Old habits, new threats -- Why more phishing attacks are bypassing outdated perimeter detection

Perimeter solutions such as Secure Email Gateways (SEGs) have long been a cornerstone of email security, historically serving as the primary line of defence against malicious emails entering an organization. Utilizing legacy technology such as signature and reputation-based detection, SEGs have provided pre-delivery intervention by quarantining malicious attacks before they reach the end recipient.
Why, then, are 91 percent of cybersecurity leaders frustrated with their SEGs, and 87 percent considering a replacement?
Among many other concerns, such as their overlap in functionality with Microsoft 365 and the administrative burden of complex and manual rules, one of the key reasons for this major shift in attitude comes down to efficacy. As the threat landscape continues to evolve, cybercriminals are finding ways to bypass SEG detection technology. Additionally, the major burden of maintaining legacy technology slows SEG vendors' ability to innovate their solutions in a cutting-edge way. This is why, in the first three months of 2024, we identified a 52.2 percent increase in the number of attacks that bypassed SEG detection.
Signature-based detection
One key detection mechanism used by SEG technology is signature-based detection, which can be effective against 'known bad', such as malicious payloads, sending domains and hyperlinks that have previously been identified and are present in definition libraries.
Whilst this can be efficient in filtering out frequent attacks and spam mail, the fact the threat must be ‘known’ can dramatically reduce its efficacy when detecting zero-day attacks, socially engineered phishing emails without a traditional payload, and any hyperlink or domain that is polymorphic in nature. This is especially concerning since the rise of AI and publicly available chatbots have allowed cybercriminals to churn out new payloads at an alarming scale – each not recognized by any blocklist.
Obfuscation
There are a few phishing techniques and payloads that can easily bypass signature-based detection. Firstly, obfuscation is a key tactic used by cybercriminals to mask malicious payloads and evade signature-based detection technology. In the first three months of 2024, 24.9 percent of attacks employing technical measures to bypass detection hijacked a legitimate hyperlink. This form of obfuscation involves hosting a malicious payload on a legitimate site or using a legitimate website link to obscure the ultimate destination. Additionally, 19.6 percent of attacks concealed hyperlinks to phishing websites within image-based attachments, and 16.2 percent used HTML smuggling, where an encoded malicious script is 'smuggled' within an HTML attachment.
Social Engineering
Key to signature detection is the presence of some form of ‘known bad,’ so what happens when the attack doesn’t include any form of physical payload?
Cybercriminals are increasingly using open-source intelligence (OSINT) to craft convincing phishing emails that impersonate trusted stakeholders in a business or supply chain. These attacks rely on social engineering techniques to trick the recipient into performing actions such as divulging personal information or changing financial details, without requiring them to click on a traditional phishing hyperlink.
Therefore, without any physical payload, purely linguistic and socially engineered attacks are highly likely to bypass signature detection. This is especially true if the attack is sent from a domain that isn’t listed on any blocklist, such as a legitimate but compromised account or a spoofed email domain with proper authentication.
Polymorphic attacks
In 2024, our Threat Intelligence team have seen campaigns where cybercriminals have utilized polymorphic subdomains to subtly alter the end of the sending address on each phishing email. This makes it nearly impossible for security teams to block each email as a new domain will pop up in place of every reported one.
Reputation-based detection
Similar to the concept of ‘known bad’ in signature-based detection, SEG technology also uses reputation-based detection to identify traffic from previously identified malicious domains. To do this it will look at pre-defined blocklists, the age of the domain and authentication checks such as SPF, DKIM, and DMARC. By gathering information on source, age and verification, reputation-based detection should be able to flag a malicious sender.
Some perimeter technologies will also employ social graphing checks to determine pre-existing relationships between accounts. Therefore, if two people have communicated over email before, the sender address is deemed to be ‘safe’.
But as with most legacy technologies, cybercriminals have found workarounds to successfully deliver attacks into a recipient's inbox.
Lookalike email domain
Another tactic we have seen utilised in 2024 is lookalike email domains. Unlike direct spoofs, lookalike emails have a few characters subtly altered, allowing the cybercriminal to set up proper authentication checks. Our Threat Intelligence team suspects that the ease of setting up authentication has contributed to the fact that 68.4 percent of the attacks that bypassed SEG detection in the first three months of 2024 passed all verification checks.
Legitimate but compromised accounts
In 2024, nearly half (48.3 percent) of the attacks that bypassed an SEG were sent from legitimate but compromised accounts. Whether this is from within the target's own business, supply chain, or a third-party account not linked to their organization at all, a compromised account is highly likely to bypass reputation-based technology.
If the attack originates from within the recipients supply chain, compromised accounts can also ensure attacks bypass any type of social graph detection, as there will a pre-existing and therefore ‘safe’ relationship between the two accounts.
An attack in action- an example of the ‘perfect’ phishing email to bypass SEG technology
Below, our Threat Intelligence team have put together the ‘perfect’ attack to bypass legacy technology. Whilst there are other psychological factors that come into play, we have focused on three key reasons why it would bypass reputation and signature-based detection.
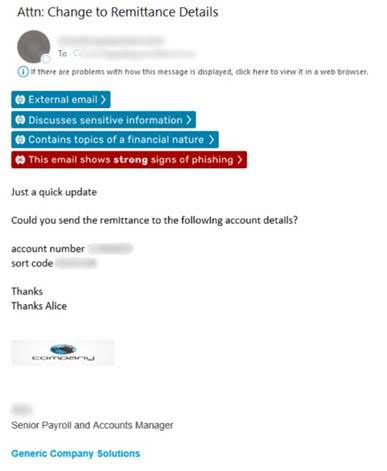
1. This phishing email has come from a legitimate but compromised account in the recipient’s supply chain meaning that the email will pass all authentication checks.
2. The cybercriminal has hijacked an email chain, meaning there is a pre-existing relationship between the sender and recipient. Consequently, this would pass any social graph checks.
3. The attack is purely linguistic, meaning there is no physical payload for signature-based detection technology to scan for.
Adapting to the new era of phishing attacks
As cybercriminals evolve their strategies, the limitations of legacy SEGs become more apparent. The rise in sophisticated phishing threats like polymorphic attacks, social engineering tactics, and the use of compromised accounts have undoubtedly highlighted the significant gaps in perimeter technology, leading to a notable increase in bypassed attacks.
Old habits die hard, but to effectively counter these advanced threats, organizations should consider transitioning to integrated cloud email security (ICES) solutions. By leveraging AI-powered, behavioral-based detection methods and adopting a zero-trust approach, these modern solutions offer superior protection, ensuring that even the most advanced attacks are detected, mitigated and neutralized.
Image credit: bloomua/depositphotos.com
Jack Chapman is SVP of Threat Intelligence at Egress, a KnowBe4 company
