Closing the time to protection gap with threat forecasting

The dominant theme at this year’s RSA Conference in San Francisco was actionable security intelligence, a term which can mean different things to different people. For example, do bad IP addresses, DNS fast fluxing information, and geolocation constitute security intelligence? Additionally, do malware campaigns and adversary tracking count as security intelligence?
The answer is yes for both questions, but it is important to note that these are not the only high-level indicators that can be considered security intelligence. The key challenge is understanding how to "apply" security intelligence in such a way that it is actionable. The following may be considered provocative and even go against the grain of opinion in Silicon Valley: In most approaches to security, there is too much emphasis on the adversary and not enough on understanding the attack surface.
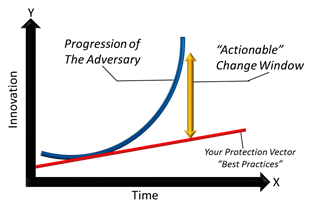
Pirc’s Law of Adversarial Disruption
The image above visually represents Pirc’s Law of Adversarial Disruption (is based on the Law of Disruption), which is my assertion that there is a rapidly expanding innovation gap between the adversary and traditional product-based security best practices. Further, this gap can only be disrupted by the application of new data-driven approaches that provide enterprises with actionable security intelligence and better visibility into their unique risk profiles. This is a key issue that security professionals face in our race to keep up with the adversary. Over time, cyber criminals have been able to re-invent themselves due to increased connectivity, social engineering, and the various applications that enable them to conduct campaigns and operations against a multitude of targets across every industry vertical. The security industry is preoccupied with the adversary and some believe that taking out a cyber criminal’s supply chain or trying to build a better version of "Anonymous" through white hat cyber vigilante groups will solve the problem. These tactics may help, but they won’t solve the problem. Attribution and traceability will eventually catch cyber criminals, but once their methods of attribution are uncovered, cyber criminals will move on to something more advanced. That amounts to a lot of work for little gain and also takes the focus off defending assets.
I’ve yet to attend a security conference where I haven’t heard the quote from Sun Tzu’s Art of War: "Know thy Enemy". After years of focusing on the threat landscape, there is still one thing we need to know better than the enemy… ourselves. You can’t properly defend your infrastructure if you are not intimately familiar with your attack surface, and few enterprises fully understand the full scope of the attack surfaces within their own organizations. Enterprises continue to buy and deploy tier 1 security products (antivirus, NGFW, IPS, SWG, SIEM, etc.) because these products are listed as security best practices. In order to defend against most of today’s threats, we first have to know what they are, and then we have to propagate that information across various security products. Some security vendors are quick to respond, while others are not so quick. This, however, is a shotgun approach to security that will likely solve only about 70 percent of an enterprise’s risk. Enterprises definitely need these technologies, but what about the other ~30 percent? This is where actionable intelligence can be used to offset the risk in the change window indicated in the image. We can never be 100 percent risk free, but by utilizing actionable security intelligence, we can begin to close the gap of time to protection and disrupt the adversary.
Threat Forecasting
We must take a sniper’s approach to identifying risk and closing the gaps. This requires a move from static risk analysis to variable risk analysis. How does variable risk analysis apply to threat forecasting? It removes the ambiguity and reduces the signal-to-noise ratio by tailoring security that is prescriptive to a specific environment. First, threat forecasting requires an in-depth understanding of your attack surface. The ability to clearly identify your attack surface is a fundamental of good security hygiene: again, how can you defend what you don’t know? Further, threat forecasting utilizes threat intelligence about known and unknown exploits and malware and maps it to your attack surface.
At this point, we have a lot of information, but it still only provides half the picture, and it’s difficult to discern what is actionable. To close the gap and understand which threats are a clear and present danger to your organization, you must be able to identify which of the possible threats targeting your attack surface are capable of bypassing the security products deployed in your network. Once you have this knowledge, you will have actionable and prescriptive intelligence that will not only reduce the time-to-protection gap, but will also greatly reduce risk.
This is a quick overview of the power of threat forecasting and the impact actionable security intelligence can have on your overall security efficacy.
Call to Action
As security professionals we need to challenge the status quo of security best practices. Additionally, we need to close the gap on time to protection by utilizing actionable security intelligence that matches our attack surface. Without any changes, we will continue to be like lemmings marching off a cliff.
Image Credit: watcharakun/Shutterstock
 NSS Labs' Chief Technology Officer, John Pirc is a noted security intelligence and cybercrime expert, an author and a renowned speaker, with more than 15 years of experience across all areas of security. The co-author of two books, "Blackhatonomics: An Inside Look at the Economics of Cybercrime" and "Cyber Crime and Espionage", Pirc has been named a security thought leader from the SANS Institute and speaks at top tier security conferences worldwide. Pirc’s extensive expertise in the security field includes roles in cybersecurity research and development for the Central Intelligence Agency, Chief Technology Officer at CSG LTD, Product Manager at Cisco, Product Line Executive for Security Products at IBM Internet Security Systems, Director of McAfee's Network Defense Business Unit and, most recently, Director of Security Intelligence at HP Enterprise Security Products, where he led the strategy for next generation security products.
NSS Labs' Chief Technology Officer, John Pirc is a noted security intelligence and cybercrime expert, an author and a renowned speaker, with more than 15 years of experience across all areas of security. The co-author of two books, "Blackhatonomics: An Inside Look at the Economics of Cybercrime" and "Cyber Crime and Espionage", Pirc has been named a security thought leader from the SANS Institute and speaks at top tier security conferences worldwide. Pirc’s extensive expertise in the security field includes roles in cybersecurity research and development for the Central Intelligence Agency, Chief Technology Officer at CSG LTD, Product Manager at Cisco, Product Line Executive for Security Products at IBM Internet Security Systems, Director of McAfee's Network Defense Business Unit and, most recently, Director of Security Intelligence at HP Enterprise Security Products, where he led the strategy for next generation security products.
