
Six ways GRC tech can help organizations meet CMMC requirements
All organizations have to monitor and protect data. But, monitoring and protecting data is even more essential for those that work with the Department of Defense (DoD). The DoD has witnessed a growing number of threats, vulnerabilities, and cyberattacks aimed at its contractors. As a result, the DoD has established a framework for companies to adhere to, to prove compliance in protecting defense data.
The framework is called Cybersecurity Maturity Model Certification (CMMC). And, like CCPA or HITRUST, specifies a unified set of cybersecurity standards required by all DoD contractors by the end of 2020. While old DoD compliance standards allowed self-certification, CMMC requires third-party validation to compete for government contracts. Certified organizations must be audited every three years to verify ongoing compliance.
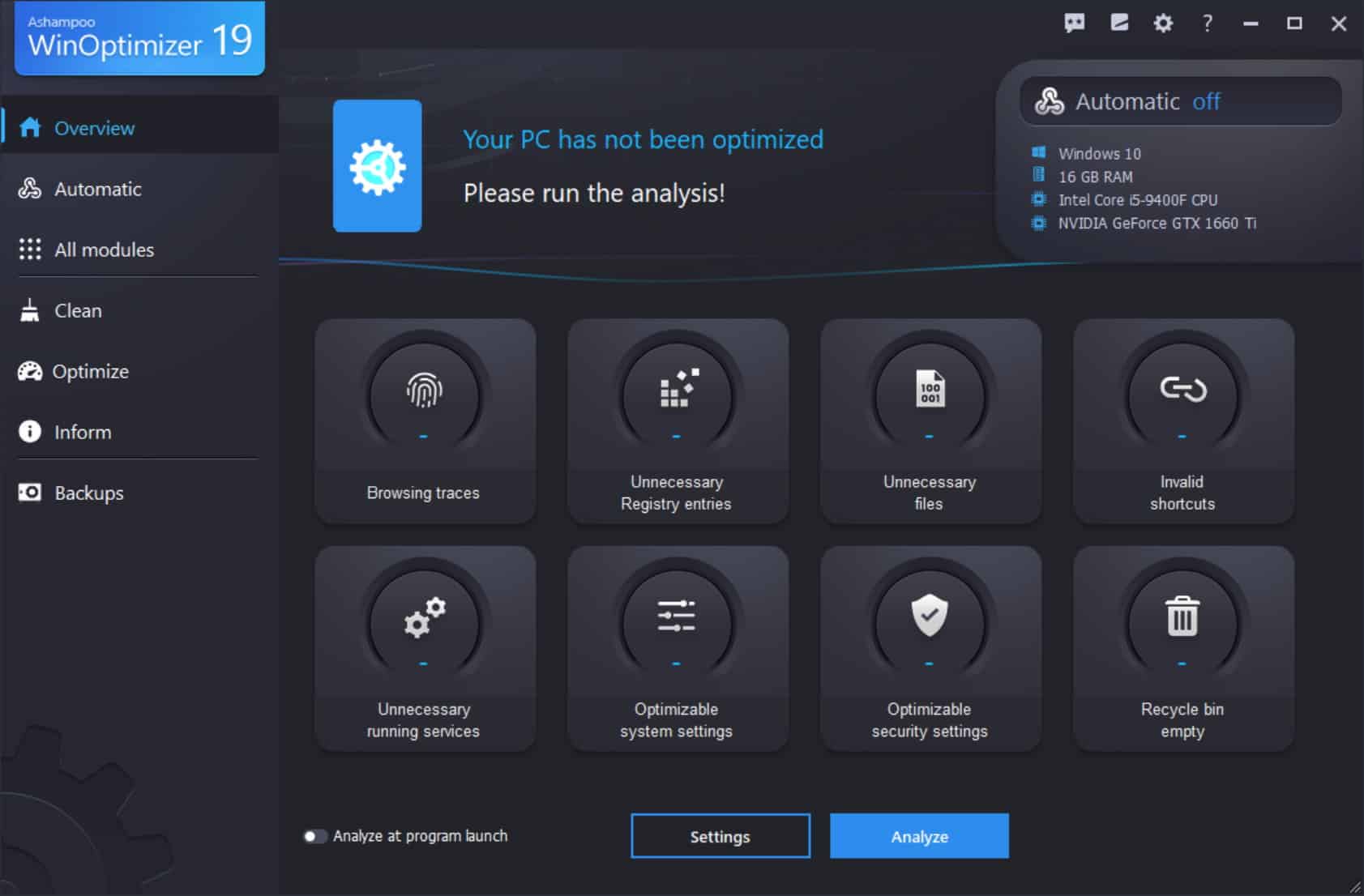
Ashampoo WinOptimizer 19 brings better clean-up, speed-up and optimization tools to Windows
You've almost certainly noticed that your once speedy computer is no longer the impressive beast it used to be. You could, of course, consider upgrading a few hardware components, or even invest in a new system altogether, but this is unnecessary expense. Turn to the newly released Ashampoo WinOptimizer 19, and you may find that all of your problems are solved.
This stalwart of the world of system optimization is back in an updated version that improves on existing tools, adds new options, and gives you everything you need to boost your computer. The focus is on improving speed and overall system performance, but Ashampoo WinOptimizer 19 will also help you to reclaim disk space, improve privacy settings and take control of telemetry.

Five compelling reasons to migrate to Atlassian Cloud
Last October, Atlassian’s CEO Scott Farquhar announced that Atlassian Server was reaching end-of-life (EOL) and customers have two options: either migrate to Atlassian’s own public cloud solution or move to Atlassian Data Center.
To ensure customers have plenty of time to consider these options, Atlassian is taking a phased approach. Since February 2021, organizations are no longer able to buy new Server licenses. However, they can still upgrade or downgrade their Server products until February 2022, and they can renew and receive maintenance and support for their licenses until February 2024. In practical terms this means that most customers with large data migrations will need to migrate to either Atlassian Cloud or Atlassian Data Center by Summer 2023.

Digital transformation: How COVID forced change across the business landscape
One of the most prolific business trends to come out of the pandemic has been that of digital transformation. COVID-19 forced change across the business landscape, and the sudden scramble to go digital has completely altered the way companies do business. Whether it be internal changes through productivity tools or security, or external changes in how businesses interact with customers, we can see that some type of digital transformation has taken place in almost every business vertical.
In the pre-COVID era, businesses only called upon their digital transformation capabilities occasionally. In a 2018 Tech Pro Research study, about 70 percent of organizations surveyed confirmed having a digital transformation strategy already in place, or were working on one. However, they also reported challenges in buy-in and funding. Then, almost overnight, digital transformation was quickly adopted as the spread of COVID-19 shut down regular work functions. As companies were pushed into exploring digital solutions, organizations found new ways through this digital transformation to continue business, serve clients and keep their employees safe.

Is digital transformation the answer to the recovery of SMEs?
Small to medium enterprises (SMEs) are essential to the UK economy. The government has noted that they contribute to 99.9 percent of all private sector business in the country with a turnover of £2 trillion.
However, entering the largest recession since records began and even after unprecedented financial help, small firms remain at risk of failure in navigating their business through the pandemic. The current situation has rapidly changed the way that we interact with customers, how consumers buy, and the interests of clients and customers alike.

Reimagining the network for the cloud
In every IT era we overestimate our ability to put new technology to work. The cloud is no different -- it still takes too long to build even rudimentary networks in the cloud environment. Think about all those VPNs that were built in 2020. You need to buy a box, certify, test, deploy, sort out licensing. It’s weeks or months for a solution that provides a level of security (up to a point) but little flexibility or performance. When the business needs changes, you need to do it all again.
What you want is a holistic environment with all the advantages of a data center but none of the drawbacks of centralization. You need something that connects you not just to, but through the cloud, out to the edge and to wherever your people and partners are. You want to be able to manage this as effectively as an on-prem system even though it’s massively distributed. You need to know what’s going on everywhere, so you need complete security, visibility and management controls that treat the entire cloud as a single entity even if it encompasses multiple public and private clouds. You also need to be able to secure it and apply all the governance and controls needed to satisfy regulators and your auditors.

Into the future: Amazon and the rise of personal healthcare
For 100 years, retailers have segmented the broad marketplace into groups -- soccer moms, or Millennials, or New Yorkers, or readers… pretty much every retailer uses target segments like those. But Amazon has never been interested. Instead, it wants a segment of one: you. It gathers information about what you look at, what you buy, your browsing habits. To that it adds information from your purchases -- address and credit cards on file -- as well as your Amazon address book to find those close to you.
It is also the second biggest tracker on the web, after Google, so it follows your activity far beyond the Amazon ecosystem. And it can access the standard sets of information that can easily be sucked in from outside: your credit score, your home ownership, criminal complaints and records…. Amazon probably knows more about you than any other entity on the planet, including your mother and your spouse.

The future of service management in the DevOps era
Whether you view your organization as having an agile approach or not, in 2020, companies had no choice but to drastically change their way of working as the world rapidly pivoted to remote working. Organizations that had already embraced agile principles had the advantage of being able to adapt faster to the pandemic and meet the demands of their employees, who were suddenly all working from home.
Now, as we start to slowly emerge from multiple lockdowns and restrictions, one interesting side effect of COVID-19 is that it has lowered our collective tolerance for slow, overly bureaucratic processes. We all crave an agile approach, whatever our definition of agile might be.

The challenges of digital transformation
The goal of digital transformation is to fundamentally change how B2B suppliers operate and deliver value to customers by creating a connected digital ecosystem. A change of this magnitude, however, is not without its challenges.
For one, in order to change a business’s value delivery model, the first step is understanding the value each customer is looking to receive -- something that is easier said than done when there is no formal way to document and collaborate around goals and objectives.

Playing hide and seek with your data? Here's how to find that critical piece of information on your intranet -- even from a tunnel with no online connection
No matter your job, it likely requires immediate answers from your enterprise Intranet. Indexed enterprise search lets you find what you need from anywhere, while cached indexed enterprise search lets you find what you need even when you are offline.
Together, these two components can help resolve what feels like a never-ending game of file hide and seek.

Why senior management needs to make cloud backup a priority
At work and at home, backup is critical. From making photocopies of significant documents to digitizing old family photos, relying on hard drives to replicating servers, we all know that it’s important to have multiple copies of the information that matters to our families and our businesses. Knowing we should do something, however, isn’t the same as doing it consistently and well -- which is why backup often fails.
Many organizations still rely on outdated backup strategies that put the company at risk from cybercrime, human error, physical disasters and more. But because the business "already has a backup plan", or because backup isn’t a shiny new object, it can be difficult to convince senior management to make it a priority.

Reducing the carbon footprint of AI: The debate continues
The debate about the energy greediness of large AI models is raging. Recently, an AI ethics researcher at Google was dismissed because she had pinpointed the upward spiral of exploding training data sets. The fact is that the numbers make one’s head swim. In 2018, the BERT model made the headlines by achieving best-in-class NLP performance with a training dataset of 3 billion words.
Two years later, AI researchers were not working with billions of parameters anymore, but with hundreds of billions: in 2020, OpenAI presented GPT-3 -- acclaimed as the largest AI model ever built, with a data set of 500 billion words!

How biometrics is moving from verifying identity to verifying humanity
Even though 'face spoof' sounds like a piece of skateboarder terminology used to describe a particularly vicious wipeout, it’s actually something more commonly dealt with by InfoSec professionals who work for huge banks, telecommunications companies, and healthcare providers.
Simply put: it’s when a scammer uses a 3D mask -- or a printed or on-screen image -- to fool biometric security measures a la "Mission Impossible" in order to gain access to the system those security measures are in place to protect.

How to reduce the carbon footprint of AI?
Can artificial intelligence be deployed to slow down global warming, or is AI one of the greatest climate sinners ever? That is the interesting debate that finds (not surprisingly) representatives from the AI industry and academia on opposite sides of the issue.
While PwC and Microsoft published a report concluding that using AI could reduce world-wide greenhouse gas emissions by 4 percent in 2030, researchers from the University of Amherst Massachusetts have calculated that training a single AI model can emit more than 626,000 pounds of carbon dioxide equivalent—nearly five times the lifetime emissions of the average American car. Who is right?

The advancement of penetration testing throughout the pandemic
COVID-19 threw the spotlight on cybersecurity like never before. The unprecedented global shift to remote working and subsequent surge in cyber crime, drove a priority focus amongst business leaders to ensure a robust cybersecurity posture across every part of their newly extended network. Many organizations had to make this transition rapidly, which increased the likelihood of misconfigurations and other errors, while the drastically increased attack surface presented fresh cybersecurity challenges around remote network connections, VPN connections, phishing, and many other types of network attacks.
Ensuring adequate protection against this wave of new security threats facing every size and shape of business became paramount and challenged CISOs to balance reduced budgets and staff against the requirement for increased technology investment.

