Retailers may soon use tagged Facebook photos to identify you in stores

A new tech startup that produces facial recognition camera systems tied to Facebook tagged photos, plans to offer the technology to more traditional physical stores so they could offer you appropriate deals as you enter their business. That’s great for stores that want to have more targeted information about you, based on a bit of your history and likes. But what about privacy, what are the implications?
For now, you are not included in this scheme unless you opt in via Facebook to a third party service. The service would then present tailored deals to your mobile device when you enter an establishment using the technology (currently being tested in Tennessee). Facedeals, the provider, says this simply bolsters and leverages check-ins so that local businesses have more personal information, and by knowing and targeting the products they offer you based on your likes and preferences they can seem more relevant, like discounted or free drinks for using the service at a bar & grill.
Blizzard hacked for real this time -- change your passwords NOW!

In May we read that game maker Blizzard, developer of a series of popular games including World of Warcraft, Diablo III and Starcraft, was hacked, but that turned out to just be individual compromised accounts from some of its users. Now we read, from Blizzard itself rather than a third party, that they have been hacked and information compromised on their networks. So how are they doing with the breach?
"This week, our security team found an unauthorized and illegal access into our internal network here at Blizzard", the company says. So did they respond well? It seems they got the jump on things and responded quickly, a smart move: "We quickly took steps to close off this access and began working with law enforcement and security experts to investigate what happened."
Have you looked at your .htacess file recently? Your Apache server may not be secure

If your organization’s website runs on Apache, and many do, you might wonder if the webserver’s .htaccess controls are securely configured. If you believe the demo we saw on July 27 at Black Hat by Matias Katz and Maximiliano Soler, the answer is a resounding ‘NO!’ What Katz and Soler describe in their session is not some rare “corner case” hack that could only possibly occur in a lab with billions of automated attempts, this is easily testable in the real world, and the tools to exploit it are freely available.
It turns out that Apache, the most commonly-used web server in the world, has an arrangement where it hands off PHP-based requests within .htaccess to PHP itself, which has worked fine on millions and millions of websites for years. But with .htaccess, you can specify what requests get sent to PHP to try to interpret. The usual methods are GET and POST, but if you feed the .htaccess process some non-standard input, PHP automatically (unless otherwise instructed) treats it as a GET request, and allows the utility to start saving the PHP files on a webserver to your local filesystem.
5 ways to put hackers on the defensive

Black Hat keynote speaker Shawn Henry, the former executive assistant director of the FBI’s Criminal, Cyber, Response and Service Branch, started off the day after opening remarks from Jeff Moss, founder of Blackhat. Moss wondered if now was the time for the cyber-security sector to take a more aggressive/offensive approach. Moss mentioned working for a former employer years back, a firewall manufacturer that had a product that would launch specially crafted code in response to an attacker, sort of an early offensive DoS attack. This was an early attempt by security professionals to cause pain by going on the offensive.
But since DoS attacks aren’t exactly a legal offensive tactic nowadays, what to do? He recommends civil action, a la recent Facebook actions where attackers were sued in civil court. But what happens when attackers are overseas? Mr. Moss is hopeful that responding in a civil manner would “encourage” other countries to implement legal protections to stop current and future attack attempts abroad.
Scam sites lure victims with fake YouTube-to-mp3 converters

Want to access the music tracks of YouTube.com videos on your iPod but don’t want to pay? You’re not alone. Recently, a crop of websites have popped up offering to convert the audio from videos to .mp3 files that you can then download at no charge. Sounds great, right? The catch: scammers are trying to capture the popular click traffic and redirect users to scam websites, where you might get more than you bargained for, in the form of free malware and other unpleasantness as a bonus.
Recently, we hosted a “cyber boot camp”, teaching high school students to attack and defend networks. One of our presenters, John Moffat, who often delivers security awareness seminars to teenagers and stresses the dangers of the “free” Internet, referenced this scam in his presentation. While Mr. Moffat doesn’t claim to be a malware expert, he knows a scam when he sees one, and does his best to help others avoid falling prey.
Nation-state hackers attack small businesses, too

Small businesses have their hands full these days in light of a down economy, tightening budgets and the steepening pace of business, but with nation-state hacks front and center in the threatscape, should you worry about those, too, or are you (and your customers) safe?
Nation-state hacks bring to mind images of large defense contractors, big government offices, and/or high profile financial institutions. After all, if a bad actor overseas stole the cutting edge design of a new nuclear reactor, it would be quite a haul for that government and its cronies -- and worth their time, money and effort to go after. But you’re a small business, too small to garner that kind of attention, right?
That Facebook account verification email in your inbox is a scam
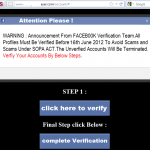
If the scary email or app notification, and subsequent webpage, is to be believed, you have only a few days to verify your Facebook account or you’ll be out of luck. But don’t worry, a few days later you will magically get a few more days to verify, and so the scam goes.
A Twitter follower with the handle of @chasapple sent us a tip on an app message they received, here’s a screenshot of what happens if you clicked the link.
How will the LinkedIn hack affect you?

This morning when I logged into LinkedIn I was greeted with several front page references to the reported hacking of the site, and instructions for changing my password, which I did immediately. This is a good time to change all of your social media passwords, making sure you create a fresh password that is hard to guess and unique to each site. It is not unusual for malicious parties who grab a bunch of passwords from one site to try those same passwords on other sites.
Over 6.5 million account passwords showed up on a Russian forum in SHA-1 (hashed) format to prove that the hackers had indeed succeeded in penetrating LinkedIn. There is a good chance that if the hacker(s) achieved access to LinkedIn passwords then they also know the corresponding LinkedIn usernames, i.e. the matching email address of the account owner.
Cameron's Bio
is a researcher for global security provider ESET and has played a critical role in building the ESET North America Research Lab. Cameron has been building critical technology infrastructures for more than 20 years, beginning as an assembly language programmer in 1987 and eventually becoming an evangelist for Linux and open-source technologies with an emphasis on the security sector. Prior to joining ESET, he founded Logical Web Host in 1998, a data-driven web services company.
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.
