Sunvell T95X TV box: a web-focused, cloud-based client for those on a budget [Review]

Businesses often envision the modern desktop computer as being a boring piece of kit, one that not only costs a lot of money but also doesn’t offer much in terms of innovation.
The reality is slightly different; between dongle PCs, mini and micro PCs as well as all-in-ones, there’s plenty of innovation around if you know where to look.
Watching users fail is key to building a good product

Just 40 hours of engineering work to go live with a state-of-the-art smartphone application? It’s only possible if you have the right framework and if you forget perfectionism in favor of real user feedback. At Spreadshirt, we want it to be easy for our users to buy, sell, create and share ideas on over 200 products on our ecommerce platform. Whether they use a desktop, tablet or smartphone, we want our users to have a great experience.
Back in 2014 we had created a t-shirt designer for tablets, to reflect the rise of the touch screen. It worked on smartphones, but that was a rare use case back then. This web app has been perfected through many iterations. But the mobile times changed. And exactly as we had already envisioned in 2016 smartphone traffic was up 22 percent and tablet traffic was down at less than 10 percent. We needed a new design tool to focus on the experience for our visitors from smartphones and find out what their specific needs and issues were. Watching users fail holds the greatest learnings when you develop complex applications, such as our smartphone t-shirt designer.
How to scale a microservices-based app

The promise of microservices is that you can divide and conquer the problem of a large application by breaking it down into its constituent services and what each one actually accomplishes. Each can be supported by an independent team. You get to the point where you can break the limits on productivity that Fred Brooks described in his book, The Mythical Man-month.
Aside from being able to throw more people at the problem and -- unlike what Brooks observed -- actually become more efficient once you get a microservices-based application into production, you can quickly start thinking about how to scale it. Think resiliency and high-availability. And you can easily determine what services don’t need scaling, or high availability.
The future of self-driving cars relies on big data

Autonomous cars depend on information. They’re equipped with technology to gather and communicate a vehicle’s position, speed, direction, and braking status. They also recognize traffic signals, proximity to pedestrians, and hazardous objects on the road. With voluminous data being computed in near real-time, self-driving cars can respond to dangers afoot or notify the car owner of imminent mechanical issues, in which case it might automatically set up an appointment with the nearest auto body shop.
In addition, self-driving vehicles aren’t disposed to human-prone errors resulting from distracted driving, tired driving, or driving while inebriated. They’re constantly alert, vigilant, and have a panoramic view of the road. All of this demonstrates how big data is becoming the cornerstone to the driverless car’s future. What’s more, it’s already making great strides toward self-driving capabilities, driver safety, and enhanced customer experience.
Your clouds don't need to clash

Increasingly, two models for cloud are emerging -- the public or shared cloud and private cloud. While the definitions of these models might still be fluid, that has not stopped the rise of loud, passionate defenders of each who are willing to fight to the death to defend the idea that their cloud model will ultimately reign supreme. Needless to say, this "clash of clouds" can be intimidating for many enterprise IT professionals seeking to develop a cloud strategy where it might seem the wrong choice could result in the end of their business (or at least their careers).
Relax.
Low code/no code development: Is it right for you?

Research carried out by Gartner, which predicted that the demand for mobile applications would outstrip the number of app developers by 2019, still looms large over the mobile app industry. The way CTOs and CIOs cope with the developer shortage could make or break their company’s technological expansion.
To face this shortage, IT departments have two options:
What's next for the IBM mainframe?

The IBM mainframe has been a stalwart platform for enterprise computing for the last 50 years. There are not many technologies you can point to that have survived that long and remain a key component of many companies’ IT infrastructure. Its survival should be lauded, but the question remains: "Is it the only game in town for enterprise computing?"
That answer is a resounding "No." The mainframe is a combination of hardware and software that is arguably unique to all other computing offerings available in the marketplace today. That doesn’t make it a bad platform, but it does limit its opportunities for growth. It is a proprietary platform, only available from a single vendor -- IBM.
Galileo atomic clocks failed: What can we learn from it?

Galileo has been making headlines once again, and this time not for the right reasons. It was reported on January 18, 2017 that several of the atomic clocks responsible for the satellites’ ability to calculate precise time have failed.
Timing is everything in GNSS -- very precise time is required to calculate an accurate value of the delay in receiving signals that have been transmitted from a given satellite. This allows users to determine their position on Earth accurately. Also, many applications today take advantage of the very precise timing that GNSS can provide via the atomic clocks in use on the satellites.
Verizon sells 29 data centers to Equinix for $3.6bn

Global data center company Equinix has bought 29 data centers, along with their operations, from Verizon Communications. Approximately 250 Verizon employees will also become Equinix employees in the process.
The deal, worth $3.6 billion, will be completed in all cash. It includes more than 1,000 customers, 600 of which are net new. Verizon will now, consequently, become a substantially larger customer. It also includes roughly a million square meters of data center space.
Big data will be a $76bn market by 2020

Big Data is now a $57 billion market, according to a new report from SNS Research. Entitled The Big Data Market: 2017 - 2030 -- Opportunities, Challenges, Strategies, Industry Verticals & Forecasts, it says that vendors will be earning from hardware, software, and professional services revenue.
What’s more, the report says the investments are expected to grow at a CAGR of roughly 10 percent over the next four years, reaching $76 billion by the end of 2020.
The gig economy has flipped the job market on its head

Today, CISOs are facing a much different set of challenges than they were 20 years ago. From a marked increase in the risk of breach to the growing difficulty in filling security jobs these security leaders are facing an uphill battle. Add to that the pressure to provide security assurance to the board and it’s easy to see why more organizations are harnessing the power of the gig economy.
In the last few years the gig economy has flipped the job market on its head. From ordering groceries to renting a house for a week, the gig economy has opened up new revenue channels for businesses and income opportunities for individuals. But while the issues that have driven this market -- difficulty hiring, a distributed workforce, and people spending less time at companies -- are nothing new, it was the maturity of software that enabled the gig economy to really take off.
Is it time to replace the VPN?

It’s time to replace the traditional VPN and regain trust of your endpoints with a more secure and easier approach to remote access. VPNs have typically been the go-to solution for access to internal applications, with one-third of access requests to corporate networks coming from outside the firewall.
However, VPNs come with security drawbacks, including the increased risk of unauthorized remote access to sensitive data. Typically, they grant access at the network level, meaning every user with VPN rights can access the same applications that any other user can, which is a risky practice.
Microsoft is replacing the password -- what's taking its place?

It was supposed to have died a long time ago, but, for a near-cadaver, the password has managed to hold onto its last breath for over two decades. Bill Gates declared passwords passé way back in 2004, but it was only late in April that the company he founded introduced a replacement for the outmoded authentication system.
For years, organizations have sought to educate employees about the importance of secure passwords and of resisting phishing attacks -- and both efforts have failed. A Verizon report indicates that 63 percent of confirmed data breaches involved leveraging weak/default/stolen passwords in 2016. Meanwhile, a new report from Proofpoint says that phishing and similar attacks using e-mail were up 45 percent in the last quarter of that year. Clearly, the constant haranguing by security teams of employees to change their passwords and make them more complicated, as well as their pleas not to click on suspicious links/attachments, are falling on deaf ears.
Ransomware's biggest target is the healthcare sector

Ransomware grew 50 percent in just a year, according to a new report by Verizon. The Verizon Data Breach Investigations Report (DBIR) is based on the analysis of 79,000 security incidents and 1,945 confirmed data breaches, across 79 countries.
According to the report, ransomware also grew in popularity, and by a large margin. In 2014, it was the 22nd most common malware variety. Fast-forward two years, and now it’s fifth most common.
Hajime botnet controls nearly 30,000 devices
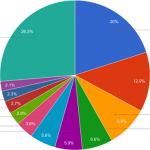
Hajime, a mysterious IoT botnet, now controls almost 300,000 devices, according to a new report by Kaspersky Lab. The report also states that the botnet's true purpose is still unknown.
Kaspersky says the malware, whose name means "beginning" in Japanese, first appeared in October 2016. Since then it has evolved into a decentralized group of compromised machines that discretely perform either spam or DDoS attacks.
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.
