DMARC -- rebuilding trust in email [Q&A]
Email has become the default means of communication for both businesses and individuals, but as we saw yesterday it isn't without its problems.
A major issue email has is that of security, cyber criminals are getting better at creating phishing and other messages that accurately spoof commercial organizations. But there is a technology in the form of Domain-based Message Authentication, Reporting and Conformance (DMARC) which has the potential to restore faith in email communication.

New authentication methods help companies to ditch passwords
Most people now recognize that passwords alone are flawed as a means of securing systems. The problem is that there are lots of options when it comes to finding a better way of doing things.
Access control specialist SecureAuth is helping the move towards a passwordless world with the introduction of additional multi-factor authentication (MFA) methods, including Link-to-Accept via SMS or email, and YubiKey, the FIDO Universal Second-Factor (U2F) security key by Yubico.

Improving the measurement of cyber threats before they turn into attacks
Cyber attacks are a major problem for companies and they can be made all the more devastating if a long time elapses before they're discovered.
A new report by the Cloud Security Alliance looks at helping enterprises develop metrics and processes to measure threats before they become cyber attacks.

Google Play Protect branding to be added to certified Android devices
Google Play Protect is the company's latest attempt to prevent Android users from being tricked into installing malware or insecure apps. As an extension of this, Google is introducing a branding program that will see the Google Play Protect logo added to certified Android devices.
The certification of Android phones and tablets is not a new concept -- it's something that Google has been doing for a while. But the new branding on packaging will help buyers identify devices that Google has approved, and it should also encourage more manufacturers to submit their hardware for certification.

New cloud solution allows multi-factor authentication across the enterprise
Data breaches can often be traced back to weak or stolen credentials, add in a proliferation of systems in the cloud and increasing levels of mobile access, and protecting business systems becomes a major headache.
Independent identity provider Okta is launching its latest cloud-based Okta Adaptive Multi-Factor Authentication (AMFA) that makes two-factor authentication standard for every user.

Intel's 8th-gen processors help deliver secure payments
Earlier this month we saw Intel launch its new 8th-generation Core processors. As well as improved performance, these chips offer added security with Intel Software Guard Extensions (Intel SGX) technology.
Thanks to a collaboration with authentication specialist Nok Nok Labs (NNL) the new chips with SGX are able to deliver standards-based authentication to enable stronger, simpler, and more secure payments for computer users.

Are you doing enough to address your risk? Here are a seasoned CISO’s fundamentals
Several years ago, I received an early-morning phone call at home from one of my security staff. Our security operations center had just contacted us, reporting anomalous data traffic. They believed we had several assets that were infected with malware. As I listened to the incident response team triage the event, I thought to myself, "What can I do as a CISO to better protect my organization?"
I had numerous networks and legacy assets under my purview, and even though I had a solid security program, I didn’t feel we were doing enough to address our risk. What fundamentals could I incorporate to better prepare my teams and my security organization?

FBI wants US businesses to stop using Kaspersky software
The FBI has admitted that it is actively discouraging businesses to not use security products from Kaspersky Lab.
Rob Joyce, the US government's Cyber Security Coordinator, said that the agency has been actively trying to convince companies in the private sector to no longer use products from the Russian security firm following a number of recent concerns.
Why are so many organizations struggling to patch? [Q&A]
Many recent cyber attacks like WannaCry have succeeded by exploiting vulnerabilities that, although known, have gone widely unpatched.
Why do some organizations find it so difficult to keep their systems up to date and what can they do to better protect themselves? We spoke to Wendy Nather, principal security strategist at Duo Security to find out.

Google Play apps spread malware through advertising SDK
Through the use of an advertising software development kit contained in 500 apps on the Google Play Store, cybercriminals were able to spy on users and even infect their mobile devices with malware.
That's according to security firm Lookout, which discovered that the Android apps in question all had the lgexin ad SDK built into them which gave unauthorized third parties access to user devices.

Government organizations lag behind in implementing latest security practices
Cyber attacks are becoming more complex and intense. In addition, many hackers are interested in the types of sensitive data held by government bodies. Yet a new study shows that these organizations are lagging behind in dealing with IT risks.
The study by data visibility platform Netwrix reveals that while 57 percent of government entities focus on endpoint protection, 72 percent experienced security incidents in 2016, the most common reasons being human errors and insider misuse.

Non-Windows platforms increasingly at risk from malware
Where it was once the case that damaging malware attacks were aimed solely at Windows devices, a new study shows that strategic attacks on both Mac and Android devices are rapidly rising.
The report by Malwarebytes reveals that Android ransomware was up by more than 100 percent in the second quarter of 2017. In addition, Mac malware
this year is already at the highest it has ever been.
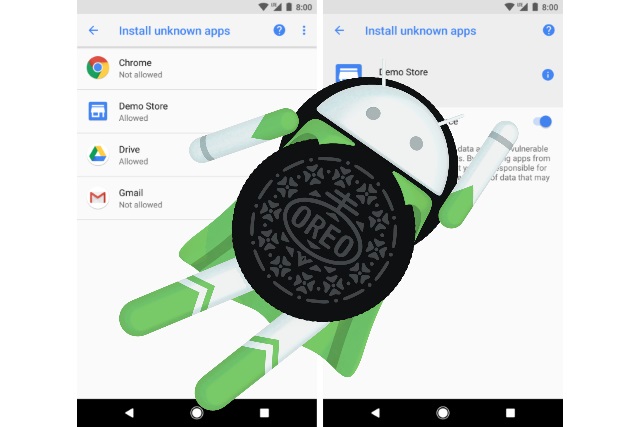
With Android Oreo, Google is stepping up app security
App security is undeniably an issue for Android users, particularly those who choose to install apps from outside of Google Play. Even apps that are housed in the main store are not immune to security issues, but those from other sources are rather more risky.
With Android O, Google has ditched "Allow unknown sources" -- the setting that could be toggled to allow for the installation of non-Play apps. Instead, there is a new "Install unknown apps" permission, and Google thinks this offers more control and greater security.

DDoS attacks increase by 28 percent in Q2 2017
DDoS attacks are seeing a major rise as hackers seek more diverse threats, according to new research.
The latest State of the Internet/Security Report from Akamai reveals that the number of DDoS attacks increased by 28 percent in the second quarter of 2017, following three consecutive quarters of activity decline, as attacks from the PBot malware hit a new high.

Enterprises not confident security can keep up with digital transformation
Businesses are increasingly turning to digital transformation to accelerate their online presence, to enrich products, deepen customer relationships, and boost their brand.
But the bad guys have gone digital too, taking advantage of the digital ecosystem and user trust to make more sophisticated attacks. A new study sponsored by digital threat management company RiskIQ finds that for many businesses digital transformation and the changing external threat landscape are outpacing enterprise security capacity.