GAO: More security training leads to less compliance, including Los Alamos, NASA
A US Government Accounting Office report released yesterday (PDF available here) reveals an astonishing and counter-intuitive trend: Government agencies' compliance with directives intended to improve information security has declined in inverse proportion to the amount of training they receive.
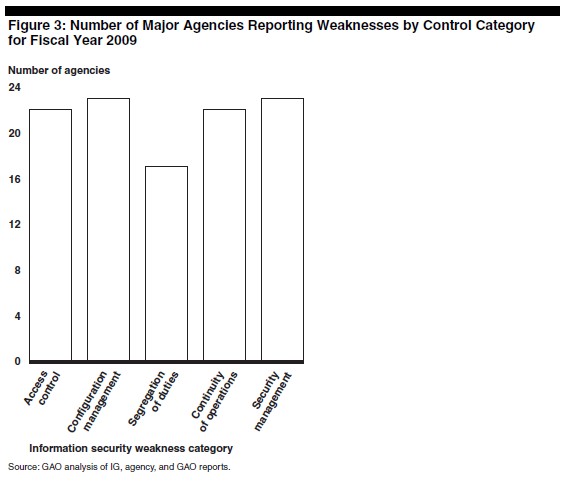
In a report to the House Government Management Subcommittee yesterday, the GAO cited increased awareness of the provisions of the Federal Information Security Management Act (FISMA), due to increased awareness training among the 24 federal agencies tested: 91% of employees in those agencies received testing in fiscal 2009, up 3% from the previous year. But specifically in light of increased exposure to the Gumblar Trojan and the Conficker worm, at least 17 of those agencies were reported to have enacted deficient responses to these increasing threats, including essentially assigning the entire job of security to just one person -- against FISMA's mandate.
Two of the agencies where GAO inspectors reported the most shocking problems were NASA and the Los Alamos National Laboratory. The GAO report chastised Los Alamos in particular: "Specifically, (1) risk assessments were not comprehensive, (2) specific guidance was missing from policies and procedures, (3) the training and awareness program did not adequately address specialized training needs for individuals with significant network security responsibilities, (4) system security plans were incomplete, (5) the system security testing and evaluation process had shortcomings, (6) corrective action plans were not comprehensive, and (7) contingency plans were incomplete and not tested. In addition, the laboratory's decentralized management approach has led to weaknesses in the effectiveness of its classified cybersecurity program. Although the laboratory has taken steps to address these weaknesses, its efforts may be limited because LANL has not demonstrated a consistent capacity to sustain security improvements over the long term."
The news for NASA was similar, particularly highlighting that agency's failure to consistently detect and report security incidents. GAO believes that the problem isn't one of poor software or even bad training. It's a management problem, the report says -- an apparent case of indecision about spreading the responsibility for security among everyone.
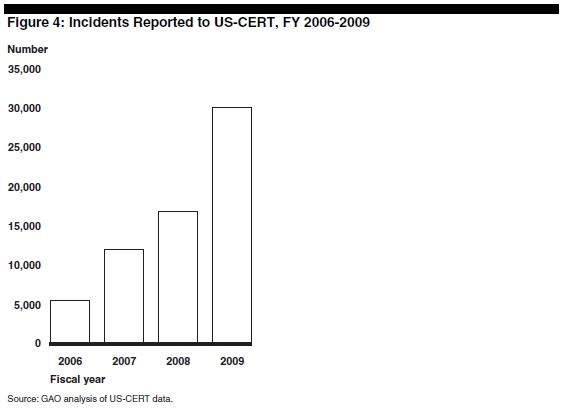
This despite the fact that the quantity of security incidents on government agency systems that were reported properly, has increased by some 400% over a three-year period.
GAO cites the continued need for a comprehensive national cybersecurity strategy, as outlined by President Bush in 2008 when he launched the Comprehensive National Security Initiative (CNSI). The Office suggests that CNSI be given more time to achieve the goals set out for it. But as one example from the report describes, the National Institute of Science and Technology's recommendations for securing systems with Windows XP and Windows Vista, is still ongoing, and would be one of those programs that GAO recommends continue. It does not appear that this program, as implemented in 2008, would encompass the simple matter of upgrading to Windows 7.
