
Why dev teams need observability to make sense of Kubernetes clusters
As cloud-native applications and microservices become more complex, developer teams struggle to make the most out of their infrastructure. Observability can cut through cluttered architectures to connect key engineering decisions to business metrics.
Driven by a constant mission for faster performance, improved efficiency, and enhanced business outcomes, developer tools change rapidly to meet the increased pressures on engineering teams. While these tools move in the direction of progress, the pace of change means that dev teams sometimes miss the forest for the trees, and today, one of the industry’s most widely-deployed tools is also its most misunderstood.

Threat hunting on a budget -- it's not as hard as you think…
Global losses from cybercrime now total more than $1 trillion, recent figures indicate, meaning that every business now must implement an effective threat hunting program has to protect its data security -- and long-term future. Establishing a threat hunting program from scratch may seem daunting, but it doesn’t have to be. Like so many things in life, the hardest part is taking the first step.
Even on a tight budget, numerous tools -- with SIEM, logs, and analytics -- can help security professionals start a robust threat hunting program. Below are the three main steps involved:

Change automation: A step-by-step guide to network security policy change management
In today’s fast-paced, data-driven environment, the only constant that businesses can bank on is change. For organizations to function and compete in the modern digital landscape, they need their data to be able to move freely and unobstructed through every branch of their business, unimpeded by security issues that require constant manual attention.
The network is arguably the beating heart of an organization but keeping it ticking requires more maintenance than it once did, owing to constantly changing risk profiles and circumstances. That’s why a greater number of businesses are turning to change automation to bridge the gap between network alerts and the action that needs to be taken.

$12 million lawsuit -- when digital consent management goes wrong
A $12 million lawsuit against video game developer, Capcom was launched by US photographer, Judy Juracek earlier this year for allegedly using 80 of her images without her consent. Last year, another US photographer, Mathilde Gattoni’s $2.25 million lawsuit against Microsoft claimed that it used 15 of her images for an MSN article without a license or her permission. Lawsuits for copyright infringement against corporations are showing no signs of abating.
It's not only photographers asserting their intellectual property rights, it’s amateur photographers who have taken photographs that have been lifted such as the case of storm chaser Sean Heavey, who spotted his image used by Netflix to promote its series, Stranger Things. The photographer, who was initially dismissed by the streaming giant allegedly, saw his case later settled out of court.

Five CRM strategies for better customer retention
With the rapid advancement in technology, organizations are constantly grappling with challenges in effectively retaining and increasing their customer base. This challenge is compelling progressive organizations to embrace the best customer relationship management (CRM) strategies for success.
Despite the focus on customer needs and customer-centricity, many organizations worldwide continue to take a reactive approach to customer needs. They, therefore, miss out on creating a long-lasting, partner-like relationship with them. Given the level of competition in the market today and the infinite options customers have, making customers a business priority is highly critical to satisfy and retain them and drive the required levels of trust and loyalty. This means clearly understanding their actual pain points and developing solutions that resolve those pain points – instead of trying to fit them into your service.

Shopify in 2021: Staying at the top of the online retail game
It’s been a while since the world shifted its shopping habits from offline to online modes. Smart retailers had realized the need to deliver a purchasing experience that was independent of the consumer's location. And online retail stores solved that need.
The growth of online retail is nothing short of a fairy tale. Back in 2014, total retail eCommerce sales worldwide reached $1336 billion in value, and it is projected to hit $6388 billion by 2024 at a staggering CAGR of 16.93 percent!

Why managing your own IT could lead to costly downtime
If there’s one thing that all businesses can agree upon it’s that time equals money. It’s the reason why organizations large and small all over the globe are on the constant lookout for ways to boost productivity and performance -- all while maximizing resources and lowering costs.
This is especially true when it comes to your IT infrastructure. Not only is it (probably) the backbone that keeps your business running smoothly and competitively, but it is also a considerable investment in itself. Whenever it isn’t operating, businesses are quite simply hemorrhaging money.

Security testing: Essential or simply supplemental?
A 2019 study on the effectiveness of enterprise security strategies found that 53 percent of enterprises are clueless if their security tools are working. This means that they do not undertake security testing. If they have anything that has the guise of security validation, it is likely inconclusive or conducted in an unsystematic manner.
However, a more recent study found that around 70 percent of organizations perform penetration tests as a way of preventing cyber breaches. Many already acknowledge the importance of testing their security controls. This finding coincides with a report that says that the global security testing market is huge and rapidly accelerating.

Bolstering business resilience in a world of incessant risk
Today’s business environment is fraught with risk. Whether it be financial, economic, security, compliance, reputational or operational, the business risk landscape is constantly evolving and always changing.
But what we’re learning, as we’re continuing through this era of digital transformation en masse, is that organizations best prepared to manage and minimize risk potential are those that are structured in a way that enables them to recognize objective risks, respond to them, and evolve alongside shifting market dynamics -- quickly and at scale.

How to find the 'sweet spot' with low-code automation
Today, low code is all the rage, with the worldwide low-code development technologies market expected to reach $13.8 billion this year, according to Gartner. One major factor driving investment is hyper-automation, as organizations look to quickly identify and automate appropriate business and IT processes.
It’s no surprise robotic process automation (RPA) and citizen automation and development platforms (CADP) are two of the technologies seeing jumps in revenue, pointing to the current interest in low-code automation.

Use AI to beat the bad guys
As we enter the back half of 2021 there are two top cybersecurity headlines, and they’re both sobering. One, even large organizations now suffer cyberattacks as a near-daily fact of life -- not just mid-sized businesses with resource-strapped SOCs (Security Operations Centers), which historically felt the most pressure.
Two, prevention-forward defense strategies no longer inspire confidence. Malicious, innovative use of AI to find and exploit fruitful attack vectors sees to that. AI has rendered many old go-to defenses less effective, namely firewalls and SIEM (security information and event management) solutions. The third headline, however, is cause for optimism. AI works for cyber defense, too. In the current environment, if you are not leveraging AI to defend your organization, it isn’t optimally defended. Period. I see AI as our greatest ally to create a secure future.

The fall back-to-school tech most worth your money in 2021
The past year or two have been chaotic for parents and students alike due to the COVID-19 pandemic. Transitioning from traditional, in-person learning to a hybrid or fully remote learning environment proved challenging for many students.
As we enter the latter half of 2021 and begin a new school year, it’s critical to see this moment as a fresh start -- and with a fresh start comes new technology! Students will need the latest and greatest tech to get them through the school year. Whether it’s a new pair of headphones or a snazzy new laptop, consider the six items listed below during your back-to-school shopping experience.

Overcoming the challenges of IPv4 exhaustion
As hundreds of regional communications service providers rush to deploy broadband and add thousands of new subscribers to their networks, they face a long list of tasks and budget items to be addressed. Most of the budget and buildout schedule will focus on the physical deployment of the fiber (FTTH) or wireless access. However, back in the core network, one of the important decisions -- and one that needs to be made early in the planning process for a network buildout or expansion -- is how to approach IP connectivity.
Given the exhaustion of IPv4 addresses, and the cost and complexity of migrating from IPv4 to IPv6, operators need to think carefully about how they will provide an IP address for every customer. After all, a network won’t run without IP connectivity.

If cloud technology is the need of the hour, then why do organizations resist adoption?
As we continue our journey through the extended new normal of the pandemic, it is crystal clear that to survive and thrive, companies will have to adapt to be able to respond to the ever-evolving needs of today’s digital consumers. It is not an exaggeration to say that today a successful business needs to be responsive, scalable, secure, and resilient. In this context, one of the most vital strategic decisions that can be made by most organizations is the accelerated shift of their legacy IT infrastructure to 'Cloud Technology'.
According to an IDC report, it is expected that by the end of 2021, approximately 80 percent of the enterprises will put a mechanism in place to shift to cloud-centric infrastructure and applications at a rate double or more of what it was before the pandemic. However, in this race of cloud adoption, many organizations do not have a clear picture of what they want and often underestimate the challenges involved in cloud migration. Lack of appropriate research, the correct approach and the right service provider leads to organizations ending up getting their hands burnt, leading them to put their plans on the backburner.
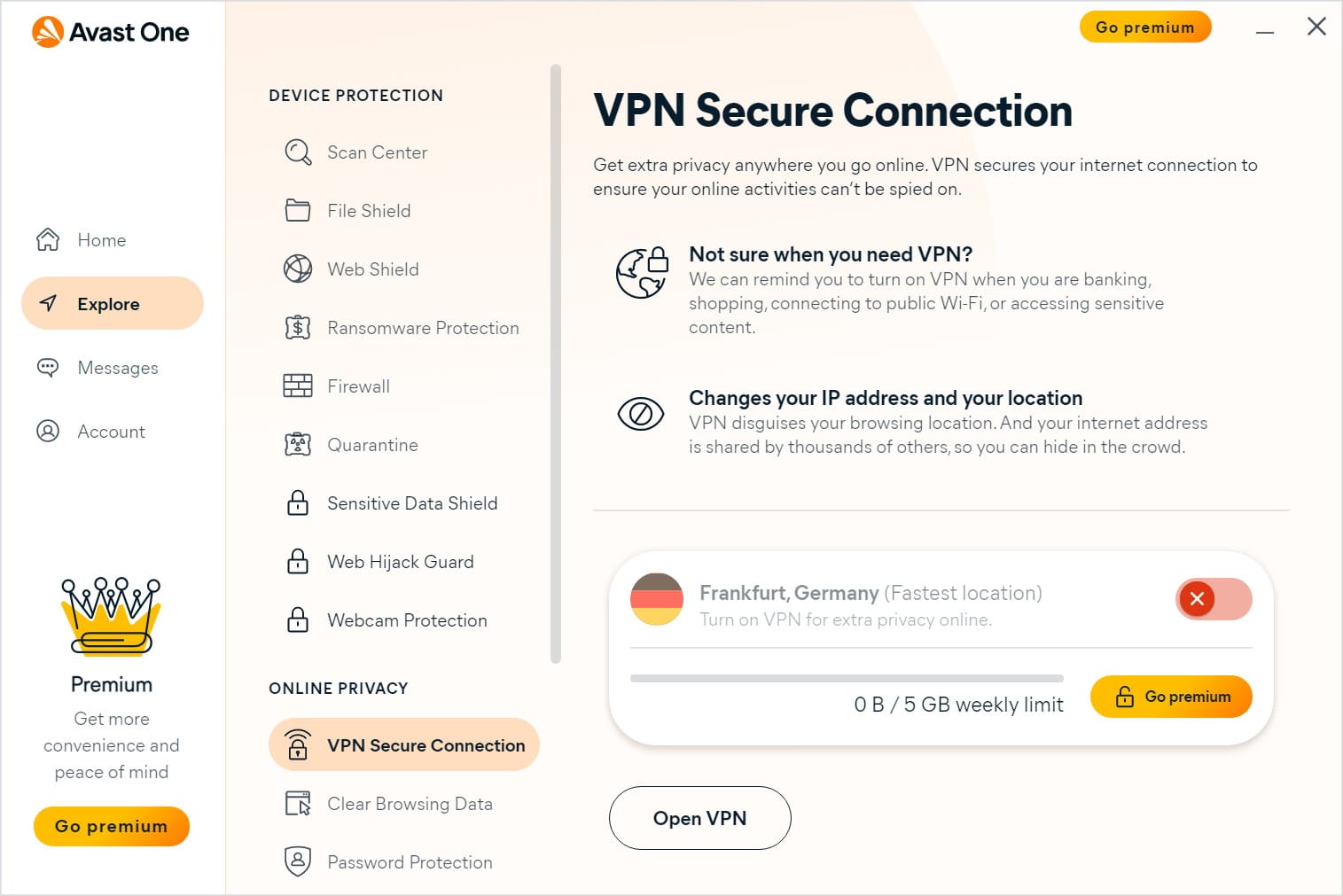
Avast One is a comprehensive privacy and security suite that includes a free VPN
Released at the same time as the company undergoes a redesign involving a new logo, Avast One is here to help keep you protected online. This is more than just an antivirus tool -- although an AV component is present -- this is a comprehensive suite of protective tools covering various aspects of security and privacy.
Things start off with Avast One Essentials, which is the free version of the security suite. For anyone with concerns about privacy, even this free version includes a powerful VPN with a generous weekly allowance. There is also protection against spyware, password theft and identity theft. And there is even more to explore in the paid-for editions.

