Copilot. For Windows 11 users, that is huge news, and the feature is set to arrive from next week.

Microsoft unveils four new Surface devices
Today, at its hardware event, Microsoft took the wraps off four brand-new Surface devices aimed at end users and IT professionals.
According to Nancie Gaskill, General Manager, Surface, these new products "have been redesigned to reflect our longstanding commitment to integrating the voice of commercial customers" while also "supporting the needs of IT professionals to deploy, manage and support these devices at scale." These are the four new devices that were announced:

Business leaders worry more about ransomware than the economy
According to a new survey from Censuswide for Veeam Software, UK business leaders rate ransomware as a more significant threat to their organization (43 percent) than the economic crisis (41 percent), skills shortages (34 percent), political uncertainty (31 percent), and Brexit (30 percent).
The survey 100 directors of UK companies with over 500 employees who had suffered a ransomware attack in the past 18 months finds 61 percent are anxious about the prospect of another attack.

63 percent of IT workers are worried AI will take their jobs
While many IT workers see the productivity benefits of AI, 56 percent believe it benefits employers more than employees. Additionally, 63 percent are concerned generative AI tools might take their job in the next five years compared to 44 percent of general office workers.
These are some of the findings of a new report from Ivanti. It also looks and digital experience (DEX) and finds 58 percent still prefer dealing with a human rather than a chatbot.

Countering the rise of AI criminals
As generative AI tools continue to expand, new doors are being opened for fraudsters to exploit weaknesses. Have you experimented with generative AI tools like ChatGPT yet? From beating writer’s block to composing ad copy, creating travel itineraries, and kickstarting code snippets, there’s something for everyone. Unfortunately, "everyone" includes criminals.
Cybercriminals are early adopters. If there’s a shiny new technology to try, you can bet that crooks will explore how to use it to commit crimes. The earlier they can exploit this technology, the better -- this will give them a head start on defenses being put in place to block their nefarious activities. If tech helps boost the scale or sophistication of criminal attacks, it’s extra attractive. It’s no wonder cybercriminals have been loving tools like ChatGPT.

Get 'Customizing Microsoft Teams' (worth $27.99) for FREE
In the evolving remote working arrangement, the demand for custom Microsoft Teams apps is increasing rapidly across businesses.
If you are someone who aims to provide users with an exceptional experience through custom-built apps that adhere to industry standards and good governance, Customizing Microsoft Teams is for you! The book starts with an overview of Microsoft Teams customization and configuration prerequisites.

Cyber insurance claims for ransomware reach record high
A new report from cyber insurance provider Coalition shows a 12 percent increase in cyber claims over the first six months of this year, driven by the notable spikes in ransomware and funds transfer fraud (FTF).
Companies with over $100 million in revenue saw the largest increase (20 percent) in the number of claims as well as more substantial losses from attacks -- with a 72 percent increase in claims severity from the second half of 2022.


