
From digital revolution to evolution: How IT leaders can implement small-scale change for long-term benefits
The popularity of cloud is self-evident. A recent IDC report showed that spending on shared cloud infrastructure reached $13B in Q3 2021, an increase of 3.6 percent from Q3 2020. Additionally, according to IDC projections, cloud spending in 2021 is expected to have increase by 8.3 percent in 2021 compared to 2020. Cloud adoption of is no longer a competitive differentiator, particularly in the wake of the pandemic rush to digitization.
Business success is in the details. Large transformation initiatives such as cloud may be appealing, but in today’s climate of digital parity, these projects may not deliver the return on cost and time invested which leaders desire. To stand out amongst competitors, business leaders need to shift their focus from complete digital transformation to smaller, more incremental evolution.

Modern mentorships: Fixing the cybersecurity skills gap
With job vacancies currently outweighing the number of people available to fill them, a career in cybersecurity offers almost limitless opportunities. The 2021 Cybersecurity Workforce Study from (ISC)² estimated that there were 4.19 million cybersecurity professionals worldwide -- an increase of more than 700,000 from the year before.
While this illustrates an industry undergoing major growth, there remains a workforce gap of 2.72 million people which represents a very serious problem for organizations faced with a growing volume and sophistication of security threats.

Bridging the security gap in the software development life cycle
The timeliness of security checks during the software testing process is critical to more rapid and higher quality software development and yielding higher returns. Yet DevOps and security have historically struggled to integrate in the software development life cycle (SDLC). According to a Gartner study, through 2022, 90 percent of software development projects plan to follow DevSecOps practices, up from 40 percent in 2019.
With the increased risks of cyberattacks and pressure on DevOps teams to deliver software to faster timelines, the risks and consequences associated with flawed code and faulty infrastructure configurations cannot afford to be missed in the early development stages. So the pros of uniting these teams is clear, but the cons remain costly and their discord could hold organizations back by making software deployment faster but in doing so releasing security vulnerabilities.

Addressing cybersecurity vulnerabilities does not have to be a losing battle
Many companies share the opinion that they are fighting a "losing battle" against cyber threats and security vulnerabilities. The threats are endless, and they are only getting more aggressive and difficult to counter.
This sentiment is echoed by the most recent edition of one annual security report (Priority One Report 2022), which describes 2021 as a banner year for cyberattacks. There is a sense of collective pessimism in being able to sustain cyber defenses, which cost hundreds of thousands of dollars yearly.

Release management through the eyes of DevOps
To drive cost efficiency, organizations need a process in place designed to manage and schedule the rollout of mission-critical software updates and releases to the production environment -- this is where release management comes into play.
Release management is introduced to solve problems, but it must be approached in the right way to succeed effectively. Many of the challenges that businesses face with their software releases in traditional operating environments stem from a disconnect between the development and IT operations teams. To bring these two differing sides together, many have implemented a DevOps methodology as a way to break down the existing silos and provide more value quicker and with fewer risks by balancing throughput and stability.

Managing AI risk: What are you waiting for?
Recent headlines have brought much-needed attention to questions surrounding algorithmic fairness. Regulators are taking notice. To date, EU officials put forth proposed language for aggressive new AI oversight. The Federal Trade Commission has published governance principles on the responsible use of AI, holding that existing law already empowers U.S. regulators to take corrective action. Additionally, a panel of AI experts testified before Congress about the potential inequities of algorithmic decision systems.
Many argue that increased regulation could stifle innovation, putting some nations at a disadvantage in the global arms race for AI dominance. But if the alternative is to do nothing, we could be creating even bigger risks, threatening our fundamental principles of fairness and equality.

Navigating the complexities of securely transmitting digital documents
Sending and receiving important, mission-critical, or time-sensitive documents -- whether as an email attachment, via a file-sharing app, or as a digital fax -- is today a critical component of business processes and communication.
Digital documents are now a primary form of business communication, and everything from contracts to proposals and RFQs should be considered data that is governed by compliance and security regulations. Let’s examine the four leading considerations for businesses when it comes to secure digital document transmission.

What's in store for intelligent search in 2022?
The past year has brought significant changes to the digital workplace, with the sheer volume of data overwhelming workers, and increasing by the minute. To keep afloat under the hybrid working model, enterprises need new tools and technologies to handle disorganized masses of information without getting lost.
Moreover, the transformation of the digital workplace continues to be a top strategic priority of enterprise and IT leaders. Recent research from Gartner has shown that 58 percent of board members ranked digital technology initiatives as their top business priority this year.

Is Kubernetes the right fit for your IT?
Kubernetes is a standardized, open-source program for managing containerized workloads and programs. It is claimed to be many things -- and has a great many fans in the tech space, and for good reason.
It has a whole raft of benefits. It is incredibly efficient, improving workloads and response times across broad IT infrastructures, and ultimately resulting in more portability (although not a cure), shortened software development cycles, and reduced cloud-data consumption. Naturally, this in turn leads to quicker and cheaper IT projects.

What has Covid taught us about tech?
As we move into 2022, perhaps the biggest change we have seen is the beginning of the end for traditional 9-5 working in favour of anytime working. Much has been made of agile and remote working with a great deal of the focus being on physical location, but the knock-on effect this has on working hours and the technologies we utilise is huge.
The act of walking in and out of an office (or perhaps the commute) for most gives a clear beginning and end to the working day. In the hybrid working world these once black and white edges to your day become greyed. Today, with laptops firmly in place and collaboration tools delivering work into your home mean that work is never more than a couple of steps away.
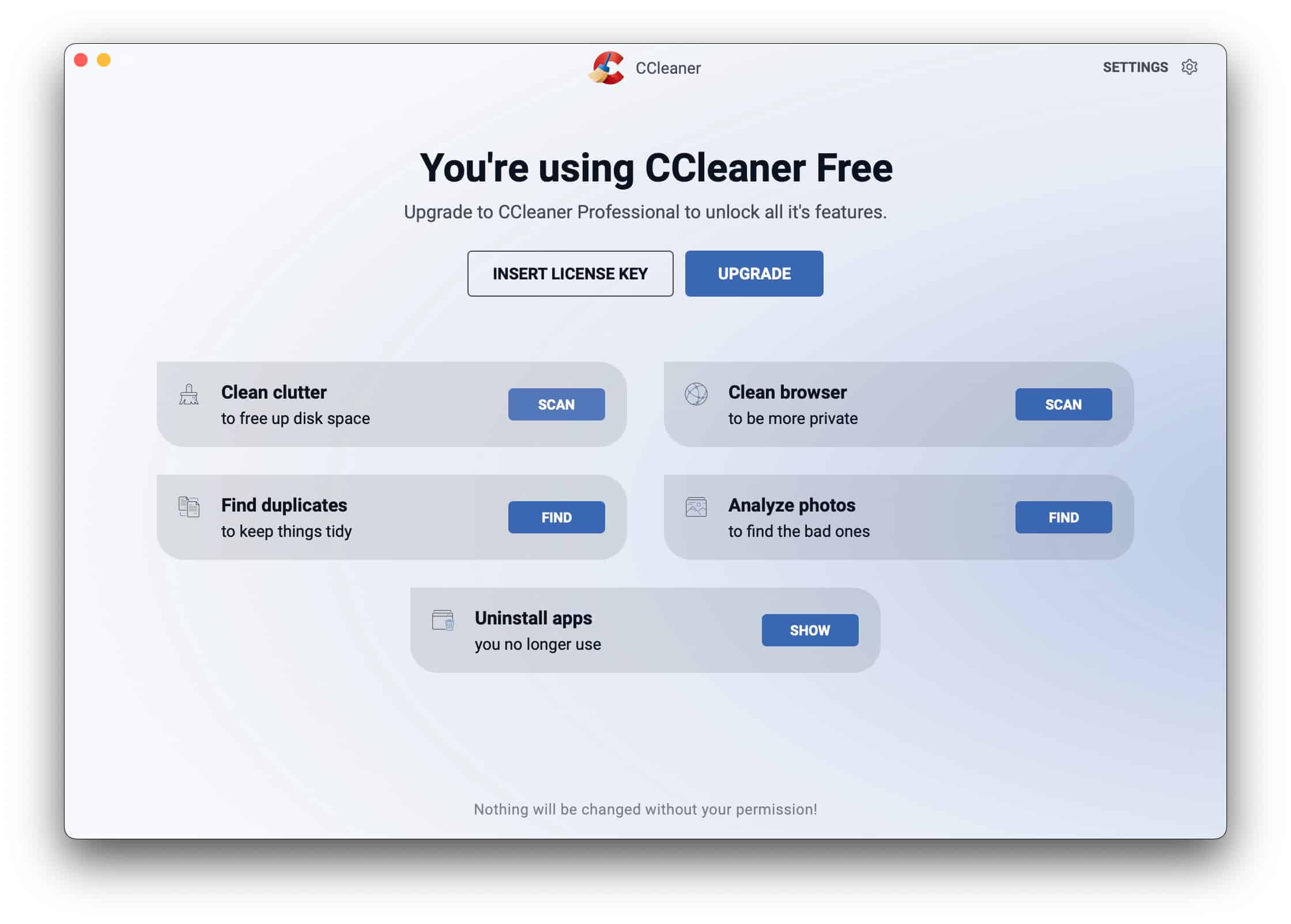
CCleaner for Mac 2 with added photo analysis tidies up macOS better than ever
There is an updated version of CCleaner for Mac available, complete with some major improvements and additions which help to make this essential optimization tool even more useful. There are Free and Professional versions of the software to choose from, and both have undergone major developments.
Both editions of CCleaner for Mac 2 feature an updated tool for analyzing hard drives and determining which files and apps can be safely removed to free up space. There is also an enhanced browser cleaning option to help improve your privacy, and the Professional version includes amazing new tools for cleaning out poor quality and duplicate photos.

4 strategies to avoid cybersecurity burnout
CSOs, CIOs and CISOs have never had it so tough. Alongside their traditional responsibilities, they must now face a cybersecurity threat environment that is growing exponentially, and a growing cyber skills gap. As a result, many of them are reporting burnout.
Today, ransomware has become one of the greatest network security threats organizations have to deal with. Increasingly sophisticated and distributed at a high speed via the internet and private networks using military-grade encryption, today’s ransomware attacks demand multimillion ransoms. Ransomware is expected to cost UK businesses around £15 billion this year and nearly £200 billion by 2031, and this is only one of the many threats organizations have to deal with.

5 critical errors to avoid when selecting your managed service provider
As customers demand personalized services, businesses are under increasing pressure to meet those demands. In turn, employees need support as projects grow more complex, and to meet the needs of both customer and workforce, juggling cloud management in-house can be a relentless headache.
In these situations, businesses seek the assistance of a managed IT service provider. These highly skilled technology partners specialize in simplifying the process and easing the headache. Ultimately, managed services free your staff from performing time-consuming tasks and allow them to focus on the core business operations instead.

How and why NHS Trusts must take a longer-term view over software procurement
Getting software right is no easy task -- especially in healthcare. It must be applicable to a near-endless list of users, applications, and contexts -- and these are constantly evolving. These inevitabilities, paired with the inherent difficulties of managing such a huge organization, unfortunately means that software is often not as effective as it can be -- and costs the UK's National Health Service (NHS) far more than it needs to.
The reasons for this are, of course, many, but the fix is remarkably simple; NHS Trusts must stop looking at the micro and the short-term, and instead think about how to procure software that is both flexible and delivers long-term value. Easier said than done, I know, but it is not impossible. Here are a few things to keep in mind when choosing software.

The future of business analytics will look similar to your favorite app
Imagine a world where more than 300 million people use analytics to make data-driven decisions every day, decisions that require digging through databases, combining multiple sources of data, and even the most advanced analytics techniques. Don’t believe it? This world already exists. Most of us just don’t know it.
Spotify currently has 381 million users listening to music and podcasts. Netflix just reported that it has 221 million subscribers streaming movies and shows across the globe. It’s estimated that 100 million people use an Apple Watch, and many more millions use other wearable fitness devices as well. The list goes on. These companies help millions of people discover new artists, find a show to watch, and even live healthier lives. Their users are everyday consumers, not business analysts or data scientists, and yet they’re somehow making decisions using insights based on the largest and most complex of data sources. If you want to see the future of analytics in business, look to the leading consumer apps.

