Microsoft's Exploit Mitigation Tool (EMET) gets a new bag of tricks
 Hackers are having a field day these days. No one is safe. But that doesn't mean that Microsoft or other companies aren't trying to design mitigation techniques to keep hackers out.
Hackers are having a field day these days. No one is safe. But that doesn't mean that Microsoft or other companies aren't trying to design mitigation techniques to keep hackers out.
In that vein, Microsoft released the enhanced Mitigation Experience Toolkit (EMET) which is designed to help prevent hackers from gaining access to your system. Yesterday, the company made available a preview version of EMET 3.5, introducing four new mitigation features construed at mitigating Return-Oriented Programming (ROP) attacks.
What is ROP?
ROP is an advanced exploitation technique that attackers use to combine short pieces of code that are already present in a system, for a malicious purpose. This security exploit technique uses control of the call stack to indirectly execute specially selected machine instructions immediately prior to the return instruction in subroutines within the existing program code. This is a process similar to the execution of a threaded code interpreter. In this way, the hack appears benign. Because all the instructions that are executed come from executable memory areas within the original program, this avoids the need for direct code injection. This process circumvents most measures that try to prevent the execution of instructions from user-controlled memory.
Many advanced exploits today rely on ROP to do their tricks. Security specialists have found the technique to be one of the most pressing attack vectors now facing Windows.
EMET is designed for enterprise IT workers and advanced users, but can be installed on all recent versions of Windows. It lets them manually switch on Windows anti-exploit defenses, such as DEP (data execution prevention) and ASLR (address space layout randomization) for specific applications.
ROP mitigations. The ROP mitigation techniques rely on the fact that at some point the ROP chain will need to call certain critical functions in a program. In other words, programs operate in a strategic way because the functions that they operate in demand that structure. And the issue is that this occurs before they transfer execution to the shell code. EMET will filter all operations to those critical functions and perform the following checks.
Caller checks mitigation. For starters, EMET will make sure that when a program reaches a critical function, it follows a “call” instruction rather than a “ret” instruction. This mitigation breaks many ROP gadgets.
Execution Flow Simulation Mitigation. Imagine a ROP operation that reaches a critical point or function. So when that happens, the ROP gadget is poised to start the exploit. This mitigation tries to detect ROP gadgets when a call to a critical function occurs. How does it work? By emulating a specified number of instructions at the return address of the caller of a critical function. Moreover, you can configure the number of instructions to emulate manually by editing the desired application’s registry key and creating the “SimExecFlowCount” DWORD value.
 Stack pivot mitigation. You can use this mitigation to detect the occurrence of pivot on the stack. Because it is compatible with most programs it is safe to enable it by default.
Stack pivot mitigation. You can use this mitigation to detect the occurrence of pivot on the stack. Because it is compatible with most programs it is safe to enable it by default.
Special function checks. The special function checks the mitigation and splits it into two parts, one to load library checks and the other to provide memory protection checks.
The load library validates calls to see if it comes from a ROP gadget or shell code, meanwhile the memory protection aims at preventing any attempts to change the protection of stack area for a given thread.
Mitigation Toolkit
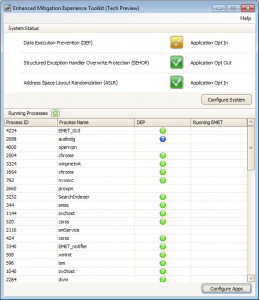
You can download the Mitigation Toolkit, and begin the installation. Once you have installed the program on your computer and started it for the first time, you can start configuring your applications and the three security features Data Execution Prevention, Structured Exception Handler Overwrite Protection and Address Space Layout Randomization. Some of the features that EMET provides are not available under XP.
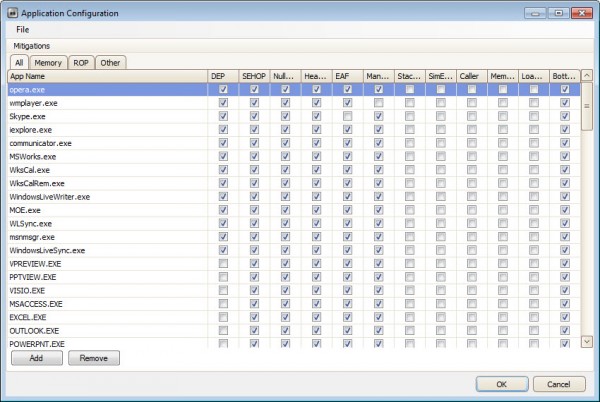
Probably the easiest way to get started is to click on Configre Apps, and then on File > Import to import one of the available protection schemes that EMET ships with. This ads all Office applications and core Windows programs such as Internet Explorer, Windows Media Player or Skype to the program protecting them from various exploitation techniques.
Some programs may not be compatible with all mitigation techniques, and it comes down to trial and error to find the configuration that works on a system.
Closing
Because Hackers are usually several steps ahead of security analysts, the mitigation programs can stifle their operations because programs have a certain constitution and programmers can learn and master the hacker techniques. That is what these programs are able to do.
Photo Credit: Andrea Danti/Shutterstock