
New venture aims to completely rethink enterprise security
Up to now cyber security has generally taken a defensive approach to protecting data and intellectual property.
That’s set to change as a team of industry experts has got together to create a system that's aimed at dramatically improving the reliability and security of enterprise data and applications running in both cloud and conventional environments.

Tech companies like Facebook and Google lead the way in delivering LGBT equality in the workplace
US technology companies are setting a benchmark for those in other sectors to reach for when it comes to LGBT equality in the workplace. These are the findings reported in the thirteenth edition of the Human Rights Campaign (HRC) Foundation’s Corporate Equality Index. The HRC rates workplaces on lesbian, gay, bisexual and transgender inclusion and equality, and this year's report shows that there is now greater awareness and understanding of the transgender community.
The index rates companies using a variety of factors including the presence of non-discriminatory policies, the existence of transgender-inclusion healthcare, and whether or not there are guidelines in place to encourage transgender inclusion. This year there are a record number of businesses attaining a 100 percent rating, and 14 of these fall into the hardware, software and data services areas of the tech sector.

Splice Machine reduces the cost and complexity of building database applications
Databases are important to enterprises of all sizes, but building applications to exploit data effectively can be time consuming and expensive.
Now Splice Machine, maker of the only Hadoop RDBMS (relational database management system), is making its product publicly available for the first time. It will allow database architects and app developers to build real-time, scalable applications without the burden or cost of a traditional RDBMS.

Republicans vote against USA Freedom Act that would have limited NSA surveillance
A bill that could have curtailed the surveillance activities of the NSA has been rejected by the US Senate. The USA Freedom Act was blocked as a bloc of Republican senators voted against the Obama-backed bill. After the Edward Snowden revelations, there have been many vocal calls for the powers of the NSA to be reined in. This was the bill that was supposed to deliver, but right wing opponents referred to it as a "gift to terrorists".
The bill passed the House of Representatives in May and had the backing of many of the biggest technology companies. One of the main aims of the USA Freedom Act was to stop the collection of domestic phone records, but there were also implications for the agency's online dragnet-style data trawling. Now it seems that the fight for privacy starts afresh.

Businesses underestimating the Wi-Fi demand caused by BYOD
Enterprises continue to struggle with Bring Your Own Device (BYOD) as employees continue to demand the freedom that comes with mobility in accordance with new trends. Security has long been discussed as the primary challenge when it comes to BYOD. Yet, other reasons such as network access is fast becoming a key concern for IT departments but also the key frustration for employees.
When it comes to connectivity, employee expectation is that it just works and as such this expectation must not be overlooked when implementing a BYOD roll-out.

Jolla crowdfunds its first tablet, hits goal within hours
Crowdfunding a mobile device is a tricky thing to get right. Just ask Ubuntu maker Canonical. To make its Edge smartphone happen, it turned to Indiegogo to get $32 million, of which it only managed to raise (a record) $12.8 million. Its failure can be linked to the sky-high goal, a mistake from which Finnish mobile device vendor Jolla appears to have learned from.
Jolla is also turning to crowdfunding, for its first tablet called Tablet, but the goal it set, of just $380,000, is much, much, much more easier to reach. In fact, at the time of writing this article, Jolla has raised more than $490,000 (a figure that is quickly rising), with 21 days left until the crowdfunding campaign ends, on December 9.

Comodo 8 delivers smarter sandboxing
Comodo Group has announced the release of Comodo Antivirus 8 and Comodo Internet Security 8.
The new build brings smarter sandboxing with a new default "auto-sandboxing policy", keeping unknown programs isolated from your system.

Will LinkedIn make a move into the enterprise?
News surfaced this week that Facebook was considering a move into the enterprise sector with the imaginatively titled 'Facebook at Work'. Not a great deal is known about the service yet, but pretty much everyone is in agreement that it could provide interesting competition to incumbents like Microsoft and even the likes of LinkedIn.
It has long struck me as surprising that LinkedIn hasn’t made a similar move. Back in 2011 Jeff Weiner, CEO of the company, suggested that enterprise social tools was "an area where we want to add value". Yet so far we’ve seen nothing particularly interesting.

Celebrating 60 years of software
There's an old computing joke that says the difference between software and hardware is that hardware is the bit you can kick.
To celebrate software's 60th birthday business package selection specialist Capterra has produced an infographic charting the history of the bit you can't kick. It'll provide a trip down memory lane for anyone involved in computing.
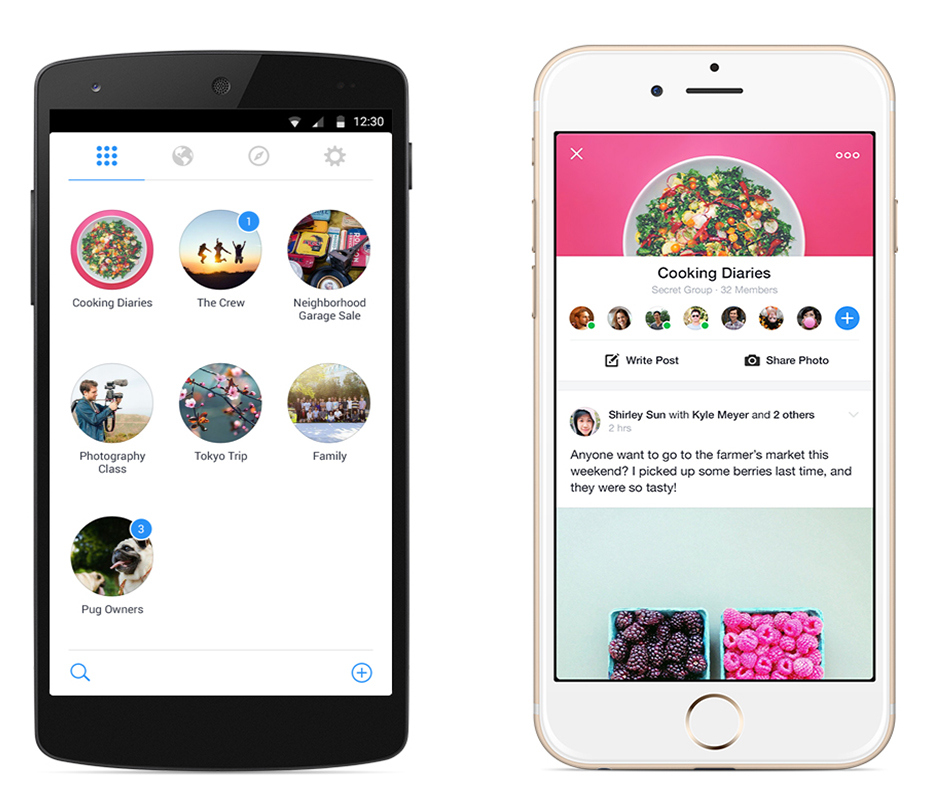
Facebook continues to show it 'gets' mobile with new Groups app
If you use Facebook on mobile, you will be familiar with Messenger, Facebook's separate app dedicated for messaging. While some people hated having to download another app, others enjoyed it -- including myself. Mobile is a world meant for apps that do one thing well. With a relatively small screen size, optimized apps have the best experience -- not ones that cram in all the functionality they can. Facebook is continuing to follow this philosophy with its new dedicated app for Facebook Groups.
The official Facebook app includes everything, however, the only thing it does well is allow you to browse your newsfeed. To view your Groups on the mobile app requires going into the 'more' tab and scrolling down to select a Group. With a new dedicated app, all you have to do is open the app and you have all your Groups laid out in a grid waiting for you. Also, I find using the Groups app a much more pleasant experience. There are nice animations, and easy access to notification and privacy settings, among various other small features.
Google Chrome 39 goes 64-bit on Mac, promises performance, stability improvements
Google has unveiled Chrome 39 FINAL for Windows, Mac and Linux. The big news with version 39 is the long-awaited arrival of a native 64-bit build for Mac users.
Unlike the Windows version, which offers both 32-bit and 64-bit builds, the Mac build is now 64-bit only, and existing users with supported Macs will be automatically upgraded to the new version.

New report claims 81 percent of Tor users can be identified
A new report claims that more than 81 percent of Tor users are identifiable using a method that threatens Internet anonymity.
The study, titled "On the Effectiveness of Traffic Analysis Against Anonymity Networks Using Flow Records", claims that a technique known as traffic confirmation can be used to identify users.

T-Mobile is making it rain free tablets on Black Friday -- here's how to score one early
Do you like free stuff? Of course you do -- everyone likes something for nothing. Hell, I go to Costco with no plans to buy anything; I just walk around eating all the free samples. Is it low class? Yeah, totally, but it's essentially a free buffet with a cornucopia of flavors -- Swedish meatballs, salad, granola bars and more.
Today, T-Mobile announces that it too is going the free route, offering a tablet at no cost! It is an Android tablet -- the Alcatel ONETOUCH Pop 7. Never heard of it? Me neither, but it actually looks pretty nice. It runs Android 4.2.2, has a dual-core processor and best of all, supports 4G data. Even though it is a "Black Friday" deal, the carrier will be offering it a week early. Will you be successful in scoring one?

PayPal comes to Pebble so you can pay while tracking perambulatory progress
Wearables are starting to come of age, and they're now about much more than just tracking blood pressure and distance while running. Today Pebble continues the expansion of its range of apps with the launch of a dedicated PayPal app. It allow for payments to be made at participating retailers and shows payment notifications so there's no need to rely on a phone.
Pebblers -- as PayPal insists on calling owners of the smartwatch -- now have the ability to make PayPal payments without having to reach into their pockets. The app can be used to pay with a payment code, or to check in to make a payment.
Microsoft and Opera agree to terms on App Store deal for Nokia phones
Microsoft purchased Nokia, in part, earlier this year and has now begun the slow process of making it their own. New phones are being rebranded, which is not particularly surprising. Though, parterning with Opera (yes, the browser maker) is bit of a shock.
However, today the Norwegian company announced a deal with the software giant to begin powering the app store on certain models of handsets.