
How rampant robotic process automation (RPA) adoption is introducing new threat vectors
Robotic process automation (RPA) is nothing new. In fact, it’s an automation toolkit that was first introduced back in the 1990’s. But in 2020, in the midst of a global pandemic and the all new remote work norm, RPA interest and adoption hit a new high. Why? Because with RPA, digital workers are able to take over repetitive, manual tasks traditionally performed by their human counterparts -- freeing up time, energy and critical human resources.
Gartner’s Fabrizio Biscotti, research vice president, put it best: "The key driver for RPA projects is their ability to improve process quality, speed and productivity, each of which is increasingly important as organizations try to meet the demands of cost reduction during COVID-19. Enterprises can quickly make headway on their digital optimization initiatives by investing in RPA software, and the trend isn’t going away anytime soon."

Vulnerability management is complex, so how can we work smarter to reduce risk?
The saying "too many cooks spoils the broth" could well be true in the case of how we currently approach vulnerability management (VM). The process around vulnerabilities has become increasingly complex, with high levels of pressure to ensure that it is done right.
Vulnerabilities have long been one of the most prominent attack vectors, yet so many are left unpatched by organizations of every size and across every vertical -- the root of catastrophic issues. The Ponemon Institute conducted a recent study that found almost half of respondents (48 percent) reported that their organizations had one or more data breaches in the past two years. In addition, the discovery of high-risk vulns in 2020 alone, has drastically increased by 65 percent -- ultimately alluding to the fact that breaches could potentially become increasingly impactful. The longer a vulnerability remains present, the higher the chance that it will be exploited by bad actors.

Protecting your business' legacy systems from ransomware attacks
Despite the significant shift and adoption of new technologies over the past few years, many businesses still rely on legacy infrastructure. Legacy servers are often still in operation because they are far too critical, complex, and expensive to replace. Famous examples include Oracle databases running on Solaris servers, applications using Linux RHEL4, or other industry-specific legacy technology.
Although critical to the business, these legacy systems can increase a company's risk -- gaining access to just one unpatched legacy device can be relatively simple for cybercriminals. Once inside, said criminals will move laterally to gain a deeper foothold inside the network and deploy more significant attacks.

How to keep your hybrid workforce engaged
The way businesses operate has changed significantly since the first national lockdown in March 2020. But arguably one of the biggest changes has been the way businesses use technology. Data from McKinsey shows that businesses accelerated their digitization by three to four years in the first four months of the pandemic.
This adoption of new technology has not come without its teething problems, however, and this is especially true for businesses with large office contingents. These workers promptly switched to remote working in March 2020 and had to adapt to these technologies while working from home. Google data shows that searches for terms on how to use tools like Zoom rose exponentially during the first few months of the pandemic, with "how to use Zoom" increasing by 7,016.74 percent.

Why is API security failing? In part, because we're over-rotating on 'shift left'
The benefits of shift-left approaches in security are well-documented, to the point where they have become common practice. This practice helps ensure that more coding quality and security issues are found before the code is released into production, saving time and money and reducing risk. However, not all security risks can be identified and eliminated in pre-prod. This reality is particularly true with APIs, where the security risks associated with their widespread use and abuse is a significant concern. Experts from Gartner predict that by 2022, API abuse will become the most common attack vector.
Recent API incidents have already validated this prediction many times over. Starting in 2021, 90 percent of web-enabled applications will be exposed via APIs rather than the user interfaces. Without a balanced approach to protecting APIs, one that goes beyond just pipeline scanning and other shift-left practices, organizations will continue to suffer API security gaps that leave them exposed.
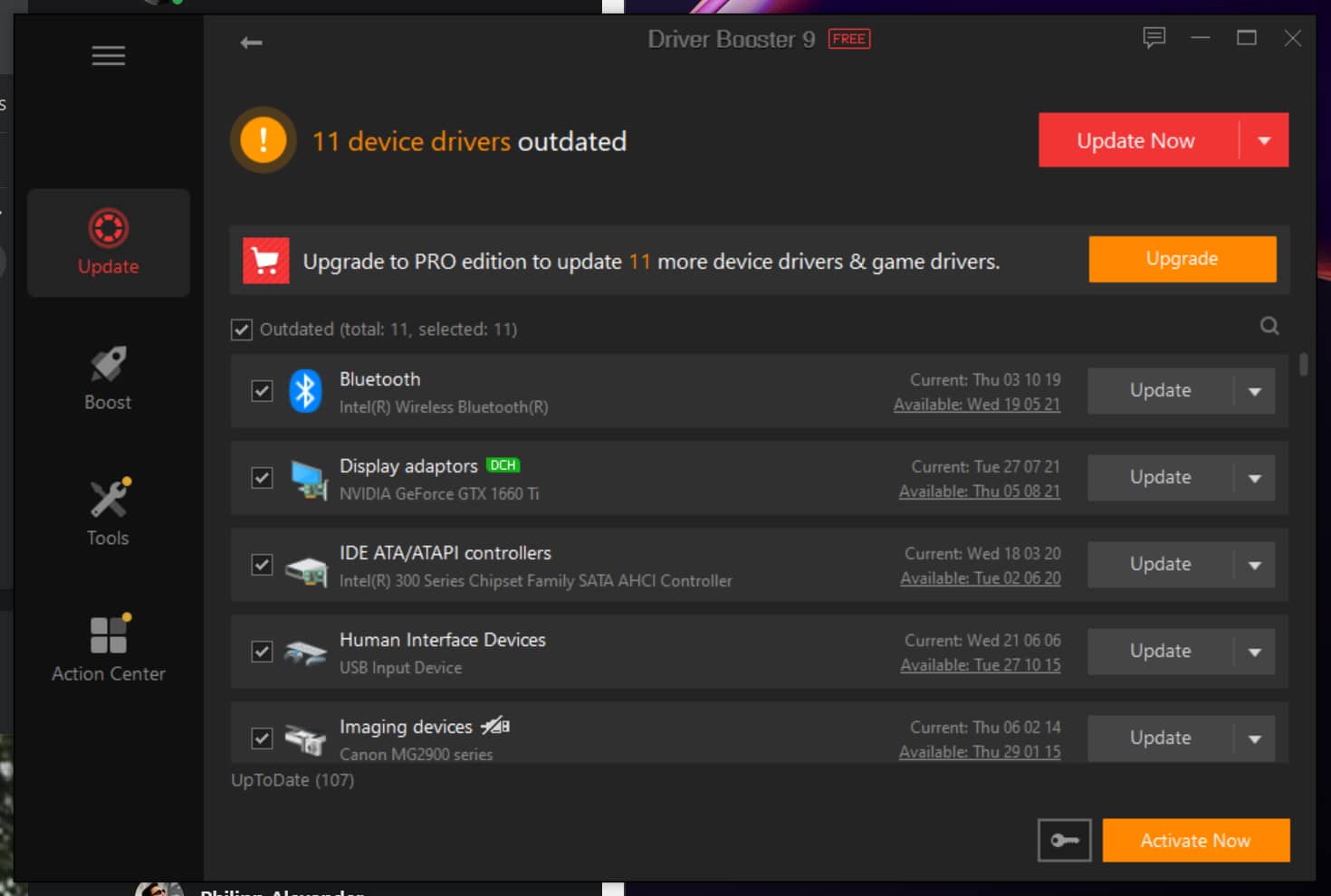
IObit Driver Booster 9 is Windows 11-ready and packed with problem-fixing additions
Whether you like it or not, and regardless of whether you know anything about them, drivers are absolutely central to Windows. Giving the operating system the ability to communicate with hardware and you the ability to tweak and control settings, drivers are essential for day-to-day computing, and keeping them up to date is important.
Driver updates not only add new features and improve performance, they can also help with stability and security. And this is why IObit Driver Booster is so helpful; it ensures that you always have the very latest drivers installed and fixes a range of driver-related issues. Version 9 of this essential tool has just been released, and it is even more powerful than before.

Cloud is costly, but it shouldn't have to be
Cloud's meteoric rise to become the dominant system for IT infrastructure has only been accelerated by the pandemic. The capacity of the cloud to rapidly run workloads with flexibility and scale is something that is rarely matched by onsite IT infrastructure; a capability that has become more essential during the pandemic induced changes to working patterns and business operations. Indeed, according to Flexera’s 2021 State of the Cloud Report, 90 percent of firms slightly or significantly increased their cloud usage due to the pandemic.
As cloud services’ dominance looks set to continue, businesses are utilizing cloud platforms to drive innovation in emerging technologies. Businesses can now scale up their operations in areas like artificial intelligence with ease, allowing them to tap into fluctuating customer desires so as to deliver tangible value to the business.

Big changes coming to the App Store later this year
2021 has proven itself to be a big year for mobile apps, and for iOS the approaching changes are even more substantial. A long-awaited update is coming to the App Store, namely the introduction of an A/B testing tool that allows developers to directly test different treatments of their product page on App Store Connect.
Although A/B testing has been available for developers on the Google Play Store through Google Play Experiments since May of 2015, Apple has continuously fallen short in offering a similar feature that allows for convenient testing. Instead, developers on the iOS App Store rely on deploying new builds to compare metrics before and after, utilizing third-party testing, or using conversion optimization via Apple Search Ads creative sets. This is all changing with the introduction of Custom Product Pages and Product Page Optimization.

How cloud-based file systems can protect your business from ransomware
Ransomware has rapidly become the number-one cyber threat, with attacks becoming more numerous and aggressive -- a trend that’s not likely to change anytime soon. According to a report from SonicWall, during the first half of this year, ransomware attacks in Europe climbed an astonishing 234 percent compared to 2020, while U.S. incidents soared by 185 percent. Worldwide attacks weren’t far behind, up 151 percent from the same period the year before. The attackers are equal-opportunity criminals, striking organizations of all types and sizes nearly every week.
There are several reasons for the steep and steady increase. The surge in remote workers using poorly protected home systems and networks has created many more opportunities for hackers. At the same time, the growing use of cryptocurrencies has made it easier to extort payment. Emboldened by these trends, cybercriminals are becoming more aggressive, threatening to publish sensitive data if targets refuse to fork over the ransom. They’re also demanding more money; research from Unit 42 puts the average ransom payment in 2021 at almost double the prior year.
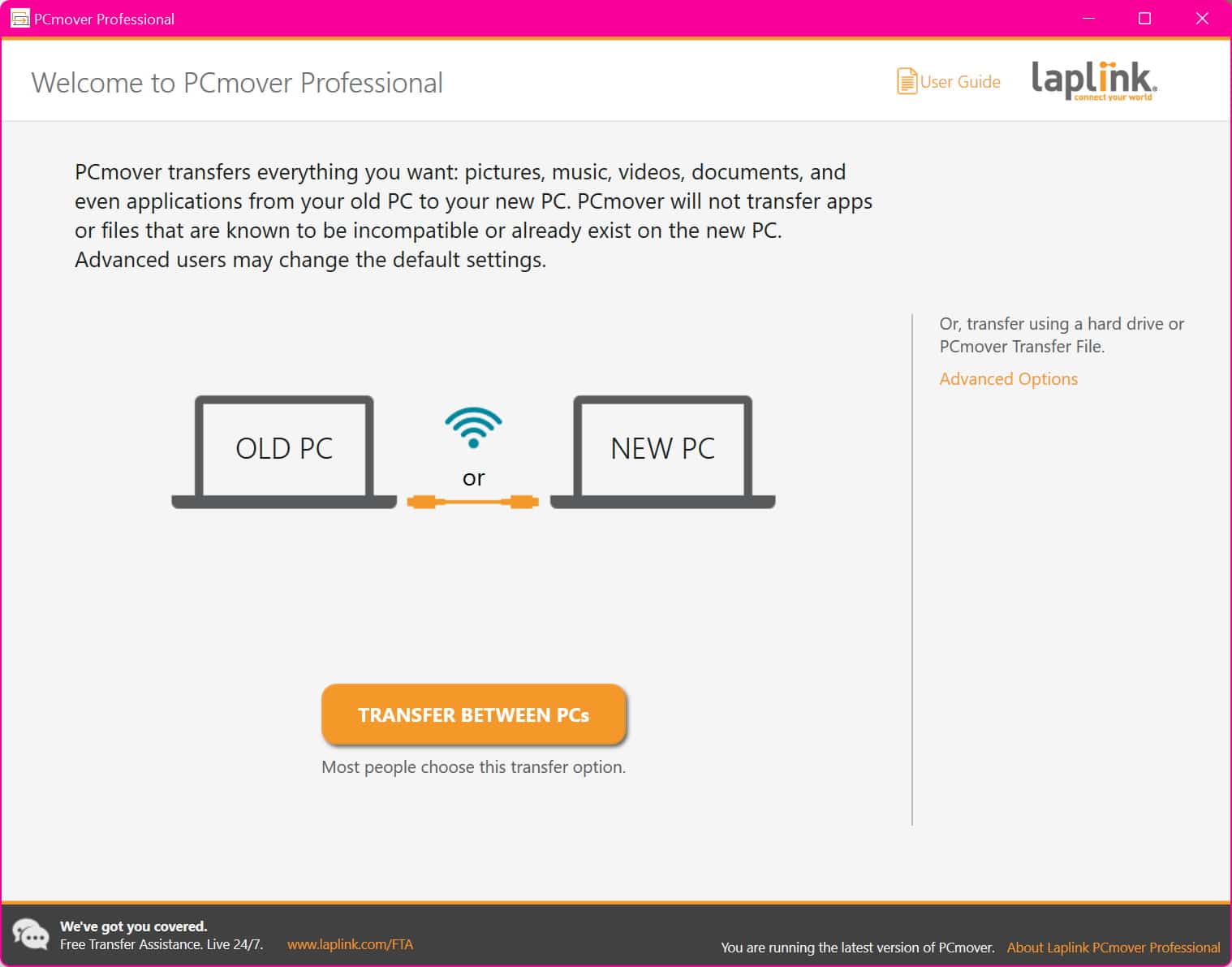
Take advantage of our special offers on Laplink PCmover and simplify migration to Windows 11
There is a lot of pleasure to be derived from buying a new computer, and this is particularly true when you invest in a machine with a brand new operating system. With Windows 11 having just been released, it's a great time to splash out on a new computer so you can use new hardware to take full advantage of everything Microsoft has crammed into the latest release.
But while exploring and using Windows 11 is great, there is the issue of setting up your new computer. This means installing all of the software you need, moving your files across from your old machine, and configuring all of the settings and personalizations you had put in place. Rather than doing all of this by hand, look no further than Laplink PCmover -- an incredible tool that will help you move everything you need to your new computer. And the great news is that you can save money with our special offers on the software.

Maintaining visibility through the growth of IoT
Data traffic rates over network backbones have increased significantly over the past several years. Fueled by the increasing demand of Internet of things (IoT) devices which continue to be more readily integrated with our daily lives, both domestically and commercially, the average annual volume of data/ information created has almost doubled over the past two years, from 41 zettabytes in 2019 to 79 zettabytes in 2021, with a forecast of growth to 181 zettabytes by 2025 (Statista, 2021).
Over the previous 18 months, this data rate has been driven further by the move to working from home (WFH) where people are using more digital technology, as well as purchasing new IoT devices to help make their WFH life more comfortable.

The continuation of remote work and the best digital tools for it
The onset of the coronavirus outbreak prompted the majority of businesses worldwide to shut down. As people get vaccinated and states lift masking and social distancing restrictions, more offices are reopening.
Some large corporations and even small to medium-sized businesses believe remote work was a positive change in the workforce and have decided to keep some employees home. A recent Gallup poll shows that 91 percent of people working remotely for some part of the week want that trend to persist after the pandemic.

Placing code ownership in developers' hands to improve security
At the root of most malicious hacks are vulnerabilities in the underlying software. This simple fact tells us that developers have a significant impact on security. When developers are supported by the right tools, they have the power to catch security issues early -- issues such as injection vulnerabilities or storing secrets in source files.
Taking such an approach allows organizations to fix vulnerabilities at the first point of entry as well as throughout the continuous integration/continuous delivery (CI/CD) workflow, which helps prevent damaging attacks from the very start.

Humans are predictable, even criminals
People’s lives are built around patterns and routines. Their routines are structured. After a while, they even become predictable. A change in routine, an abnormality, emphasizes the pattern itself. When we add a non-routine activity to our lives -- our actions usually indicate it will occur. For example, before a vacation we make plans, buy a ticket or book a hotel. Before we move to a new house, we usually visit the location several times, make money transfers and sign a contract.
In their study from 2010, Albert-László Barabási and his team studied the mobility patterns of anonymous cell-phone users and concluded that despite the common perception that our actions are random and unpredictable, human mobility follows surprisingly regular patterns. Their research eventually concludes that people’s movement patterns are 93 percent predictable.

You don't need tableau: How to integrate analytics into the apps you already have
In recent years, organizations have invested billions of dollars outfitting employees with traditional business intelligence (BI) tools. Yet, the vast majority of employees still have not bought into the trend. That's not because company BI and industry data underpinning those platforms aren't robust. It's because the analytics necessary to allow companies' knowledge workers to recognize shifting metrics, make timely business decisions and remain at the forefront at interpreting industry trends must be more intuitive and customizable than traditional platforms achieve.
Insight from nearly 2,000 knowledge workers compiled earlier this year by Hanover Research shows that virtually all of them spend time looking for information their BI platform doesn't provide. Three out of four said they would likely adopt a new analytics solution if it was embedded within an application. This reveals a disconnect between their desire to use data analytics in decision-making and the ability to draw upon intelligence tools at their disposal. To avoid such meandering on a one-size-fits-all pathway, instead, incorporate embedded analytics and seek deliberate functionality to achieve maximum value from BI.

