
Ten technology predictions for 2014
Here is my first of two prediction columns for 2014. There’s just too much for it all to fit in one column. My neighbor and good friend Avram Miller wrote a predictions column this year that’s quite good and you might want to read it before this one. We discuss some of the same things though of course Avram and I occasionally agree to disagree.
This column is mainly about business predictions for 2014 while the follow-up column will be more about products and technologies.

Where’s that Black Swan when we need one?
This was supposed to be my 2014 predictions column but the volume of correspondence following a call for predictions on my blog last week was such that I suspect it will be the first of three prediction columns with my actual predictions occupying columns two and three. This column is about the broader subject of how to predict.
I’ve written at least once before on How to Predict the Future. Do a search on that string and an old PBS column will float to the surface. All of that still applies but in this column I want to look somewhat deeper at the motivations and methods of predictors whether they actually know what they are doing or not.

RSA takes one for the team, but which team?
Edward Snowden says (according to Reuters) that RSA Security accepted $10 million from the National Security Agency in exchange for installing (or allowing to have installed) a secret backdoor so the NSA could decrypt messages as it pleased. Hell no says RSA (a division of storage vendor EMC), stating in very strong terms that this was not at all the case. But then in a second day look at the RSA/EMC statement bloggers began to see the company as dissembling, their firm defense as really more of a non-denial denial. So what’s the truth here and what’s the lesson?
For the truth I reached deep into the bowels of elliptic cryptography to an old friend who was one of the technology’s inventors.

Some thoughts on how a Grinch stole Target’s Christmas
There was a time when "activist investor" Carl Icahn actually owned and ran businesses, one of which was TransWorld Airlines (TWA), eventually sold to American Airlines. In an attempt to cut costs, TWA under Icahn outsourced reservation service to a call center built in a prison with prisoners on the phone. When you called to book travel you were giving your credit card number to a felon and telling him when you’d be away from home. Smart move, Carl, and very akin to what may have caused the post-Thanksgiving theft of 40 million credit card numbers from Target, the U.S. discount retailer.
Target used to do its IT all in the USA, then to save costs they moved IT to a subsidiary in India. Care to guess where the Target data breach came from? I’m guessing India. I’m also guessing that there will never be any arrests in the case.

Gallows humor for the NSA privacy debate
It’s hard to believe sometimes, but I began writing my columns -- in print back then -- during the Reagan Administration. It was 1987 and the crisis du jour was called Iran-Contra, remember it? Colonel Oliver North got a radio career out of breaking federal law. The FBI director back then was William Sessions, generally called Judge Sessions because he had been a federal judge. I interviewed Sessions in 1990 about the possibility that American citizens might have their privacy rights violated by an upcoming electronic surveillance law. "What would keep an FBI agent from tapping his girlfriend’s telephone?" I asked, since it would shortly be possible to do so from the agent’s desk.
"It would never happen", Sessions said.

You may not want that Windows Bay Trail tablet after all
An old friend has been telling me for months that the future of personal computing was coming with new Windows tablets using the Bay Trail system-on-chip architecture built with Intel Silvermont cores. Silvermont is the first major Atom revision in years and is designed to be much faster. Bay Trail would lead to $199 8-inch Windows tablets while also fixing the limitations of Intel’s previous Clover Trail. Well Bay Trail units are finally shipping but my techie friend is sorely disappointed with his.
The lure of this platform for Intel is great. Manufacturers could use the same chassis and chipsets for everything except gaming boxes and servers. Eight inch tablets, ChromeBooks, Ultrabooks, 10-inch tablets, and netbooks, all one chassis with up to 4GB of RAM and a 256GB SSD. One size fits all for home, car, travel, and work.

My sister’s a quilter and Google mugged her!
On my home page you’ll always see a link to Portrait Quilts, my sister’s website where for several years she has sold quilts, pillows, and tote bags printed with customer photographs. This is how she makes her living, selling on the web and through photo stores. Buy one, please. Or if you are a quilter she’ll print your photos on cloth so you can quilt them yourself.
Then approximately three months ago Google decided that Portrait Quilts does not exist.

See you on the golf course, John, Cisco is in trouble
Last week I began this series on large companies in turmoil by looking at Intel, which I saw trying to guarantee its future through enlightened acquisitions that actually emulated this week’s company -- Cisco Systems.
So if Cisco already knows how to assimilate other companies and technologies to stay ahead of the market, how can it have a problem? Cisco’s problem is its market is mature and being commoditized with all boats sinking. And this time there isn’t an obvious new idea to buy.

Why Intel wants to be everyone’s chip maker
This is the first in a series of columns on the strategic direction of several major technology companies that have faltered of late. We’ll start here with Intel, follow in a couple days with Cisco, followed by Microsoft, then see where it goes from there.
At Intel’s annual shareholders’ meeting last week the company talked about moving strongly into mobile chips and selling its stillborn OnCue over-the-top video streaming service, but the most important story had to do with expanding Intel’s manufacturing capacity. This latter news is especially important because if you look at the square footage of 14 nanometer fab facilities Intel says it will be bringing online in the next two to three years it appears that the company will shortly have more production capacity than all the rest of the semiconductor industry combined.

Amazon’s new graphical cloud helps make desktops obsolete
Amazon Web Services quietly released on Tuesday a pair of new instances on its EC2 cloud computing service. Not just new instances but a whole new type of instance aimed at 2D and 3D graphical computing. For the first time from AWS in a generally available instance, developers and users will have access to virtual machines with GPUs.
It’s like putting a PC in the cloud. More properly it is like putting your PC in the cloud. I think this has great disruptive potential. And that means we’ll see similar services coming soon from other cloud providers.

The Google File System makes NSA’s hack blatantly illegal and it knows it
The latest Edward Snowden bombshell that the National Security Agency has been hacking foreign Google and Yahoo data centers is particularly disturbing. Plenty has been written about it so I normally wouldn’t comment except that the general press has, I think, too shallow an understanding of the technology involved. The hack is even more insidious than they know.
The superficial story is in the NSA slide (above) that you’ve probably seen already. The major point being that somehow the NSA -- probably through the GCHQ in Britain -- is grabbing virtually all Google non-spider web traffic from the Google Front End Servers, because that’s where the SSL encryption is decoded.

How Big Data is destroying the US healthcare system
One thing I find ironic in the current controversy over problems with the healthcare.gov insurance sign-up web site is that the people complaining don’t really mean what they are saying. Not only do they have have little to no context for their arguments, they don’t even want the improvements they are demanding. This is not to say nothing is wrong with the site, but few big web projects have perfectly smooth launches. From all the bitching and moaning in the press you’d think this experience is a rarity. But as those who regularly read this column know, more than half of big IT projects don’t work at all. So I’m not surprised that there’s another month of work to be done to meet a deadline 5.5 months in the future.
Yes, the Obama Administration was overly optimistic and didn’t provide enough oversight. Yes, they demanded fundamental changes long after the system design should have been frozen. But a year from now these issues will have been forgotten.

Privacy is dead and here’s how
My friend Dave Taht, who battles bufferbloat for us all, pointed me today to a document from the Wireless Internet Service Provider Association. It’s the WISPA CALEA Compliance Guide, which details most of the rules that wireless ISPs are required to follow by CALEA -- the Communications Assistance for Law Enforcement Act of 1994. These rules, variants of which apply to all telcos and to ISPs of all kinds (not just wireless), say what those companies are required to do to comply with the law. More directly, it specifies how they can be required to intercept customer communications and relay that content to law enforcement agencies.
Read it if you have a moment. The document, which is chilling, explains a lot both in what it says and what it doesn’t say.

Mainframe2 runs super-powerful Windows apps in the cloud
My friend Nikola Bozinovic (say that three times fast) is a very sharp software developer originally from Serbia who has, over the years, worked for most of the usual suspect American software companies. He is also the guy who restored from a grotty old VHS tape my film Steve Jobs — The Lost Interview. And as of this week he’s the CEO of Mainframe2, an exciting startup strutting its stuff at the DEMO conference in Santa Clara.
Mainframe2 claims it can put almost any Windows application into the cloud, making apps usable from any device that can run a web browser supporting html5. We’re talking Photoshop and AutoCAD on your iPad. This is a big deal.
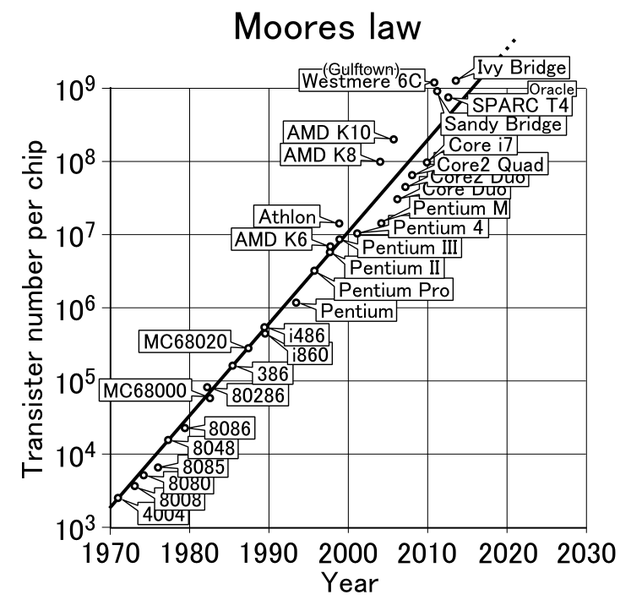
Breaking Moore’s Law
No law is more powerful or important in Silicon Valley than Moore’s Law -- the simple idea that transistor density is continually increasing which means computing power goes up just as costs and energy consumption go down. It’s a clever idea we rightly attribute to Gordon Moore. The power lies in the Law’s predictability. There’s no other trillion dollar business where you can look down the road and have a pretty clear idea what you’ll get. Moore’s Law lets us take chances on the future and generally get away with them. But what happens when you break Moore’s Law? That’s what I have been thinking about lately. That’s when destinies change.
There may have been many times that Moore’s Law has been broken. I’m sure readers will tell us. But I only know of two times -- once when it was quite deliberate and in the open and another time when it was more like breaking and entering.

