Betanews Is Growing Alongside You
You may have noticed things have been a little quieter than usual here at BetaNews. We wanted to take a moment to share why, and, more importantly, what’s coming next.
We're excited to announce that Betanews is growing!
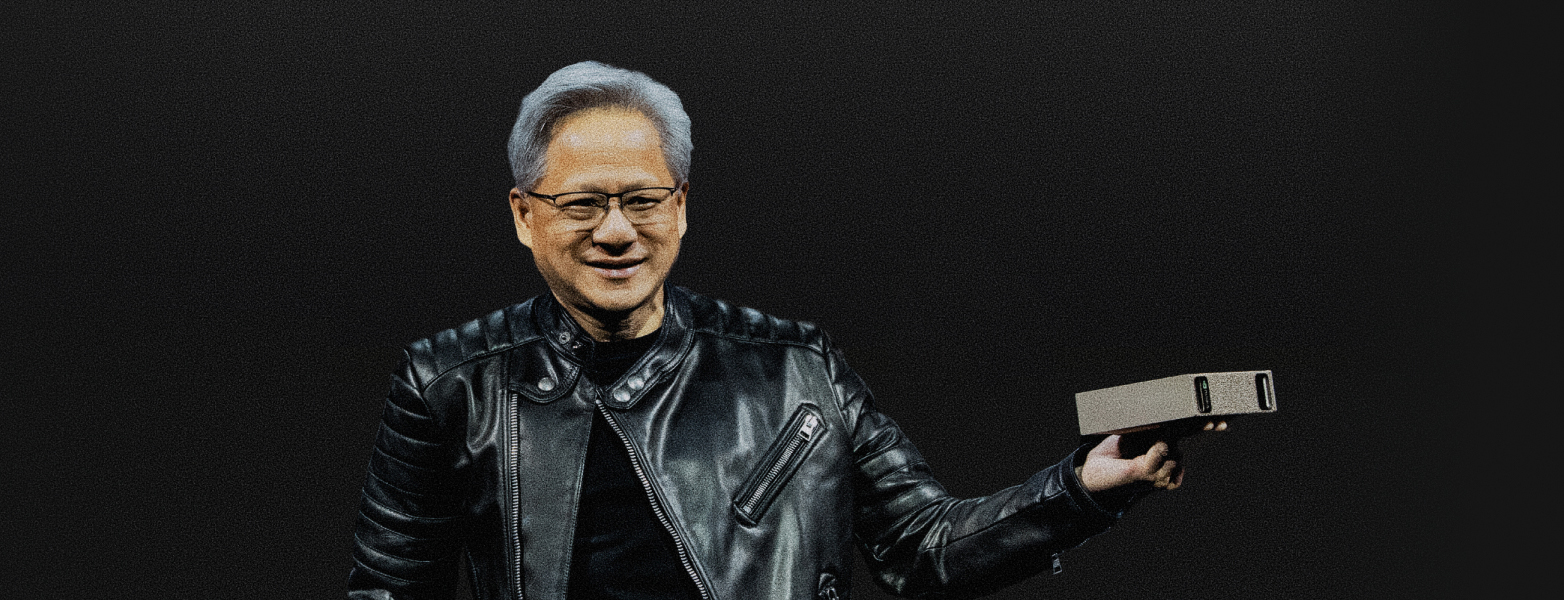
What does Nvidia's palm-sized AI supercomputer, DGX Spark, really mean for the future of AI development at the edge?
Nvidia CEO Jensen Huang’s now-famous GTC 2025 reveal where he held up a palm-sized AI supercomputer and likened it to the original DGX-1 “with Pym particles” wasn’t just a show of engineering flair.
The DGX Spark, as it’s now officially called, marks a turning point in how we think about AI infrastructure. For the first time, Nvidia’s Grace Blackwell superchip architecture has been distilled into a 1.2kg box that fits on a desktop, priced accessibly for research teams and small-scale deployments.

Why data privacy is a fundamental human right
In an age where every click, swipe, and search can be tracked, stored and analyzed, data privacy is no longer a luxury but a necessity. From social media profiles to medical records and financial transactions, personal information is constantly collected and processed, often without understanding or consent.
Recognizing data privacy as a fundamental human right isn't just a legal or technical issue, but vital for individual dignity, autonomy, and freedom of expression.

Safeguarding your marketing channels: how AI-powered automation is fueling new threats and how to defend against them
Scammers are already using AI-powered automation to manipulate marketing channels. We don't want to hand out a playbook for bad actors, but it's important to recognize the growing number of scams that have been enhanced by AI and automation tools. Most scams are still about money, either directly or by collecting personal data that can be used to access financial information. If there is no money, there is typically little motive.
In a space like eCommerce, for example, we've seen scammers clone legitimate websites to trick customers into handing over their payment information. These spoof sites look identical to the real thing.

Why now is time to build sustainable accessibility into organizational culture
Accessibility is increasingly recognized as an important part of how organizations deliver value across a number of industries, and rightly so. It goes beyond meeting legal requirements to improve user experience, promote inclusion, and build better services for all. Yet, despite the growing awareness, some organizations still see integrating accessibility into its processes as an isolated effort or something to be 'checked off' near the end of a project, prompted by upcoming regulation, user complaints, or reputational risk.
This reactive approach may satisfy compliance needs in the short-term, but it does little to build lasting, meaningful inclusion. Meaningful progress happens when accessibility is embedded into an organization’s everyday mindset and operations. In short, accessibility must become a fundamental element, not an afterthought. Adding accessibility to everyday practices instead of reserving it for emergencies allows companies to develop better products, rely on stronger teams, and be more resilient.

The growing role of AI in healthcare: how devices are changing the game
Healthcare hinges on diagnostics, which is why doctors must accurately identify the illnesses they aim to treat to provide proper care for their patients. An incorrect diagnosis introduces the risk that treatment may be ineffective or harmful.
To diagnose properly, doctors rely on data by measuring key metrics and evaluating their implications based on experience, education, and best practices. The more data available to doctors, the more accurate their diagnoses can be.

How GPUs could shape the future of blockchain and blockchain could shape the future of GPUs
Jensen Huang's keynote at GTC 2025 has again been a real show. It gave insights on the future of AI, quantum computing, self-driving cars, etc. But I couldn't help but notice one big absence though: blockchain.
AI, especially with the advent of Large Language Models (LLMs) has driven a massive demand for GPUs. Real-time processing in self-driving cars is also very demanding, so those are areas where GPUs can play a critical role. However, while GPUs have historically been used for cryptocurrency mining, it seems like Nvidia has been cautious about blockchain as a focus area in recent years. This might be due to the volatility of the market, regulatory concerns, or a shift in the overall blockchain landscape -- especially with Ethereum's shift from proof-of-work to proof-of-stake, which reduces the need for traditional mining hardware.

Beyond detecting bots -- in the age of AI, it's all about intent
For the past two decades, cybersecurity teams have been laser focused on identifying ‘what’s bot -- and what’s not’. Over the past couple of years, this focus has shifted slightly, with security teams dedicating most of their attention to the most sophisticated bots.
New developments in AI over the past year have added a new level of complexity, with the emergence of beneficial business bots, like sophisticated AI agents, complicating what was once a binary task of differentiating bot from human.

Preventing cybersecurity stagnation through breach containment
There’s a famous quote by Einstein which reads: “Insanity is doing the same thing over and over again and expecting different results.”
In cybersecurity, this saying has never been more fitting. We’ve seen years of increased investment, a figure Gartner estimates will reach $212 billion this year, yet the cost of breaches continues to rise, reaching $4.8 million in 2024. That’s 10 percent higher than 2023, according to IBM.

Big tech's privacy paradox: Why regulatory alignment is now a technical imperative
The integration of Meta AI into WhatsApp represents a fascinating case study in how technical capabilities can undermine strategic positioning.
WhatsApp’s success was built on a simple technical promise -- end-to-end encryption that creates a secure communication channel. Yet, the introduction of an AI chatbot that explicitly warns users against sharing sensitive information exposes a fundamental architectural contradiction that has broader implications for the tech industry.

DDoS and IP transit: Why integration is the smart choice for modern connectivity
As Distributed Denial of Service (DDoS) attacks grow in both frequency and sophistication, organizations are being forced to re-evaluate their defensive strategies. Gone are the days when a standalone DDoS mitigation service tacked onto your infrastructure was enough for peace of mind.
The current threat landscape demands faster response times, simplified operations, and coordinated protection. A rising trend is the integration of DDoS mitigation directly with IP transit from a single provider.

How high availability mitigates the risks of application downtime
Delivering IT infrastructure that’s highly available, performant and secure is paramount for organizations of all sizes competing in today’s dynamic application landscape. With applications at the core of business operations, users expect them to be available 24/7.
Keeping these applications online and responsive so users enjoy the best application experience is vital to organizations' financial, reputational and operational health.

The modern workplace has a burnout problem: Is AI the remedy?
Burnout has long been an issue in the workplace, made worse by today’s “always on” culture. In fact, data shows that 77 percent of employees report feeling burned out.
If left unchecked, not only will it lead to health consequences, but also negatively impacts business outcomes. For instance, burnout often worsens employee performance and creates talent retention challenges if morale becomes too negative.

Active Directory recovery: Rebuilding the forest from root to tip
After 25 years, Active Directory remains a stalwart of IT infrastructure. Supporting access for an estimated 610 million employees, it enables seamless, secure connectivity to the networks that power daily business operations worldwide. Favored by nearly 90 percent of Global Fortune 1000 companies, according to Frost & Sullivan, Active Directory has long been the primary mechanism for enabling staff to connect, collaborate, and work efficiently.
Despite the rise of cloud-based alternatives, Active Directory's scalability, compatibility, and established integration with Windows environments has ensured its continuing appeal for hybrid and on-premise infrastructures. Its unrivaled scalability and powerful centralized control make it the go-to solution for managing users, devices, and policies at scale.

Why conventional disaster recovery won’t save you from ransomware
The conventional formula for maintaining business continuity in the face of unexpected IT disruptions is as follows: Back up your data. Make a recovery plan. Test the recovery plan periodically.
That approach may work well enough if your primary concern is defending against risks like server failures or data center outages caused by natural disasters. But in the present age of widespread ransomware attacks, conventional backup and recovery planning aren’t always enough.

