Ransomware: How to identify the threat and protect yourself against it

Ransomware has affected over 13.1 million US citizens. That’s 4 percent of the entire US population. Half of those people will pay a steep ransom of up to $500 to retrieve their information.
Do not let this be you. Arm yourself against the epidemic and read on to find out how keep yourself from being a part of the statistic.
The Nitty-Gritty Behind the Nightmare
Ransomware is extremely common, but how does complicated malware like this actually work? To break down the inner workings of ransomware, we will take a closer look at the .locky strain.
Let’s pretend it’s a regular day in the office, and you need to sort through your hundreds of emails. What if you came across an email that looked like this?
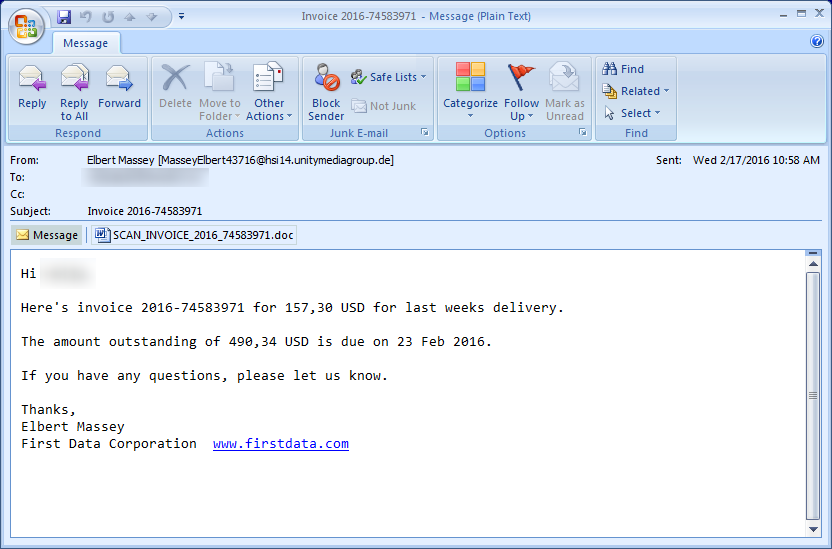
Source: https://securelist.com/blog/research/74398/locky-the-encryptor-taking-the-world-by-storm
A Nigerian prince isn’t asking for your credit card information, so at first glance this message appears innocent enough. You decide to open the document.
Next, a Word document may pop up asking you to enable macros in order to read the invoice. Also, you may see an option to manually open files in a .zip file. Immediately following your completion of these seemingly harmless tasks, the following message comes up:
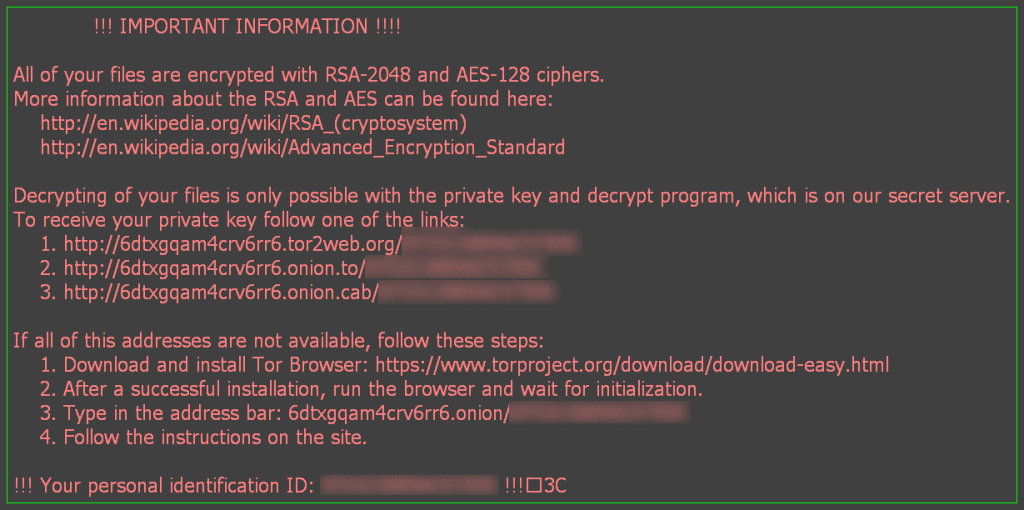
Source: https://securelist.com/blog/research/74398/locky-the-encryptor-taking-the-world-by-storm/
This message means your device has been affected by crypto-ransomware. The hackers demand bitcoins for your files.
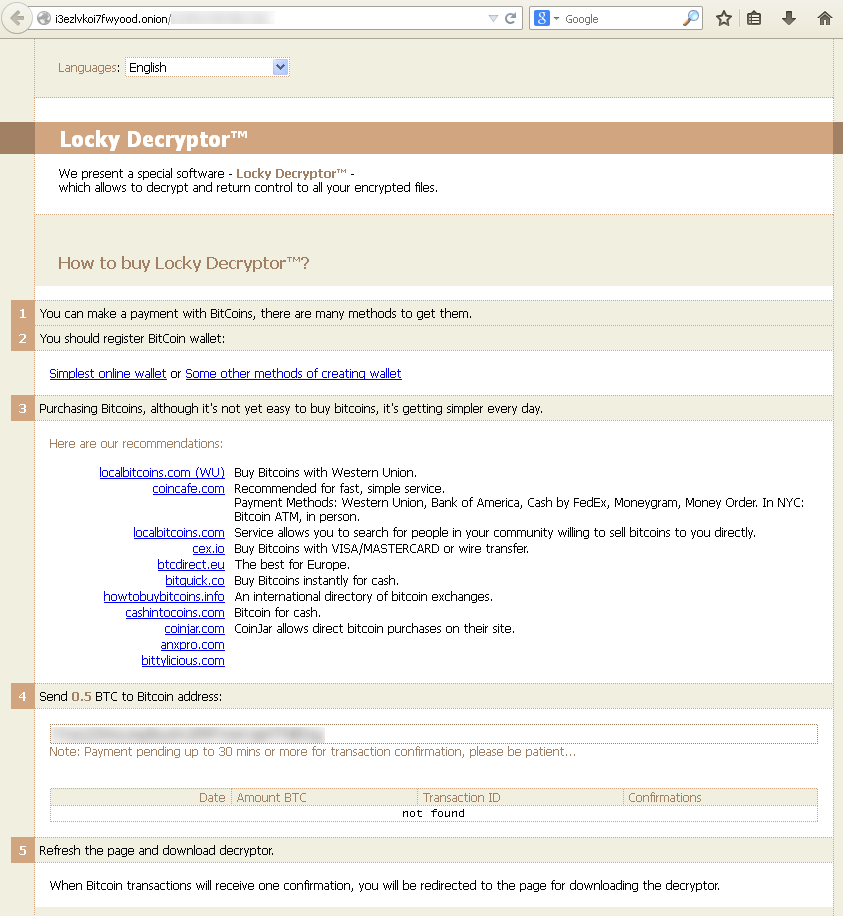
Source: https://securelist.com/blog/research/74398/locky-the-encryptor-taking-the-world-by-storm/
Am I Supposed To Know What a Bitcoin Is?
Hackers rely on the use of a newcomer in the cyber world: bitcoins.
Bitcoins are not printed in banks. Bitcoins are "mined" through computers and particularly valuable because only 21 million can be mined ever. Bitcoins are a hacker’s bread and butter because they are decentralized and untraceable. International transfers are anonymous, meaning law enforcement cannot trace them back to a sole source.
Bitcoins are also becoming more expensive. In February, Hollywood hospital paid a 40-bitcoin ransom valued at $17,000, or $425 per bitcoin. This June, the price per one bitcoin increased to $583, which means Hollywood hospital’s ransom is now valued at a whopping $23,320.
I’ve Been Infected: Now What?
- Pay the piper.
The FBI suggests just paying the ransom. Although this tactic is often taken by large hospitals and organizations, I view this option as a last resort. Paying the ransom means giving into the hacker’s demands and sometimes, it won’t work at all.
For example, Kansas Heart Hospital fell victim to a failed decryption just this past May. The hospital was attacked by ransomware, and the hackers asked for a small ransom in exchange for the hospital’s files.
After paying the ransom, the files weren’t decrypted, and the hackers demanded a second, larger payment. Ultimately, the hospital did not pay the ransom realizing that this was not the best course of action.
- Act Quickly, Think Strategically
Your second option could be to follow these simple steps:
- Disconnect from your network, Wi-Fi and Bluetooth, and remove any portable devices
- Asses the damage
- Identify the ransomware strain
- Determine the best response -- Should you pay? Cut your losses? Is there a decryptor available?
A Hacker’s Plan of Action
Hackers will threaten to do one of three things: encrypt, lock or worst of all, delete. In the case of deletion, there is a glimmer of hope. Some lazy hackers may simply prevent your files from appearing in your folders, while others may leave traces behind on the disk, making partial recovery possible.
Lockerware viruses will appear as a Law Enforcement warning. An example of this is the FBI Moneypak virus. The files are left in the same place, Trojan horses or scripts are used to block Internet access, and an unknown login is created. Basic strains of this virus can be removed through free versions of Malwarebytes and Hitman Pro.
Tips to Protect Against Ransomware
- Education
Host lunch-and-learns with your organization’s Human Resources and IT departments to train them on the basics of spotting malware.
- Protection
In order to defend against a ransomware attack, back up data often following the 3-2-1 rule: create 3 backup copies on 2 different media with 1 backup in a different location. Make sure to verify the backups, or else they are useless.
- Monitor
Consistent monitoring can be a good way to spot virus attacks. Some ransomware strains will actually change the names of your files, and add an extension (for example: .locky). Find a data storage solution that can also track user activity. Strange activity could be an indicator of ransomware or data breach.
What’s Next for Ransomware?
The future of ransomware lies in iTunes and QuickTime for Windows, according to Ian Trump, Security Lead at LOGICnow. Adobe Flash is the most vulnerable software right now, leading Google to remove the need for Flash in most content.
Although Ransomware is common, these attacks can be reduced as long as people continue to spread ransomware awareness and educate the public about this epidemic.
Image Credit: pathdoc / Shutterstock
 John Hurley is CEO of SmartFile. He has over 18 years of Internet software and leadership experience. Prior to starting SmartFile, John was president and co-founder of Webexcellence, one of the largest web development firms in Indianapolis. John worked with companies such as Delco Remy, Angie’s List and NCAA to develop rich web applications. Also while working at Webexcellence, John played a key role in the startup phase of ExactTarget. As president and co-founder of SmartFile, John heads the sales, marketing, and business development.
John Hurley is CEO of SmartFile. He has over 18 years of Internet software and leadership experience. Prior to starting SmartFile, John was president and co-founder of Webexcellence, one of the largest web development firms in Indianapolis. John worked with companies such as Delco Remy, Angie’s List and NCAA to develop rich web applications. Also while working at Webexcellence, John played a key role in the startup phase of ExactTarget. As president and co-founder of SmartFile, John heads the sales, marketing, and business development.