Dirty_Sock vulnerability in Canonical's snapd could give root access on Linux machines
A security researcher has discovered a vulnerability in Canonical's snapd package which could be exploited to gain administrator privileges and root access to affected Linux systems. The security issue has been dubbed Dirty_Sock and assigned the code CVE-2019-7304.
Chris Moberly found a privilege escalation vulnerability in the snapd API. This is installed by default in Ubuntu -- under which proofs of concept have been tested and found to work "100% of the time on fresh, default installations of Ubuntu Server and Desktop" -- but may also be present in numerous other Linux distros.
The Ubuntu CVE Tracker describes the vulnerability as: "snapd 2.28 through 2.37 incorrectly validated and parsed the remote socket address when performing access controls on its UNIX socket. A local attacker could use this to access privileged socket APIs and obtain administrator privileges".
Moberly found the security hole back in January and reported it to the snapd team who developed a fix fairly quickly, but unpatched systems remain at risk. He explains his findings:
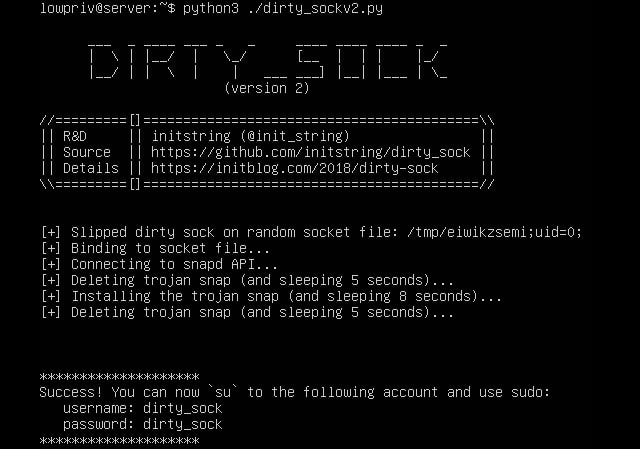
snapd serves up a REST API attached to a local UNIX_AF socket. Access control to restricted API functions is accomplished by querying the UID associated with any connections made to that socket. User-controlled socket peer data can be affected to overwrite a UID variable during string parsing in a for-loop. This allows any user to access any API function.
With access to the API, there are multiple methods to obtain root.
He provides two possible exploit routes, dirty_sockv1 (which "uses the 'create-user' API to create a local user based on details queried from the Ubuntu SSO"), and dirty_sockv2 (which "sideloads a snap that contains an install-hook that generates a new local user").
In a post about the update that addresses the issue, Canonical says:
Chris Moberly discovered that snapd versions 2.28 through 2.37 incorrectly validated and parsed the remote socket address when performing access controls on its UNIX socket. A local attacker could use this to access privileged socket APIs and obtain administrator privileges. On Ubuntu systems with snaps installed, snapd typically will have already automatically refreshed itself to snapd 2.37.1 which is unaffected.
Moberly praises the response to his reporting of the vulnerability, saying: "The snapd team's response to disclosure was swift and appropriate. Working with them directly was incredibly pleasant, and I am very thankful for their hard work and kindness. Really, this type of interaction makes me feel very good about being an Ubuntu user myself".
