Bad, but inevitable: The consumerization of IT is accelerating
Everyone, led by Vice President Whatshisname, wants to use their iPhone on the corporate network. Don't IT security people have enough problems? But the onslaught of unsecurable consumer devices in the enterprise is probably unstoppable.
A new study by IDC sponsored by Unisys looks at the problem of consumer devices invading the enterprise. The authors of the study come out of it upbeat, but it scares the bejeezus out of me. Put simply, these devices -- by which I basically mean those running iOS or Android -- were not designed to be secure and manageable. There are efforts to make them secure and manageable, but these are, generously-construed, version 1.0 efforts. It's obvious to me that these devices will create many severe security problems for enterprises, but the forces of consumerization cannot be stopped. Too many people want to use them, security be damned. Even the White House got them.
Resistance is Futile
The IDC study is based on "a worldwide survey of over 3,000 information workers and business executives in nine countries" and asks a lot of important questions. I have some quibbles with a few of the questions and disagree with some of IDC's conclusions, but there's great data in there. The chart below, the first in the report, illustrates the issue pretty well.
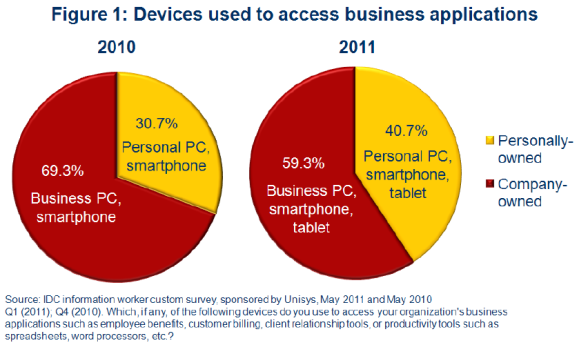
Business users are demanding to be able to use their own equipment to access corporate networks and perform business functions. This has been true for some time of home PCs, and even these are problematic in many ways, but now even more employees are demanding to use their smartphones and tablets.
IDC and others take the position that this is great opportunity for businesses to improve their processes, make employees more productive and responsive to customers. There's certainly a lot to that, but I'm a security guy and the thought of letting everyone bring their own hardware and software onto the enterprise network strikes me as, well, nuts.
Android and iOS both go to some effort to secure their environments. Apple seems to take it more seriously, although it may be that security is just a compatible outcome of their real aim, which is to control all aspects of the iOS experience. Still, there is plenty that can go wrong with iOS, as illustrated recently with a new jailbreak which enables drive-by attacks on iPhones.
Android is clearly the worse platform from a security standpoint. The permissions-based model asks too much of users at install time and there are numerous examples of malicious apps getting into the Android Market.
IDC told me that the necessity of supporting users of these devices will force IT to take another look at their security to make it better. And there are products which allow some management of iOS and Android devices, such as Good Technology and MobileIron. There are other techniques IT can use to strengthen security like certificate-based authentication and 2 factor.
Pardon My Skepticism
I'm not sold. I see far too many opportunities for abuse. When you consider the use of WebKit in Safari, the number of vulnerabilities patched regularly on the browser is large. With some effort and resources you can find them in advance. It's easy to envision targeted attack scenarios. And just as they enable new types of applications, these devices enable new forms of attack, like "iPhone Shoulder Surfing", in which an attacker takes video of another user on an iPhone and a keylogger of sorts is run against the video. See for yourself:
The survey shows that IT largely agrees with me. Eighty-three percent of IT respondents listed Security as a significant barrier to them accepting employee devices on their networks. Seventy percent consider employee-provided smartphones to be a security threat.
But IDC isn't buying it:
IDC believes this primary focus on security is likely a fig leaf that IT is hiding behind, and surmises the real issue is IT wanting to maintain control of the infrastructure. On many occasions, IDC has seen IT managers play the security card when they don't want to accommodate something new. The range of issues surrounding consumerization of IT is in fact very wide, but security is a bogeyman, both easy to point to and very difficult to argue against.
So, in other words, security concerns are obvious and difficult to refute, therefore they must be a distraction from the real issue.
I commend IDC and Unisys for asking (mostly) good questions and putting out good data, but they are the ones who are deflecting. Consumerization is inevitable, so perhaps they perceive resistance as futile.
Even Microsoft
Microsoft doesn't seem concerned either. Just yesterday at the WorldWide Partner Conference Microsoft COO Kevin Turner spoke of the Consumerization of IT (see about 01:16:20 into the video). He mentioned security once in passing, but didn't really talk about it. The four pillars to Microsoft's consumerization strategy are:
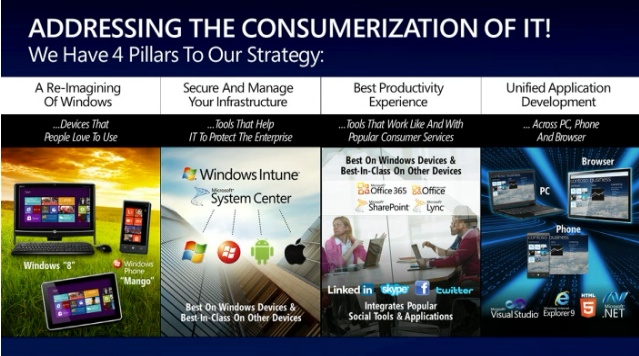
- Show what's possible with Windows. Education is paramount. The gateway to Windows 8 is Windows 7, and there will be full upward compatibility.
- How do enterprises embrace "bring your own device"? Windows Intune and System Center 2012 will allow management of devices beyond Windows PCs.
- Windows will have the best productivity experience.
- There will be a unified development environment which (he intimates) will allow development of applications which will run on Windows on any hardware.
Microsoft's ongoing efforts in security may serve them well as they move Windows onto new platforms, but they can't afford to slow down. They're too far behind already.
Don't IT people, especially the security people, have enough to do already? It's too bad, since this survey makes clear that things are going to get worse for them.
 Larry Seltzer is a freelance writer and consultant, dealing mostly with security matters. He has written recently for Infoworld, eWEEK, Dr. Dobb's Journal, and is a Contributing Editor at PC Magazine and author of their Security Watch blog. He has also written for Symantec Authentication (formerly VeriSign) and Lumension's Intelligent Whitelisting site.
Larry Seltzer is a freelance writer and consultant, dealing mostly with security matters. He has written recently for Infoworld, eWEEK, Dr. Dobb's Journal, and is a Contributing Editor at PC Magazine and author of their Security Watch blog. He has also written for Symantec Authentication (formerly VeriSign) and Lumension's Intelligent Whitelisting site.