
Ransomware attacks affect five percent of SMBs
Five percent of all small and medium-sized companies in the entire world were victims of a ransomware attack in 2016 alone, with the money paid out to reclaim data reaching new highs, new research has revealed.
Datto's new State of the Channel Ransomware Report found that an estimated $301 million (£222 million) was paid to ransomware hackers from 2016-2017.

The practical guide to fighting ransomware
Close your eyes for a second. Imagine you are in charge of an IT security team in an enterprise, where the headcount is measured in the thousands. Or, you’re the single security engineer in a startup that just hired its 100th employee.
Either way, you haven’t had it easy these last few months. WannaCry and Petya/NonPetya ransomware attacks caused you to spend hours on the phone and in meetings with your superiors, answering countless questions on the security of your infrastructure.
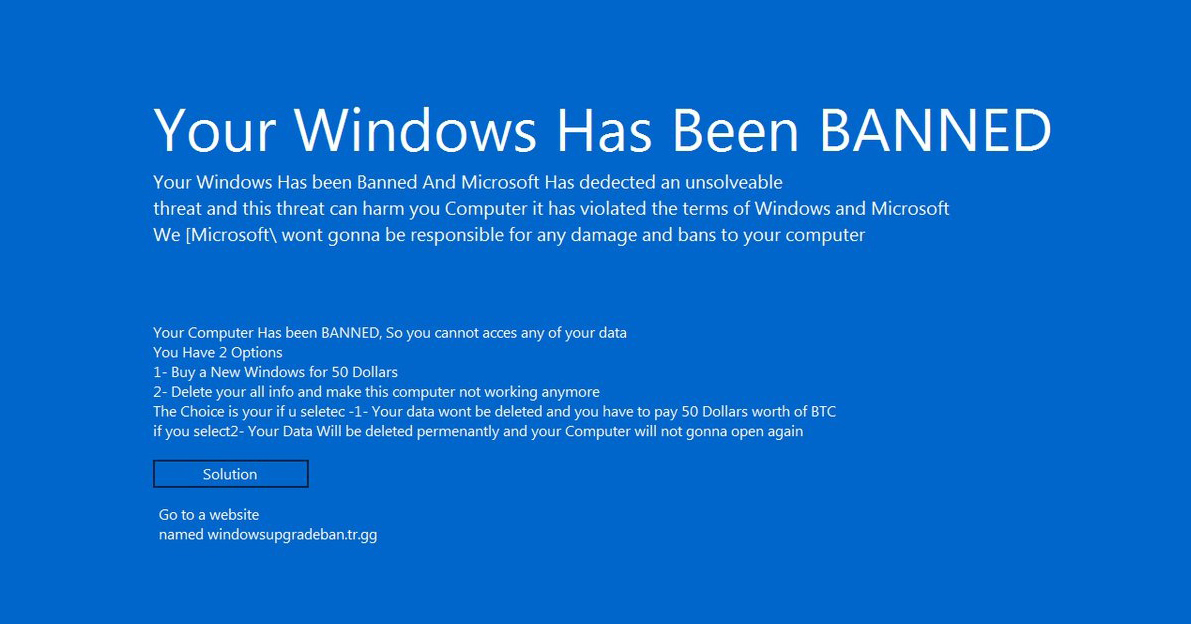
'Your Windows Has Been Banned' malware makes an unwelcome return
"Your Windows Has Been Banned" is a nasty piece of malware that first surfaced in 2016. It locks your computer screen and displays a message stating "This PC has been banned for terms of use violations."
It doesn’t go into specifics for the ban -- because, obviously, it’s not a real ban -- but simply says that your PC has been locked in order to "protect the Windows service and its members," adding "Microsoft does not provide details about specific PC bans."

Carbon Black launches streaming protection against ransomware
Ransomware remains one of the most serious threats to organizations of all sizes, but traditional signature-based detection methods can struggle to identify the latest attacks.
Endpoint security company Carbon Black is launching its latest Cb Defense next-generation anit virus (NGAV) solution using 'Streaming Ransomware Protection' designed to detect and prevent attacks, even if the ransomware employs fileless techniques or unknown tactics.
Ransomware is the top threat to business data
New research from research organization the SANS Institute reveals that frontline IT professionals consider ransomware to be the top overall threat to data availability.
Insider threats and denial of service are also considered top threats to sensitive data. While the majority of respondents indicate that they escaped actual compromise of sensitive data in the last year, enough respondents did lose data to provide valuable lessons from these events.

Thwart ransomware and protect your data with our O&O Disk Image 10.5 giveaway, worth $49.95
Everybody needs a backup -- with ransomware added to the list of threats to your data, now is the perfect time to take full advantage of our latest Downloadcrew giveaway: a full copy of O&O DiskImage 10.5 Professional, worth $49.95, across this coming weekend.
What makes O&O DiskImage special is that it allows you to back up both individual files and folders as well as take a full drive image, so you can protect key data alongside your fail-safe drive image covering your entire Windows installation -- all from one application.

Ransomware attacks almost double in first half of 2017
The percentage of ransomware attacks almost doubled in the first half of 2017 compared to the first half of 2016, from an average of 26 percent to an average of 48 percent of the main attack categories worldwide.
This is according to a mid-year cyber attack trends report from threat prevention company Check Point. It also finds that 23.5 percent of organizations were impacted by the RoughTed malvertising campaign, and 19.7 percent of organizations were impacted by the Fireball malware over the same period.

Attacks from unknown threats increase by 40 percent
The second quarter of this year has seen two of the largest recorded cyber attacks in WannaCry and NotPetya, and the latest quarterly report from Panda Security reveals there's been an increase in unknown threats too.
PandaLabs analyzed attack data collected from all devices protected by one of Panda Security's solutions and discovered a 40 percent increase in attacks from unknown threats from the previous quarter.

NotPetya isn't your typical ransomware
Ransomware is often considered a somewhat low-stakes annoyance: in most cases, the data itself doesn’t leave the network and public operations aren’t compromised. NotPetya changed the game -- it’s shown us the potential of how wildly damaging ransomware infections can be from here on out. It can feel like science fiction at times, but is now utterly reasonable to consider any data or device with a CPU and memory on your network as something that can be held hostage by ransomware.
Ransomware has proven to be a lucrative endeavor: more and more central and important systems are being targeted. Cryptolocker targeted family photos. Later variants somewhat indiscriminately encrypted any user file they had access to -- and last month, we saw NotPetya locking out machines entirely.

Ransomware victims paid over $25 million to recover files
Ransomware victims have paid more than $25 million in the past two years to get their data back, a new study by Google has shown.
The report, made by researchers at Google, Chainalysis, UC San Diego, and the NYU Tandon School of Engineering, followed the trail of cryptomoney through the blockchain, allowing researchers to get a birds-eye view of the ransomware world.

UK ransomware victims most likely to pay up
A new study from anti-malware specialist Malwarebytes reveals that UK users are most likely to pay up if hit by ransomware.
The study of over 1,000 companies across the US, France, UK, Germany, Australia, and Singapore reveals that 56.9 percent of UK businesses surveyed opted not to pay the ransom, and 46.2 percent lost files by not paying. In comparison, 84.1 percent of French businesses surveyed opted not to pay the ransom, and only 24.5 percent lost files.

Exploring the psychology of ransomware
In recent months we've seen high profile ransomware attacks target many businesses, and we've seen cyber criminals making greater efforts to target their victims.
A new study from endpoint protection company SentinelOne and De Montfort University has been looking at how social engineering tactics are used by cyber criminals to manipulate and elicit payments from victims.

How ransomware is going manual to target victims [Q&A]
The ransomware attacks that make the news are the ones like WannaCry and NotPetya that spread rapidly and affect many businesses.
But there's a new breed of manual ransomware attack happening that seeks to pick its victims much more selectively with a view to causing maximum disruption. We spoke to Roy Fisher, incident investigator at cyber security company MWR to find out more.

Goldeneye attack is not ransomware
On June 27, reports of a rapidly spreading ransomware attack started to emerge from Ukraine. The speed at which critical infrastructure networks were shutting down pointed to a ransomware application with a wormable component, whose virality called to mind the WannaCry ransomware. In less than three hours, the infection crippled banks, ATMs, public transport and an airport, as well as utilities provider Kyivenergo. Then it spread outside the Ukraine.
As multiple critical infrastructure networks reported major blackouts, Bitdefender started an internal investigation over isolated malware samples to trace the attack’s origin and better understand what it targeted, and how.

Rapid response software helps companies recover from ransomware attacks
Recent high profile ransomware attacks including WannaCry and NotPetya have highlighted the fact that often the time organizations take to recover is just as damaging as the attack itself.
Network visibility firm Portnox is aiming to tackle this with the launch of Rapid Ransomware Response and Control as part of its suite of network access control (NAC) systems.