Containers: The ultimate Trojan horse

Containers are meant to be immutable.Once the image is made, it is what it is, and all container instances spawned from it will be identical. The container is defined as code, so its contents, intents and dependencies are explicit. Because of this, if used carefully, containers can help reduce supply chain risks.
However, these benefits have not gone unnoticed by attackers. A number of threat actors have started to leverage containers to deploy malicious payloads and even scale up their own operations. For the Sysdig 2022 Cloud-Native Threat Report, the Sysdig Threat Research Team (Sysdig TRT) investigated what is really lurking in publicly available containers.
Public registries: A double-edged sword
Docker Hub is the most popular free public-facing container registry. It houses millions of pre-made container images in convenient, self-contained packages with all required software installed and configured. Public registries also host official content and images signed by Verified Publishers, which adds some level of trust that they are not malicious and can be used safely. While public registries save developers time, if a user is not careful, there could be malicious aspects to the container they pull. With so many containers to choose from, it is easy to choose the wrong one.
Threat actors also appreciate how much friction this technology removes from developer workflows. They count on the fact that many developers may not examine what exactly is being installed. According to the Sysdig threat report, DockerHub is being used by malicious actors to deliver malware, backdoors, and other unwelcome surprises to users and companies. One specific practice to watch out for is typosquatting, which is when an image is disguised as legitimate while hiding something nefarious within its layers. Its name can be just a letter off the real thing, or the attacker might rely on a developer carelessly copying some instructions containing the bad path.
Sysdig TRT found images shared by suspicious users with names to appear as popular open source software in order to trick users. For example, popular packages like Drupal and Joomla have had their names used in order to disguise malicious payloads. Deploying these images means opening the doors of our environment to attackers, letting them pursue their goals or move internally to business critical assets.
What's really in the container
The Sysdig TRT analyzed more than 250,000 Linux images over several months. During the research, 1,777 images were found to contain various kinds of malicious IPs or domains and embedded credentials.
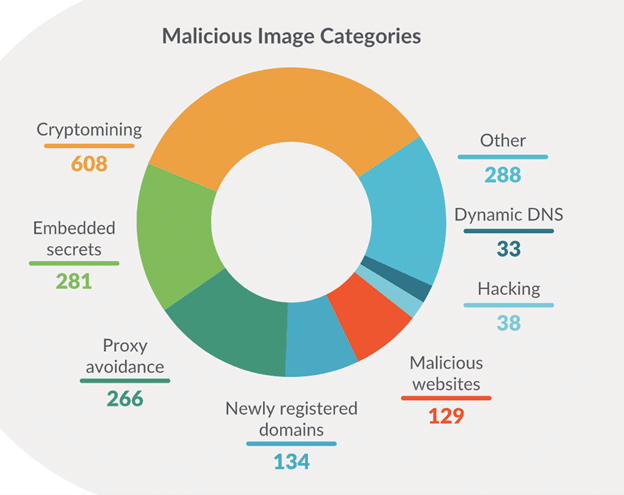
Upon taking a closer look, we see that cryptomining images are the most common malicious image type. This is quite expected because mining cryptocurrency on someone else’s compute resources is the most prevalent type of attack targeting cloud and container environments today.
Embedded secrets in Docker images is the second most prevalent attack technique. In this case, attackers insert secrets in an image and use this information to get a foothold in your environment and then try to move laterally. For example, an SSH key can be added, which could allow for simple remote access or AWS keys could be added to give them cloud capabilities. This highlights the persistent challenges of secrets management is still a battle we need to win.
Conclusion
Container images are just another software asset which requires proper security controls. Externally sourced container should be thoroughly scrutinized before they are used by your organization, whether in production or on developer machines. Tools that scan container images before loading can help as they will examine the layers and look for vulnerabilities and malware.
Static analysis alone isn’t enough. Dynamic analysis is the only real way to know what happens once that container is running. This is where threat detection and response tools play their part in protecting cloud workloads. Tools like Falco, a CNCF open source project, will watch how the container behaves and alert or automatically respond with various actions if that behavior is suspicious.
Containers are here to stay in the supply chain. In fact, their adoption continues to increase. Organizations must understand the risks that premade images can introduce. Cryptominers can get very expensive very fast, and backdoors can lead to a compromise of your entire infrastructure. Everyone loves containers. Attackers love containers too.
Image Credit: Sadik Gulec / Shutterstock
Stefano Chierici is Threat Research Lead Manager at Sysdig.
