No more either/or: How a layered, data-centric approach to security removes outdated restrictions

Viewing security as a modern data challenge is something different from simply recognizing the crucial role of data. IT security has always been about gathering, analyzing and acting on data. But modern cloud data challenges are about handling ever increasing amounts of disparate, differently-structured and unstructured data, from a changing mix of dynamic sources.
The challenge is not about battling to handle data overload. But rather, rethinking the underlying data technologies you use at the core of your security platform, so that as more data floods in, it makes your security tighter and more effective.
Many of the toughest choices around different IT security approaches are false dichotomies. Customers are forced to pick an either/or approach because of the limitations of vendors’ legacy architecture. These architectures are locked to a specific data model: a limited, static World view. And, all too often, this is a model that does not scale.
By leveraging more advanced, powerful, and less rigid data technologies, many of these "either/or" dilemmas disappear, offering users the obvious, and most sensible option to leverage both.
Agent v’s Agentless -- A Worn-Out Debate
The "agent versus agentless" debate, is a prime example of this type of false dichotomy. With a powerful modern security platform, organizations should be able to use a logical mix of both.
For organizations in an early stage of cloud maturity, and those that don’t have the time or resources to deploy security agents across a broad infrastructure, an agentless method offers a fast and easy start, getting visibility into cloud assets, possible risks, and attack surfaces. With a dedicated cloud security platform, all this should require is a simple one-time connection of your cloud accounts.
The agentless approach is also helpful for gaining full coverage where a traditional agent cannot reach, or quickly assessing security posture across an entire environment. For example, shadow IT hosts and new accounts that companies may have brought onboard due to mergers and acquisitions.
Agentless offers the lowest possible overhead for organizations to gather data about vulnerabilities, misconfigurations, cloud audit log anomalies, and unusual account activities. It arms those organizations with the essential data to meet compliance guidelines, detect account compromises, and much more.
Easily implemented, an agentless approach can identify risks stemming from vulnerabilities and misconfigurations in your cloud environments during build time. It can then scan and detect vulnerability risks across all your hosts, containers, and language libraries. Security teams can detect anomalous activities, such as a new user trying to create or delete an EC2 or S3 instance, change keys or policies on a cloud account, or add new privileged users.
An agentless approach is quick and simple. However, it can only go so far. To gain the best picture of your cloud environment, it’s critical to monitor workloads during runtime. This is essential for uncovering active threats, such as an attack that is exploiting an unknown or zero-day vulnerability.
Relying solely on agentless scanning leaves the potential for organizations to miss critical activity and information. For the strongest runtime security, you need an agent that is tracking activity to investigate and respond faster. Unlike an agentless approach, an agent is uniquely positioned to perform activities such as runtime threat detection of known and unknown threats, file integrity monitoring, host-based intrusion detection, configuration checks, and host vulnerability scans.
The Layered Security Approach
The latest Lacework Cloud Threat Report, reveals how attackers are rapidly increasing in sophistication, with a particular focus on infrastructure. Attackers constantly seek paths of least resistance to compromise a system, hiding in the complexity of seemingly disparate risks and exploiting them whenever possible. Despite cloud adoption becoming nearly ubiquitous across industries, many enterprises still lack the visibility needed to truly manage and understand these sophisticated vulnerabilities present or emerging in their own cloud environments.
To identify threats and vulnerabilities, organizations need to gather and correlate as much information as possible from all available sources. The best possible option is to adopt a layered methodology to security monitoring that allows companies to leverage the relative advantages of both agent and agentless approaches. But this is where the data handling capabilities of the overarching security platform come heavily into play.
If a security platform has originally been built to handle structured data or time series data from its own proprietary agents, it will struggle to handle unstructured logs files, or other data from external tools and integrations. Conversely, a platform specifically built around one cloud API, may struggle with others and is likely to lack the underlying data model and real time data handling capabilities to incorporate more sophisticated agents. Any attempt to update the original platform is likely to result in sub-standard, bolt-on or "gaffer tape" functionality and performance.
For any real solution, it is essential that a cloud security platform is built from the ground up to handle and analyze diverse data types from different sources. This is viewing security as a data challenge.
Machine Learning -- Rewriting the Rules
But the ability to handle diverse data types within a core, cloud security platform is only the first part of any real solution. Users may have the ability to draw in more data from more diverse sources. However, wrangling these high volumes of diverse, complex data manually within an outdated platform is unsustainable, if not impossible. Any system that relies on security administrators maintaining written rules, rapidly becomes overwhelmed resulting in data overload and alert fatigue from false positive alerts.
Effective use of machine learning models changes the rules of the game, by removing the need for security rules. A good security platform should still enable rules for regulatory and compliance purposes, or to enforce bespoke platform configuration for example. However, a layered security approach is about complex cross-correlation of diverse data types. Relying on manual rules is not a realistic option.
Instead, machine learning can be trained to create organization-specific models of "normal" behavior. This can include the behavior of users, administrators, workloads, host, platforms: in short every human and non-human element of the system. With the model in place, the security system generates security alerts when any behavior differs from the norm. This results in great alerting accuracy, fewer false positives and more comprehensive security coverage. Moreover, machine learning makes it possible to identify new attack vectors as they emerge, zero-day exploits and complex multi-tier vulnerabilities.
Strong machine learning models will effortlessly cross-correlate endless permutations of diverse data elements, such as time series metrics, logs, configuration settings and much more. The scope and accuracy of what a machine learning model can achieve in days, would be impossible for even the most skilled team of security analysts. And in stark contrast to a manual security team, the more data a model has to contend with, the more accurate and effective it becomes.
The Human Requirement
Security analysts are not yet out of a job. Machine learning enables them to do their job effectively once again. However, security alerts still require human investigation, triage and response. This is where the final piece of the puzzle comes into play for any layered security approach.
We have seen that more sophisticated security alerts are now required, correlating a broader, more diverse mix of information from agents and security APIs across all layers of a system. This means that investigating, verifying and acting on these alerts becomes an increasingly complex task. Without the right user experience from a security platform, analysts are left endlessly screen hopping, logging in and out of the root data sources, to reverse engineer the increasing wizardry of both the attacker and the alert.
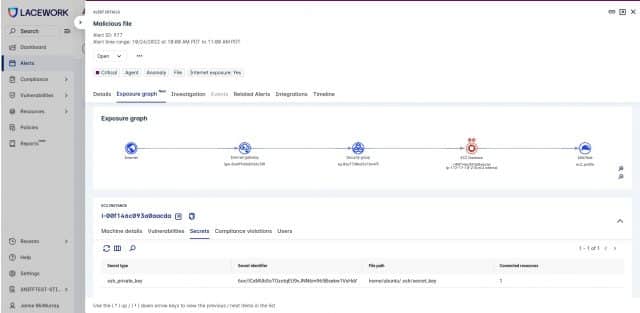
This is where attack path analysis comes into play. Effective attack path analysis is about more than a user interface which shows the direct sources of an alert (and not all security platforms do this effectively). Attack path analysis needs to direct a security analyst as quickly as possible towards a diagnosis, not just the symptoms.
Graph analysis is built to uncover hidden relationships between diverse data elements. Incorporating this into the user experience for attack path analysis gives analysts a full picture of any attack. Alerts are triggered by anomalies coming from a specific data source, or an anomalous correlation between multiple metrics. Graph analysis can then be used to find data from any sources that are related to the trigger.
From here analysts can be presented with a single screen that visually ties together different attack vectors, including vulnerabilities, misconfigurations, network reachability, secrets, and identity and access management (IAM) roles for every host in the environment. This provides an additional layer of context for every alert to clearly show which assets could be attacked and why.
As cloud threats continue to grow in volume and sophistication, this critical context enables security teams to identify and prioritize remediation based on risk and actively watch for exploits before they become a problem.
Image Credit: donscarpo / depositphotos.com

Ryan Sheldrake is Field CTO -- EMEA, Lacework