Microsoft Endorses Product That Turns Off Vista UAC Nags
The latest version of a well-reviewed third-party security policy enhancement system for Windows Vista claims to solve what its manufacturer characterizes as "not a secure solution" to a critical problem Windows historically had with administrator privileges on programs. But in the announcement of the upgrade earlier this week, a key Microsoft product manager is quoted as having acknowledged Vista's own take on the solution was not quite enough, effectively reversing his company's stand on User Account Control.
The product is BeyondTrust Privilege Manager 3.5, and its key new feature is the ability to run Vista's UAC transparently without prompting the user for privilege elevation. In Monday's press release, Microsoft director of client security product management Austin Wilson is quoted as not only endorsing the product, but appearing to agree with BeyondTrust's key contention: that the UAC prompts were not only a nag but an insecure solution in itself.
"Microsoft recognizes that to help create a secure, auditable and compliant enterprise environment all users should be Standard Users and ideally not have administrative privileges or access to administrator passwords," the press release quotes Austin as saying. "BeyondTrust Privilege Manager helps corporations that need to allow standard users to run applications that require administrative privileges on Windows Vista with UAC enabled without any prompts or input required from the user."
It is the Vista feature which Apple so successfully parodied in one of its "I'm a PC" ads earlier this year: the part of User Account Control which asks the user to "Cancel" or "Continue," so that a task may run under elevated privileges. Alternately, Vista can be set up so that the user is asked to supply an administrator password - instead of just clicking on "Continue" - before any process is run that requires highest-level privileges.
Many users don't quite get it: Why would Vista keep asking permission over and over and over, even if it's just having the user click on a button?
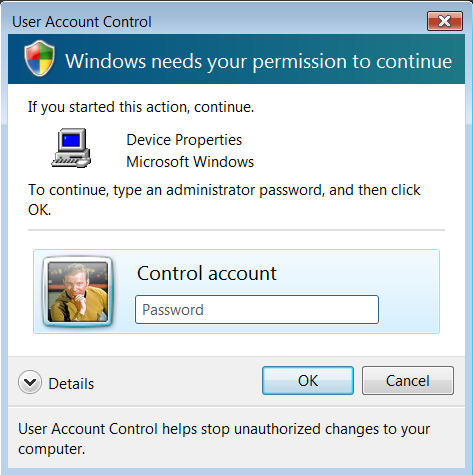
The reason is in order to implement an environment where user accounts have lower privileges by default. This way, they have less opportunity to be hijacked by an automated process, typically through the network, and made to perform system incursions in the background. Up until the era of Windows XP, users typically set up their accounts with full administrator privileges, because they trust themselves and don't want to withhold Windows functionality from themselves. That's okay until the point where such accounts are used without the user's direct knowledge or involvement.
In order to disable any keyloggers that may be lurking in the background, when Vista puts up a UAC prompt, it engages what Microsoft calls secure desktop mode. There, all other processes including many core operating system functions are suspended - which would suspend Trojans as well - while the user is prompted to click on "Continue" or to enter the admin password. Full disclosure: I myself endorsed this methodology in an article I wrote in November 2006 for InformIT, where I describe in full how UAC works and why I believe it's an effective security tool.
At the time the security prompt was first introduced in Vista betas last year, Microsoft began preparing the public for what it anticipated would be some serious concerns. A guide for Windows trainers in the workplace published last September by Microsoft tried to prepare them for the possible backlash: "Rapidly clicking through messages is a natural activity for most of us," it read.
"The UAC (User Account Control) feature of Windows Vista provides much tighter security than previous versions of Windows: It requires users to confirm some actions that are potential security risks, and does not allow some actions at all for standard users. Much research has gone into the phrasing of security messages so that they are easy to understand, and the shield icon helps information workers anticipate when authorization is needed. However, getting information workers to read each security message before they click is an ongoing challenge."
Since that time, surprisingly, some of Microsoft's own spokespeople have actually been visibly candid about their impressions of UAC, perhaps partly to help appear sympathetic to the customer, but also because they don't believe themselves that UAC and its "over-the-shoulder" (OTS) prompting method is the best solution to the account privileges problem.
Last June, Microsoft key security engineer Mark Russinovich wrote for TechNet magazine, "Even though elevation dialogs appear on a separate secure desktop, users have no way by default of verifying that they are viewing a legitimate dialog and not one presented by malware. That isn't an issue for [administrator account mode] because malware can't gain administrative rights with a faked Consent dialog, but malware could wait for a standard user's OTS elevation, intercept it, and use a Trojan horse dialog to capture administrator credentials. With those credentials they can gain access to the administrator's account and infect it. For this reason, OTS elevations are strongly discouraged in corporate environments."
So over the passing months, the concept has gone from nice idea (which I myself bought into) to "not the best solution" to something that admins may actually have to find a way to work around.
This leads us back to last week's press release from BeyondTrust, which paints a picture of the OTS prompting system as a security hole in itself: "Distributing administrator passwords to standard users is not a secure solution," BeyondTrust writes. "It places the security decision of which applications to elevate in the hands of the user instead of a network administrator. Additionally, these credentials can enable users to circumvent security policies, make ill-advised system changes, and run or install applications as an administrator."
So perhaps the clearest indicator to date of Microsoft's new willingness to bend to its customers' logic comes from its client security product manager, Austin Wilson. "I am pleased to see third-party security vendors such as BeyondTrust improve what is already our most secure business client OS, Windows Vista," Wilson continues in support of BeyondTrust's new upgrade. "The combination of elevating approved applications transparently with Privilege Manager and running UAC in no prompt mode with Internet Explorer in protected mode provides a best-of-breed solution to the least privilege problem."
BeyondTrust has not returned BetaNews' request for comment. Microsoft has also been asked to comment, and we could see a formal statement later today.
