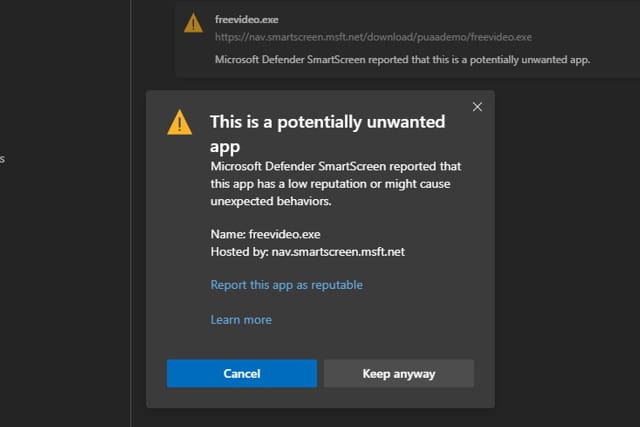
Updated Microsoft Edge will protect you from malware, crypto miners and more
With the switch to the Chromium engine, there's a lot more to like about Microsoft Edge these days. Microsoft is now pushing the browser hard, with the promise of serious speed improvements being used as a lure.
The latest update offers something extra -- protection against potentially unwanted applications (PUA). Microsoft Edge will now step in and block adware, cryptocurrency miners and other unwanted nonsense, particularly when downloading free software. The Microsoft Edge Team explains how to get the most from the protection.

Blacklisted apps in the Google Play store decrease by 76 percent
Despite a surge in app usage, with consumers downloading over 200 billion apps and spending more than $120 billion in app stores worldwide in 2019, Google's new security controls mean blacklisted apps available in the Play store dropped 76.4 percent.
The latest Mobile App Threat Landscape report from RiskIQ shows total blacklisted apps across all stores are down 20 percent.

Malwarebytes launches enhanced business cloud platform
Malwarebytes is today launching a new set of enhanced enterprise features for its business cloud platform, Malwarebytes Nebula.
The platform offers cloud delivery and management across the entire Malwarebytes’ product portfolio including Incidence Response, Endpoint Protection, and Endpoint Detection and Response. Native capabilities include guided UI, threat reporting, and simple API integrations, which enable security teams to overcome gaps in team experience and bandwidth.

Integrated attack simulations help protect against cyber threats
Security teams can often spend as much time managing security tools as they do defending against threats, and this can lead to extra risk such as misconfigured controls.
Enterprise security company ReliaQuest is introducing a new capability to its GreyMatter platform. Called Verify it uses both provided and customizable attack simulations to verify that security investments are performing as expected.

Shadow IoT threatens enterprise security
A 1,500 percent increase in IoT traffic over the past year and a rise in unauthorized devices being used in the workplace represents a major threat to enterprise security, according to a new report.
The latest IoT report from cloud security company Zscaler reveals its customers are now generating more than a billion IoT transactions each month. Analysis of just two weeks of this traffic through Zscaler cloud found 553 different IoT devices across 21 categories from 212 manufacturers.

FCA reveals data breach that exposed personal details of people complaining about UK's financial watchdog
The UK's financial watchdog, the Financial Conduct Authority (FCA), has revealed details of a data breach that took place last year.
The FCA says that personal details of people who had made complaints against the watchdog were exposed following the online publication of a response to a Freedom of Information Act request. Among the exposed information are the names and numbers of those who had lodged complaints.

Mozilla is enabling encrypted DNS-over-HTTPS (DoH) by default for US Firefox users
Firefox users in the US will soon have DNS-over-HTTPS (DoH) enabled by default. Mozilla is in the process of rolling out the privacy- and security-focused feature after an intensive period of testing.
DoH is an option for anyone outside of the US, but it will have to be manually enabled. Once enabled, DNS lookups are routed through Cloudflare or NextDNS using an encrypted HTTPS connection, hiding it from third parties such as your ISP.

The challenge of obtaining visibility into cloud security
Digital criminals are increasingly pivoting to the network after initially attacking an endpoint or publicly accessible cloud. Indeed, a network foothold enables attackers to move laterally to more valuable cloud workloads. They can then steal their target organization’s sensitive information and monetize it in whatever way they deem fit.
Many of us are fighting back against the threat of lateral movement by augmenting our visibility over the network. However, we’re constantly running into challenges in the cloud. When using AWS Virtual Private Cloud (VPC) or Azure Virtual Networks (VNets) to detect threats in network traffic, for instance, we’re missing packets’ application-level context. We thus can’t detect the malicious activity that hides within them. In this post, we will discuss why achieving visibility into the cloud continues to pose a challenge. We’ll then explore how we can gain the requisite level of visibility in the cloud.

New biometric solution guards email against account takeovers
At the root of most data breaches is a compromised account, but these can be very hard to identify, often coming to light only after they've been used to steal data.
Email security specialist GreatHorn is launching a biometric solution that effectively identifies compromised accounts and blocks takeover attempts by validating users using their unique typing patterns.

Cisco launches new cloud-native security platform
As businesses move into the cloud and expand their use of IoT devices, protecting their systems becomes much more complex.
To address this problem Cisco is launching a new integrated cloud-native security platform, Cisco SecureX, aimed at improving visibility, identifying unknown threats, and automating workflows to strengthen customers’ security across network, endpoint, cloud, and applications.

Vectra helps enterprises protect against Office 365 breaches
As more services move to the cloud, enterprises are exposed to increased risks from data breaches, and around 40 percent of organizations have suffered from Office 365 account takeovers.
According to Microsoft's Q3 2019 earnings call, there are more than 180 million monthly users on Office 365, which means there's a big attack surface out there for cybercriminals. That's why threat detection and response specialist Vectra AI has announced a new tool to help businesses protect themselves.
Malicious apps found on Google Play Store despite new App Defense Alliance
Researchers at Check Point have recently found eight malicious apps containing malware on the Google Play app store, despite Google forming the App Defense Alliance in November 2019 to improve security of apps in the store.
The apps were camera utilities and kids' games and all carried the Haken malware. Check Point estimates the apps had been installed on over 50,000 Android devices before they were analyzed and removed from the Play store.

Microsoft Defender ATP preview arrives for Linux distros -- iOS and Android versions to follow
Microsoft has released a public preview of its Microsoft Defender Advanced Threat Protection (ATP) for various Linux distributions.
The company says that the tool will also be coming to iOS and Android later this year, and more details of these mobile editions are due to be revealed at next week's RSA Conference. The spread to additional platform comes after Microsoft rebranded Windows Defender as Microsoft Defender last year.

Popular document management apps expose sensitive files
Today's employees have access to a vast range of apps on their personal devices, but this can serve to undermine enterprise security because it's hard for IT teams to understand or control where sensitive corporate IP is going and how it's getting there.
The threat research team at Wandera has discovered a number of document management apps from Cometdocs that fail to use encryption when transferring files between the user and the backend service.

Hackers leak personal data of 10.6 million MGM Resorts guests
The personal details of 10.6 million people have been posted in a hacking forum after MGM Resorts hotels suffered a data breach. The data includes dates of birth, email addresses, names, phone numbers and physical addresses, and celebrities such as Justin Bieber and Twitter's Jack Dorsey are among those affected.
While the data has only just been leaked, it stems from a security breach that took place last year. Data dating back to 2017 was found accessible on an unsecured cloud server.