
While the government searches for an iPhone backdoor, researchers find another way in
While the news about the dispute between Apple and the FBI rages on, security researchers continue to look for other ways into products, not just the iPhone. But as a prominent device it becomes a big target and deserves extra scrutiny.
The security experts from Israel and Australia decided to test out the electromagnetic radiation emitted by devices, in this case using an iPhone. The results were interesting, though they won't help in the case of phones in the custody of law enforcement.

How APIs are key to digital success
In the digital world it's increasingly APIs that hold everything together, allowing information to be easily shared between applications.
A new study from SmartBear Software gathered responses from over 2,300 software professionals around the world to paint a picture of the current state of the API industry.

Microsoft releases Windows 10 Mobile Insider Preview Build 10586.122 -- here's what's new
While the Windows 10 Mobile roll out has yet to finally kick off, new preview builds are frequently released for users enrolled in the Windows Insider program. Microsoft is working on ironing out the kinks before unleashing its latest smartphone operating system, while trying to improve the user experience for those who have already purchased Windows 10 Mobile handsets.
And, now, early adopters are treated to Windows 10 Mobile Insider Preview Build 10586.122. This "cumulative update", which is offered in the Slow and Release Preview rings, adds support for new smartphones, a significant number of improvements to existing features and some bug fixes. Here's everything that you need to know about it.

Is MasterCard's 'selfie pay' too much of a security risk?
Biometrics were the talk of the town last month in Barcelona. As the world’s mobile technology companies gathered for their largest annual event, Mobile World Congress 2016, talk centered firmly around authentication and identity.
Whilst MasterCard announced it will accept selfie photographs and fingerprints as an alternative to passwords when verifying IDs for online payments, security company Vkansee was demonstrating how easy it was to create a spoof finger with clay and a pot of Play-Doh.

Ransomware is the biggest threat to Android users in UK
Ransomware was the biggest threat to Android users in the UK last year, a new report by security company Bitdefender says.
Even though it’s not as dangerous or prolific as its Windows counterpart, ransomware still played a major role in the overall mobile security landscape for last year.

Kill the password! Yahoo Account Key rolls out to more apps
There have been a lot of attempts to kill the password and replace it with something more secure and easier to use. Biometric measures such as fingerprint and iris readers are increasingly common, but Yahoo is on a mission of its own with Yahoo Account Key.
Recognizing that "passwords suck", Yahoo launched the product back in October and since then there have been a few changes and additions. It's a simple system that uses your mobile as your access key and it's now available in more apps than ever.

Passive Wi-Fi promises major energy savings for mobile and Internet of Things devices
Researchers at the University of Washington have found a way to lower the power consumption of Wi-Fi significantly. They have dubbed the new form of low power wireless internet "passive W-Fi". It could be harnessed to power IoT devices or to help improve battery life in mobile phones.
Passive Wi-Fi will require just 59 microwatts to transmit data between devices which is 10,000 times less than the power used by traditional Wi-Fi chips in personal computers and mobile phones.

Microsoft buys Xamarin to strengthen mobile side
If a few years back we were laughing off Microsoft's efforts in the mobile market, today we are looking at the software giant in a different light. That "mobile first, cloud first" mantra that Satya Nadella introduced us to when he became CEO now defines Microsoft, which has quickly evolved into one of the most important players in the mobile space afterwards.
Under Nadella, Microsoft has tackled mobile in a more meaningful way, refocusing its strategy so that it could become a major developer for more than Windows and Windows Phone. Today, the software giant's best services and products are also found on Android and iOS, the most important mobile platforms, and more have been added following high-profile acquisitions like Acompli and SwiftKey. Now, Microsoft adds Xamarin to its mobile portfolio, proving once again that it is dead serious about conquering mobile.
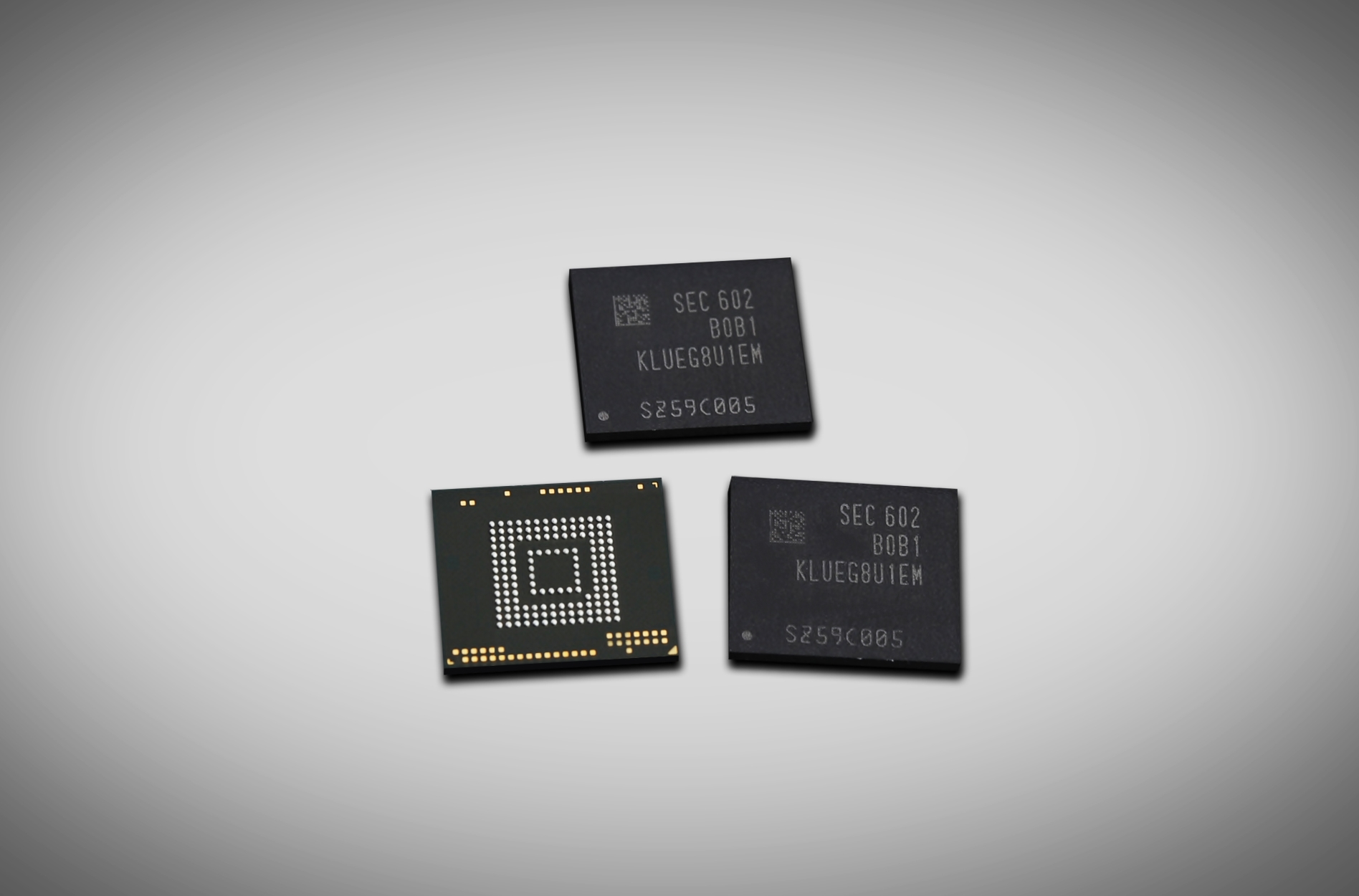
Samsung unveils speedy 256GB Universal Flash mobile storage -- will Apple use it for iPhone 7?
Last year, I bought my first iPhone. Shockingly, the base model still came with a paltry 16GB of storage. Since this was my first-ever such Apple smartphone, I decided to go nuts and splurge on the massive 128GB. Since I store my photos in the cloud, and stream music and movies, I have come nowhere near filling it up. I should have bought the 64GB, but I digress.
Of course, my situation is not the same as everyone else -- some people truly need 128GB or more. Unfortunately, Apple does not offer more than 128GB -- yet. This may change, however, as Samsung announces crazy fast 256-Gigabyte Universal Flash Storage for mobile. The high performance should make these 256GB modules very popular with manufacturers. This will certainly show up in Android devices, but could Apple select it for the upcoming iPhone 7?

Enterprises have no protection against mobile malware
Mobile enterprise security firm MobileIron has released its Q4 2015 Mobile Security and Risk Review, discussing the threats and risks that enterprises face in their mobile deployments.
The report reveals the worrying find that more than 50 percent of enterprises have at least one non-compliant device, creating a broader attack surface for malware and data theft.

Think your mobile device is faulty? You're probably not using it right
A new report shows that almost three-quarters of mobile devices returned with problems to mobile network operators and manufacturers in Europe and North America have 'No Trouble Found'.
The quarterly trend report from Blancco Technology Group also finds that in Europe device failures soared during the second half of 2015 -- rising from 14 percent during the third quarter to 29 percent during the fourth quarter.

The top 5 myths about Virtual Mobile Infrastructure (and, oh yeah, the facts)
With more and more enterprises recognizing the need to go beyond securing devices while still finding an effective way to deploy native mobile apps to employees, it's little wonder that remote enterprise approaches like Virtual Mobile Infrastructure (VMI) are receiving more eyeballs in the enterprise mobility space and the scrutiny that comes along with it. With this comes questions, doubts and even fears over the whether this new approach can really fulfill on its promise.
In fact, fears can spiral into outright myths if left to fester. Remember the myth that Macs couldn't get viruses? We all know how that claim turned out. To this end and, without further ado, here's the truth about five of the most common myths you may have heard about VMI.

Microsoft improves Windows Store's app visibility
Finding apps that are published in Windows Store should not be a problem, but this is exactly what some developers have been complaining about. It seems that when conducting a search there are titles that do not show up in the results, even though the query matches their name. As a developer put, it is a "disaster".
This is a problem not only for the developers who have worked hard to make apps for Windows Store, but also for Microsoft and its users. After all, what the search feature turns out reflects the quality of the app store. This issue may now be gone, as the software giant says that app visibility has finally been improved.

Avast finds Mobile World Congress visitors among the least safe
One would think that those attending a big technology show would be among the more savvy tech users, but sometimes they are the ones who maybe think they are above the fray and forget about the multitude of things that can go wrong whenever you are online.
To illustrate this problem, security firm Avast took a trip to Barcelona, where the Mobile World Congress show is underway. Much of the flow of people entering the airport were there to attend the show, though likely some tourists and business travelers were in the mix as well.

The cost of mobile data breaches in big companies
A mobile data breach could cost a large enterprise over $25 million (£18 million) according to a new report.
The study of security and IT leaders in Global 2000 companies, carried out by mobile security specialist Lookout and the Ponemon Institute, examines the risk introduced by employees accessing increasing amounts of corporate data via their mobile devices.