
Flash! Savior of the enterprise storage market?
From being an expensive technology and something of a niche, flash storage is shifting into the mainstream, particularly in enterprises.
According to new research by IDC, although the technology has been available for a while, the adoption of flash-based storage is only now showing real growth thanks to falling prices and a growing familiarity with the benefits it offers.

BYOD and the issues of managing VDI and VDA
Software licensing is a complex area, even in organizations with a relatively simple IT infrastructure. Once BYOD (bring your own device) is added into the mix, this takes licensing complexity to a whole new level.
There is much debate over the actual take-up of BYOD. Some sources say adoption is "exploding", others say less than 10 percent of organizations actually have a BYOD policy in place. Regardless of what the true value is, we can expect an increased level of uptake, given the recent announcement of Microsoft Office for the iPad. So BYOD will become even more attractive to end users, and potentially make life even more difficult for the license manager.
For future computing, look (as always) to Star Trek
"The step after ubiquity is invisibility," Al Mandel used to say and it’s true. To see what might be The Next Big Thing in personal computing technology, then, let’s try applying that idea to mobile. How do we make mobile technology invisible?
Google is invisible and while the mobile Internet consists of far more than Google it’s a pretty good proxy for back-end processing and data services in general. Google would love for us all to interface completely through its servers for everything. That’s its goal. Given its determination and deep pockets, I’d say Google -- or something like it -- will be a major part of the invisible mobile Internet.

Edward Snowden claims NSA caused the 2012 Syrian internet outage
Edward Snowden has claimed that the US accidentally took most of Syria off the Internet while attempting to bug the country's online traffic.
Speaking to National Security Agency journalist James Bamford for Wired, the whistleblower claimed that a US intelligence officer told him that the NSA was responsible for Syria's disconnect from the web in late 2012, and not the Assad regime.

Man asks Siri where to hide the body after murdering roommate, Siri offers suggestions
Most of us are used to asking Siri where the nearest pizza place or supermarket is. He/she has become an almost indispensable part of some iPhone users' lives. But would you ever ask Siri how to hide a dead body? That's exactly what one Florida man did two years ago.
Pedro Bravo, 20, is currently standing trial accused of kidnapping and strangling his friend Christian Aguilar in September 2012 after an argument started over Aguilar dating Bravo's ex-girlfriend. One of the key pieces of evidence used by the prosecutors is a record of Bravo telling Apple's famous digital assistant: "I need to hide my roommate".

Panda 2015 consumer range now available
Panda Security has announced the launch of its 2015 consumer range, claiming that it’s "lighter, safer and easier to use than ever before".
Protection is improved with the new XMT (Extreme Malware Terminator) Smart Engineering engine. This isn't just marketing spin, either: the latest AV-Test and AV-Comparatives reports both saw XMT-powered products at the top of the list.
Spotify enhances merchandising push for artists
Selling music seems to be a lucrative business these days, at least judging from all of the streaming services flooding the market. So how does one manage to differentiate itself and set things apart from rivals like Rdio and Google?
Apparently, for Spotify, this means moving into the merchandise business -- a rather lucrative one, given the price of concert tee shirts at shows, though Spotify doesn't plan to profit from this endeavor.

Four simple steps for securing your smartphone or tablet
A friend of mine bought a new iPhone 5s recently, used it for just over a week, and then 'lost it'. It might have been stolen or simply misplaced, she has no idea. All she knows for certain is she no longer has it in her possession. That’s bad enough, but she spent much of the first week copying over photos and other personal data to it from her old phone, but didn’t devote any time -- at all -- to protecting the device.
So in other words, if someone else has her iPhone now -- which it’s pretty safe to assume is the case -- they also have access to everything on it, which could be potentially catastrophic for her. The thing is, it’s so easy to protect a smartphone these days it amazes me so many people don’t bother to take the following simple steps:

Gmail enables unicode recognition to block links to suspicious sites
Email can be inherently dangerous, as less savvy users can, and do, click links that can lead to nefarious locations on the web. The links are frequently a bit hidden -- characters are slightly altered, such as "0" instead of an "O".
Last week Google rolled out support for non-Latin characters, a great addition, but one that enhances this problem, as well. With that in mind, the company is attempting to protect its email customers, by now enabling recognition of bad links through Unicode checks.

myMail becomes most popular alternative email app for Android and iOS
Despite the rise of other forms of communication, email remains one of the most popular options, particularly for business. No surprise then that there’s plenty of choice when it comes to mail apps for your mobile device.
According to data from app analytics company Distimo, the myMail app has passed other options to become the most popular alternative mail app for both Android and iOS, behind only Gmail and Yahoo Mail.

Artificial intelligence in the enterprise -- what you need to know
Artificial intelligence (AI) has become a bit of a buzzword among technology professionals (and even within the mainstream public) but truthfully, most people do not know how it works or how it is already being integrated within leading enterprise businesses. AI for businesses is today mostly made up of machine learning, wherein algorithms are applied in order to teach systems to learn from data to automate and optimize processes and predict outcomes and gain insights. This simplifies, scales and even introduces new important processes and solutions for complex business problems as machine learning applications learn and improve over time. From medical diagnostics systems, search and recommendation engines, robotics, risk management systems, to security systems, in the future nearly everything connected to the internet will use a form of a machine learning algorithm in order to bring value. It is the same thing as for humans, we attend schools for many years and we gain practical experience in order to deliver some kind of value.
But what exactly is machine learning, how is it being applied within organizations today, and what does it mean for the future of business? It is becoming ever more crucial for enterprise leaders to understand machine learning, particularly the benefits that it can provide for companies today. Machine learning today is already allowing many businesses to achieve higher productivity and efficiency, innovating their business, and those that do not begin to explore this new tool ultimately are at risk for falling behind their competition.

It's a cyber stick-up -- state of infection report reveals rise in ransomware
Ransomware is on the rise according the the latest report from enterprise threat protection specialist Damballa, with an increase in average daily infections of the Kovter infection of 153 percent between April and May this year.
Kovter is "police ransomware" that displays fake legal warnings about pornography. At its peak of activity in June it was recording almost 44,000 infections per day. But while Kovter was thriving CryptoLocker was dealt a blow by the taking down of the GameOver Zeus botnet.

Windows 8.1 August Update arrives -- minor improvements and bug fixes the order of the day
Microsoft’s long-awaited "Update 2" for Windows 8.1 users has materialized in the guise of August 2014 update rollup for Windows 8.1 and Windows Server 2012 R2. Also available separately for 64-bit Windows, the update is currently listed under optional updates in Windows Update.
The update is not as major as the previous Update 1 release, but does nonetheless contain a number of improvements and tweaked features.

Amazon holds a Fire (TV) sale, celebrates new apps
The Amazon Fire TV has become a solid competitor in today's set-top box market, competing with Roku, Apple TV and others. It works especially well for those who are Prime subscribers, as the service is completely integrated into the tiny box.
But Prime is not all you can do with Fire TV, other apps, like Hulu and Netflix, were available at launch and Amazon promised more on the way. That time has arrived, and the company is celebrating in its usual manner. That is, offering discounts on the device.
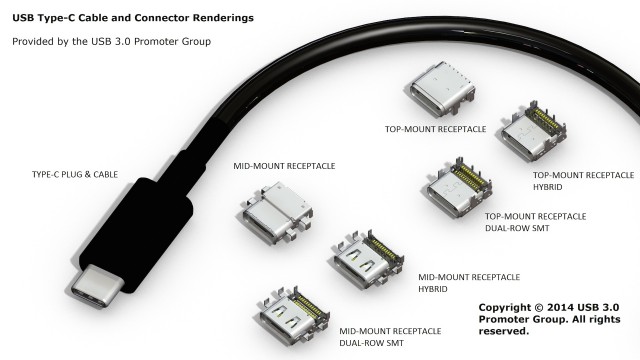
Get ready to enjoy that reversible USB Type-C connector
USB 3.0 Promoter Group announces that the much-awaited USB Type-C connector, which can be plugged in both ways, is now finally ready to enter mass production. It makes way for faster transfer speeds, courtesy of the USB 3.1 standard, increased power delivery, more compact device designs and, arguably, fewer moments of frustration thanks to its reversible orientation, which is similar to that of Apple's Lightning connector which launched in 2012.
"Interest in the USB Type-C connector has not only been global, but cross-industry as well", says USB 3.0 Promoter Group chairman Brad Saunders. "Representatives from the PC, mobile, automotive and IoT industries have been knocking down our door anticipating this new standard. This specification is the culmination of an extensive, cooperative effort among industry leaders to standardize the next generation USB connector as a long-lasting, robust solution". Here is what else you should know.