The Apple myth: Why security through obscurity isn't security
 My girlfriend was on the prowl for a new vehicle not too long ago, and decided on a Subaru. Not only do the company's vehicles arguably receive some of the highest safety ratings in the States, but their policy of across-the-board all wheel drive is another nicety I love about them. Even so, she wouldn't think of ditching her safety belt, no matter how safe the cars claim to be.
My girlfriend was on the prowl for a new vehicle not too long ago, and decided on a Subaru. Not only do the company's vehicles arguably receive some of the highest safety ratings in the States, but their policy of across-the-board all wheel drive is another nicety I love about them. Even so, she wouldn't think of ditching her safety belt, no matter how safe the cars claim to be.
Likewise, sizable portions of American society lives out in rural areas where crime and theft are almost unheard of. Yet they most likely still use locks on all of their doors, and keep them locked shut at night. Their risk of forced entry or other crimes are leagues lower than in congested urban areas (like my neck of the woods, Chicago) but they still follow plain commonsense.
So this begs the question: how has Apple gotten a free pass on the falsehood that its OS X (and now iOS) users just don't need anti-malware software? As an IT professional who has personally cleaned off numerous Macs each year for the past 2-3 years, it really irks me that Apple still hasn't admitted that this falsehood is endangering an entire slice of our computing society.
Even though we don't push this mantra at our company, knowing full well it's a borked belief, you won't find the same honesty from any Apple Store employees. Salespeople at Best Buy and other retailers that I've encountered suffer from the same misleading tunnel vision. Apple's done a great job coercing the last decade of Mac buyers that malware just doesn't exist on Macs. Yet the evidence continually points in the opposite direction.
To prove my point, try doing a search for "antimalware" or "antivirus" on the Apple support website. The single official article you will find referencing either of these terms is a posting ironically titled "Mavericks Server Admin: Security best practices". In it lies the sole inking on Apple's help website as to the need for antivirus software.
But there's a gotcha: this article was meant for admins of the server edition of OS X -- not for average end users.
Per Apple, users running Mavericks server should:
Install antivirus tools, use them regularly, and update virus definition files and software regularly. Although viruses are less prevalent on the Mac platform than on Windows, they still pose a risk.
I thought the last batch of OS X server admins dried up when Apple ditched the enterprise formally and killed off Xserve. I was mistaken -- they still exist it seems. As do malware strains on the Mac, they halfheartedly admit.
Apple's Ailing Pitch: Security Through Obscurity Works
The fruit company spent the better part of the first decade of this century basking in its own nirvana while Windows XP was the leading posterchild of the Windows malware epidemic. While Microsoft was kicking into gear the vision that Bill Gates set forth in getting serious about Windows security, Apple was lobbing cannonballs at Windows users with its "I'm a Mac" television ad series.
One such ad put this security debate front and center, in plain user speak. This 2006 ad poked fun at the Windows virus scene via an exchange between the Windows and Mac user where the Windows guy was suffering from an ailment, and mentioned how many malware strains hit the platform in the last year. The Mac guy states bluntly in response: "Not Macs".
Apple's official flag of security through obscurity was formally planted. As such, Apple users have been miffed into believing that this is actually a safe practice to ascribe to. But this is Apple we are talking about. What they say must be true.
While the rest of the 2000s flew by with Apple picking up considerable batches of Windows converts, by 2010 the tide was starting to shift. Well known voices in the tech industry were starting to speak against the tide, like Alex Stamos and Mac security specialist Charlie Miller.
They asserted claims that took different means to an end, but concluded on relatively the same thing: Windows (Vista, 7) was finally a more secure platform than OS X. While Microsoft spent the better part of the last decade getting extremely serious about security in Windows, Apple considered security as an almost afterthought. A dirty word inside Cupertino, some could say.
David Harley penned an interesting piece on the official ESET blog which let loose something most industry pundits already figured: that Apple has only recently started realizing it must get serious about its relationship with the anti-malware software security industry.
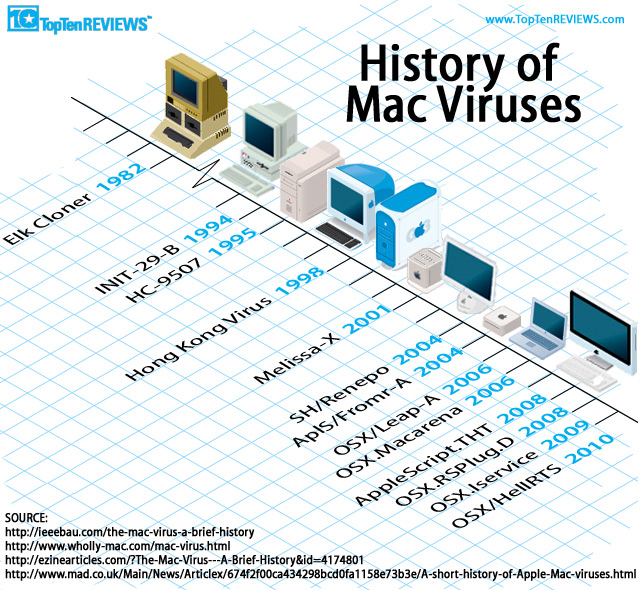
While the infection risk on Macs isn't nearly as prevalent as on Windows machines, the falsehood that Macs have always been malware free is anything but true. This graphic outlines just a sampling of some viruses that have hit Apple's 'untouchable' systems. (Image Source: TopTenReviews)
This is in complete contrast to Microsoft, which has been on the forefront of working with AV makers to ensure their products can work to secure Windows users in the best manner. Microsoft even publicly admitted recently that its own first-party Security Essentials product shouldn't be considered a viable long term solution for users as it only provides a bottom baseline of security. This doesn't say much about Security Essentials, but at least provides a frank honesty for Microsoft's user base.
In short, Microsoft isn't hiding behind any security veils. Its transparency on security topics affecting its products should be lauded. Aside from numerous first party blogs dedicated to such topics (here is one example, and another for kicks) they even host a public Security Response Center detailing bulletins on security patches, threats, and other items affecting its products. Its ecosystem of sub-blogs and TechNet articles trickle into a further myriad of information overflow.
In contrast, Apple hosts a single simple site dedicated to security for its products, primarily just listing out links to patches, general product info, press contacts, and a few bulleted best practices on security in Apple devices. Compared to the deluge of information Microsoft publishes, this is rather pittance in comparison.
Apple's real message from its pathetic security information resources? Security isn't a real big problem for us. If only the media wasn't so accepting of this, perhaps Apple would change its tune.
Aside from Apple's recent covert courting of anti-malware companies with products for the Mac, Apple has not been shy in pushing an idealistic mantra of security through obscurity for its OS X faithful.
There's a problem with this thinking, however, that is negating its applicability: Mac users aren't so obscure anymore. As of March 2014, OS X users represent a full near 8 percent of the computing population. If you're hinging your security beliefs on belonging to the crowd of "little guys" you'd better hope that too many people don't make the jump from Windows for the same comfort.
The whole concept of security through obscurity isn't much of a proven concept as a core security best practice. In combination with other security tenets, it may hold some weight, but not in an Apple-like way that has been passed as religion to OS X users for the last decade.
In fact, the United States National Institute of Standards and Technology (NIST), the same body that provides reference standards for much of government, academia, military, and other entities, calls out this concept outright in its "Guide to General Server Security." In short, "System security should not depend on the secrecy of the implementation or its components".
The mighty NIST isn't the only one calling this theory out for what it's worth. Tony Bradley of PCWorld wrote on this topic back in 2012, pointing out rightfully that "Security is more a result of user awareness and behavior. Risky behavior is risky behavior regardless of the operating system".
Other such online articles point at the same holes in this mentality. Rebecca Herold penned one such piece, as did Christine Barry from Barracuda Networks.
Apple's insistence on comfort from security through obscurity perpetuates risky behavior by OS X users which is arguably leading malware writers to find them as a rather juicy target -- and one that is only getting juicier. A mass of users nearing 10 percent of the computer population that most likely has zero security software running? And not to mention, generally having a higher disposable income? That's a winning combination for the criminals that run modern botnets and malware rings.
Eugene Kaspersky, CEO and founder of well-known security firm Kaspersky, said back in 2012 that Apple is roughly 10 years behind Microsoft in terms of security. His assertion is based in the understanding that Apple's market share of OS X has been growing rapidly, and the walled garden approach to security just isn't cutting it anymore.
Kaspersky joked, “Welcome to Microsoft's world, Mac. It's full of malware".
OS X and Linux/Unix: Security Breaches at the Gates
Matt Baxter-Reynolds of ZDNet recently penned an interesting piece outlining just how sloppy the situation surrounding Apple's latest SSL mess was. After breaking down the code behind the bug, Matt outlines the whys of how this should have never came out of Cupertino.
More importantly, he alludes to the double standard that exists in how Apple gets a relative pass from the security press industry, but if (just if) this happened to Microsoft, there would have been a downright outpouring of media scrutiny.
Regardless of the soft press Apple gets on its security mishaps, one thing that this SSL bungling does show is that Apple's internal code auditing and security practices just aren't up to the levels they should be. Matt said it point blank: "The fact that this code made it into production at all is a shocking indictment of Apple's engineering team".
Surely, the SSL mess has nothing to do with malware infections and the average uninformed user could write this off as a simple one-off blunder. But just peruse some of OS X's recent history with malware, and you may recant that judgment.
Sophos recently reported on a new malware strain that infects OS X users via an "undelivered courier item attack" and even formally recommends in its official 2014 Security Threat Report that Mac users install and use antivirus software. The same 2014 report outlines other numerous Mac malware outbreaks that hit the scene in 2013 alone.
Two months ago, in early February, news of a new Bitcoin stealing OS X malware strain came out that aims to do just that: take Bitcoins behind your back.
And what was regarded as one of the largest Mac malware infections in Apple history, Flashback, which took over 650,000+ systems in 2012, seems to be back on the scene affecting a portion of OS X users -- likely unknowingly.

Apple spent the better part of four years convincing people that Windows machines were so passé in more ways than one. A big selling point they pushed, and still do, is that Macs just don't get viruses like PCs. This wive's tale is increasingly untrue, and will in my opinion lead to a downright epidemic of Mac malware , much like what hit Windows XP back in the early to mid 2000s. (Image Source: MaxPictures.com)
But Apple isn't the only one who's feeling the pinch of indiscriminate malware these days. Unix, once thought to be nearly bulletproof in IT circles, had its clean image wiped away in March when ESET researchers outlined Operation Windigo which involved a command-and-control malware operation affecting over 25,000 Unix servers worldwide.
This trojan scheme was meant to target end users that visited websites being hosted by these Unix systems, and ultimately steal data for criminal profiteering.
Another operating system with Linux roots, Android, is experiencing an explosive growth of malware to the tune of nearly 600 percent according to Sophos. More than 650,000 malware strains have been identified by Sophos to date (as of Feb 2014). While a large majority of the malware is flooding in through third party app installations, the malware is doing the usual rounds of mischief: data theft, command and control, etc.
Is betting all of your cards on obscurity alone such a good prescription? You can make your own conclusions.
Apple Should Get Honest: Mac Users Need Security Software, Too
Eugene Kaspersky's frank words on Apple's public stance on OS X malware should stand as a warning to Cupertino that the happy days for OS X are coming to an end. In fact, I'd argue that those days are already over. With nearly 8 percent of the computing population using Macs, this crowd is no longer the niche that could sit and laugh at their Windows counterparts.
Apple used to be nothing more than a trendy alternative for users, and now, the belief that turned portions of Windows users is coming back to bite them square in the foot. How long will Apple keep holding up the smoke and mirrors regarding Mac security, both in OS X development and in end-user recommendations?
Consider this food for thought. Just 3-4 years ago, the number of anti-malware options for the Mac were counted on one hand.
Today, Wikipedia shows that no less than 21 options exist for securing your Mac. Quite a jump, I'd say.
Does Apple know something that the anti-malware companies don't? Or, more likely, is it that Apple is just continuing to play naive to the realities that the rest of the security industry understands? If there wasn't a market for OS X security software, trust me, these security behemoths wouldn't be investing troves of development time and money in such products.
But as their research (which I described above) continues to show, Apple's marketing department continues to filter out the realities of industry trends. One of Apple's biggest selling points for OS X is crumbling at the hands of thirsty malware criminals, and Cupertino doesn't yet have an interest in ditching its marketing taglines for the sake of being honest with its users. For that alone, I seriously doubt the long term future of OS X as a safe operating system next to Windows and Linux.
As a consultant, I'm doing the best I can to educate my customers. But I can only fight an uphill battle with so much ammunition. The media gives Apple a regrettable pass on its security situation, and in turn, allows it to likewise perpetuate the debunked notion of security through obscurity.
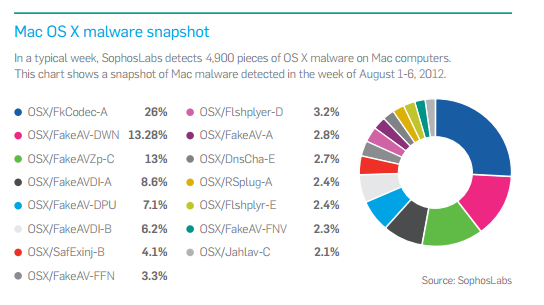
Sophos stated that it detects about 4,900 pieces of malware each week on Macs systems its software protects. This figure was from 2012. We can only imagine how much higher this is today, and more importantly, how much undetected malware is sitting on unprotected Macs at this moment. (Image Source: Sophos Security Threat Report 2013)
To the average user I encounter, the sad mistaken belief still holds that Microsoft doesn't know security, but Apple does. Because, as they tell me, their friend has a Mac, whose other friend also has a Mac, and all of them never get viruses. When I ask if they know this because they run proper anti-malware software, they call the idea ludicrous. I guess there's a certain comfort for Apple users who would rather blindly believe in the bunked status quo.
It's only a matter of time until a massive malware epidemic hits the Mac. One that will literally have Apple shipping its users coupons for complimentary copies of anti-malware software. The recipe for disaster is written on the walls. A near 10 percent slice of the computing population which has zero education in running security software. Users that have arguably higher disposable incomes (on average) than their Windows counterparts.
If you were a criminal, wouldn't you call this crowd a rather soft and desirable target? Just like house thieves that will outright pass up homes that advertise their usage of alarm systems, these crooks see Mac users in a similar vulnerable light.
Wake up, Apple. When, not if, a malware epidemic breaks out for OS X, don't be surprised when legions of faithful users migrate back to Windows.
Everything comes full circle, eventually.
Image Credit: ConstantinosZ/Shutterstock
 Derrick Wlodarz is an IT Specialist who owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over eight+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud-hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net
Derrick Wlodarz is an IT Specialist who owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over eight+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud-hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net