
Summer is here and data still needs to be protected
The summer of 2021 is upon us and everyone is excited to get back out and enjoy national parks, oceanfront beaches, amusement parks, campgrounds and so much more. With a large number of employees still working from home and taking time off this summer, it is still critical to protect your organization's data as it travels for summer holiday.
Ransomware attacks are on the rise and continue to be a disruptive force affecting everything from financial institutions, healthcare to SLED (state and local government and education). Due to the rise in remote work prompted by the pandemic, attacks are up 148 percent.

3 ways to streamline your document processing with AI
While Artificial Intelligence (AI) has gained traction with enterprises in other industries, insurance providers have been slower to adopt. In 2016, research by Deloitte noted that less than 2 percent of insurance companies were currently investing in artificial intelligence technologies.
This same research noted that overall funding in AI development was projected to reach $47 billion by 2020. Today, as AI has become prevalent, more and more insurance companies are looking for advanced solutions that will help them effectively process their repositories of day-to-day paperwork and the unstructured data they contain. Intelligent Document Processing (IDP) platform solutions that leverage AI technology are uniquely positioned to help these companies realize significant gains.
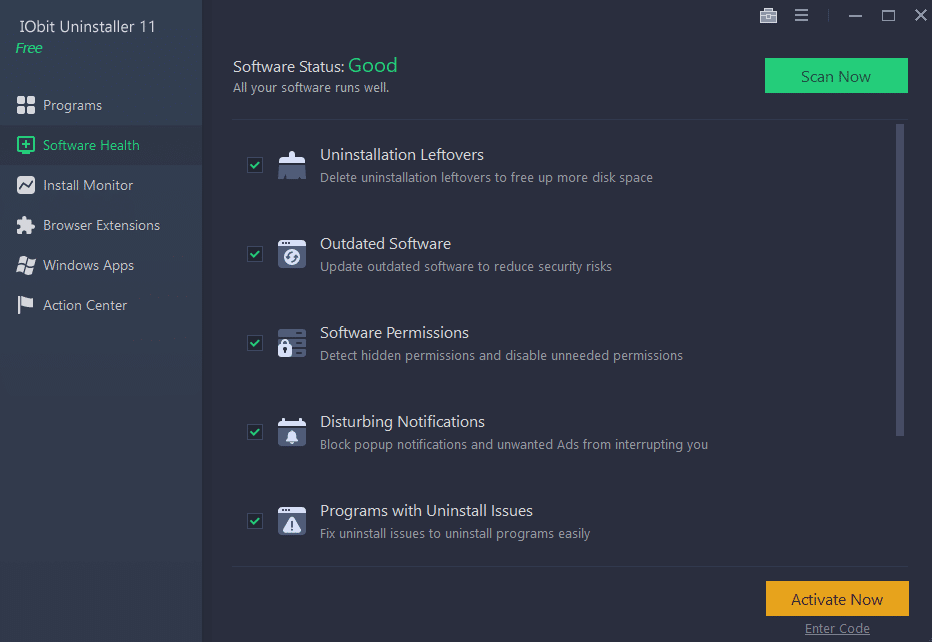
IObit Uninstaller 11 lands with permission management, Windows 11 support and more
Just about every computer in use around the world has a hard drive that contains at least some software that isn’t used or needed. You can, of course, remove apps you don't want by using the Apps & features section of Settings, but this is not guaranteed to get rid of every last trace of any given app.
And this is precisely why software unsinstallers like IObit Uninstaller 11 are so valuable. This tool monitors installations so it knows exactly which files have been added or changed, making it much easier to completely remove apps during uninstallation.

5 questions to consider before choosing an app platform
If you have an idea for an app, the first significant consideration is which app platform to use.
Both Android and iOS have positive growth potential, so there’s no need to be concerned about the platform’s longevity, but there are a few factors to consider, including app performance, budget, audience reach, and platform security.
Backups can save your business
Backups are more common than you think. Every day you most likely have a backup in place, whether it be someone who can cover for you to watch your puppy if something interrupts your schedule or even that spare tire that is in your car in case of a flat.
Backup and recovery plans apply to just about everything that you can think of in your daily life. Let’s focus on your business now and look at top reasons why you really need to have a secure and reliable backup solution.

Going digital: Common sense for successful businesses
Inevitably, the world will change once we have fully emerged from lockdown. With a heightened sense of hygiene and further concerns about workplace safety, employers will need to look closely at ways to reduce contact and move towards what is being touted as the Low Touch Economy. But how can this happen with as little disruption to business as possible?
One of the key ways to help aid in this transition is to embrace digital. Going digital has long been presented as a choice for companies -- now, it’s less a choice and more a necessity to remain relevant and to keep up with the modern age. We take a look at some of the methods business owners will need to adapt for their companies to embrace the "new normal", with a focus on digital saviors.

Why cloud adoption requires an organization-wide culture change
In the space of a year, society has transformed beyond recognition because of COVID-19 and cloud-first for most organizations is now an imperative. To this point, by the end of 2021, 67 percent of all enterprise infrastructure will be cloud-based. But what does this mean for organizational culture, will it change -- and should it change? After all, now cloud adoption is greater than just the IT department. Whether it be a heavier reliance on the accounting team, closer collaboration with the business teams, or better information sharing with the internal IT team, cloud changes the dynamics of team interactions.
Today, an organization's existing culture can strongly predict the potential for cloud success; likewise cloud adoption does have the potential to also alter the company’s culture. It can dramatically change the day-to-day work of individual IT team members, but with the willingness to adjust employee skillsets, a wide range of opportunities can become available as a result of cloud.

How Artificial Intelligence is set to revolutionize industries
There’s no denying that technology has been the key to evolution for almost every industry. From transport to gaming, sports to healthcare, improvements to processes and capabilities have been attributed to rapidly innovating technology. This is particularly prominent in the field of artificial intelligence (AI). What was once reserved for sci-fi movies is now actively a part of our everyday lives, and it’s set to pave the future -- perhaps autonomously!
In this article, we take a look at how AI is set to ignite several key industries.

Preparing your network and employees for a safe return to the office
With the vaccine rollout continuing and positivity on the horizon due to significant reduction in COVID-19 cases, companies are now planning how to return workers to the office safely. To start, employees will most likely return to a hybrid workplace, one where they rotate in and out of the office, part of the time in the office and work from home the rest of the time.
Securing your network and employees will be critical during transitions. While small businesses may perceive this to be a matter of going back to "business as usual" and resuming normal IT operations, there are a number of complexities brought on by the mass exodus out of office that need to be considered. Just as in the beginning of the pandemic, cyber criminals will almost certainly increase their phishing attempts and other malicious attacks, taking advantage of overlooked network vulnerabilities and resource-thin IT teams. To protect their networks, employees and critical data, companies will need to create plans and introduce new safety protocols to ensure security as employees transition between working from home and in the office.
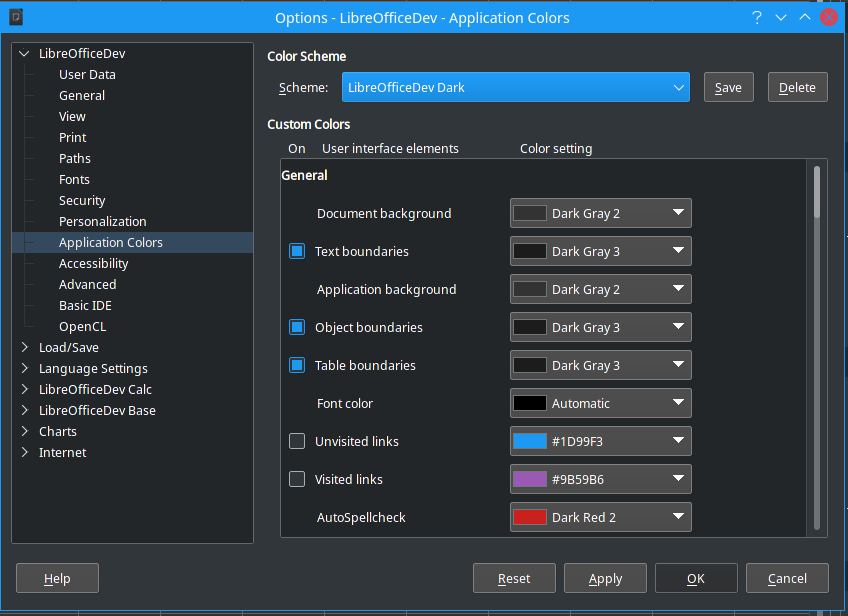
LibreOffice 7.2 is here with a long list of changes and improvements
Serving as a handy reminder that Microsoft Office is certainly not the only office suite out there, LibreOffice 7.2 has landed. There are a sizable number of changes in this latest version of the free, open-source office software including support for Apple M1 chips.
While there are lots of under-the-hood changes that are concerned with optimization, stability and improving compatibility with Microsoft Office, there are also plenty of things which are rather more obvious. This includes a new LibreOffice Dark theme, and a new batch of templates.

Why big data warehousing is the next frontier for boosting CX
It’s been decades since the term "the customer is always right" placed customer experience (CX) at the heart of every transaction, but delivering excellence in CX hasn’t become much simpler with the passage of time.
Customers effectively expect businesses to read their minds, and they don’t have much patience for those that fail. A recent PWC survey concluded that one-third of consumers would abandon a brand they love after just one negative experience, showing just how high the bar is set for CX.

6 developments in autonomous tech, coming soon
As more industries find themselves searching for viable solutions to common problems, they look towards automation. The concept of artificial intelligence (AI) has evolved over the years, and new applications for automation are emerging. It seems as though the world is moving towards automation rapidly, and industries will need to adopt this technology to stay ahead of the competition.
Continue reading to learn more about six autonomous technologies being developed that will change the way industries operate. They will contribute to higher levels of efficiency and productivity by complementing existing technologies.

How full-text search engines improve productivity at work
Entering the era of private space travel, you’d think that even if the rest of us can’t yet launch into orbit, at the very least we could make our lives easier through instant search across terabytes of up-to-date enterprise data from any place we may happen to visit on this planet. The good news is, with enterprise search software and a search index, we can make Earth that much more habitable while we await own spacecraft.
Now you may look up at the stars and wonder: what is a search index? A search index is not like the type of index you’d find at the end of a large book. Instead, it is simply an internal tool for storing each unique word and each unique number across an enterprise dataset, and the locations of all words and numbers in the data. The sole purpose of the search index is for the search engine to comprehensively search across everything, processing as many search requests as come in at any one time.

Despite the headlines, there's no need to feel hopeless about cybersecurity
The recent Colonial Pipeline attack set off gasoline panic-buying on America’s East Coast and reportedly cost the company $90 million in ransom. An adversarial nation’s Sunburst hack penetrated major U.S. corporations and key government agencies with repercussions yet unknown. Looking at these and other incidents, friends and customers have asked me, "What’s the use? Why bother? If these powerful organizations can be held for ransom or lose key data, what chance does my organization have to defend itself?"
I understand the feelings of helplessness behind the question. It can sometimes seem cybersecurity experts are preaching fire safety while all around us the house is burning down.

Supply network mapping more important than ever
Supply chains have been mapped for forever, but now technology is being increasingly involved in network mapping. Supply chains are evolving due to factors around them which might be political, economic, production-based, or, as seen this year, because of a pandemic. Covid-19 exposed the fragility of many modern supply chains with businesses relying on imports from different countries at a time when manufacturing was decreasing.
Within the wines and spirits industry companies across the world are scaling up their production, streamlining their supply chains, and expanding globally to become more efficient with their suppliers. It’s more important than ever to have an understanding of where everything comes from. You only have to look at the 2013 horse meat scandal to see why knowing your product’s origins is vital.

