
Facebook tops the data loss roll of shame
Data breaches have almost become a fact of everyday life, but there are still some that have greater impact than others.
Software company Intact has carried out an analysis of publicly available data to see which companies have suffered the most large-scale data breaches (involving more than 30,000 records or more) over the last 16 years.
Best Windows 10 apps this week
Four-hundred-thirty-four in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
Microsoft removed Timeline's activity history sync feature in preview builds. Timeline is changed to a local activity history tool. The company removed the official Microsoft Translator application as well this week from the Microsoft Store.

How improving security management can help protect the cloud [Q&A]
Cloud misconfigurations are one of the major causes of data breaches and the problem has become worse thanks to the dash for remote working.
While cloud is undoubtedly the right choice for businesses looking to expand their infrastructure to keep pace with DevOps demands and embrace support for remote working, many enterprises are falling short of providing adequate Cloud Security Posture Management (CSPM).

KB5001330 update for Windows 10 is causing performance problems and other issues
Earlier this week we asked -- slightly tongue-in-cheek -- what problems would be caused by this month's Patch Tuesday updates. As the weekend crests the horizon, we have our answer, and this time around it is the Edge-killing KB5001330 update that is proving problematic.
And the problems appear to be not only plentiful, but also fairly significant. Among the reported issues are a drop in the performance of games, error messages, screen flicker and more.

Don't be fooled into not backing up your data!
We celebrated World Backup Day last month. Started in 2011 by digital consultant Ismail Jadun it is observed on March 31st every year -- a date chosen because it’s the day before April Fools Day… and of course you’d have to be a fool not to backup your data!
This especially recognized day is a strong reminder of the increasing role data plays in our lives and of how critical it is to backup all of your data. Regardless of the size of your organization, it’s likely that data is an essential aspect of running it. If you don’t yet have a solid plan to keep your data safe, there are four things you should consider:
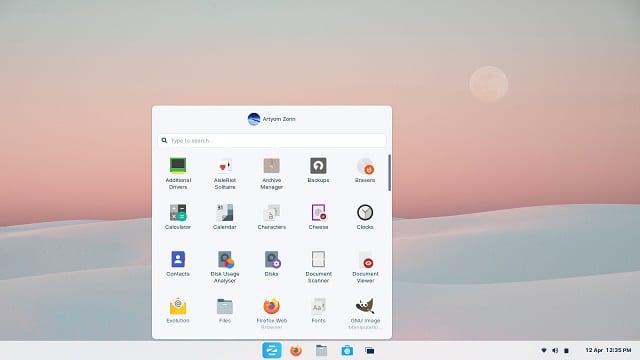
Zorin OS 16 Beta Linux distro is here, with Microsoft Windows 10X mode coming soon
A lot of people hate Windows 10, but I think it is actually quite good. With that said, I'd much rather use a Linux distribution such as Ubuntu or Fedora. With Linux, I feel more safe and secure. No operating system in infallible, but bad guys are more likely to write malware for Windows. Not to mention, Microsoft does "spy" on its users with extreme telemetry. Ultimately, with Linux, I feel like I own my computer. Conversely, with Windows, it can feel like Microsoft owns my PC.
Understandably, switching from Windows to Linux can be a scary affair, but it doesn't have to be. Some Linux distributions look a bit like Windows, so there is a degree of familiarity. Not to mention, with so much being done in the web browser nowadays, the underlying operating system becomes less important. In other words, just having Google Chrome available makes Linux a viable option for most home users these days.

Interaction Analytics supports compliance in your contact centers
Every contact center needs to track its compliance with laws and regulations, yet so many make it tougher on themselves to do so. Reviewers screen call after call, checking off compliance steps and ensuring agents meet expectations. But with potentially millions of calls to screen, manual compliance tracking becomes an impossible task -- and workaround solutions can leave centers open to damaging compliance failures, potentially costing companies millions of dollars in fines.
The cost of human error is too high, but manual processes are too overwhelming, time-consuming and expensive. Automating compliance monitoring can remove much of the burden from compliance managers and officers and decrease their chances of human error. Technology like Interaction Analytics helps reduce the traditional pain-points and limitations in reviewing contact center compliance while also unlocking insights on larger trends and ways to improve contact center operations.

EFF and DuckDuckGo's new partnership is about enhancing secure browsing and protecting user information on the web
Although most web browsers now automatically switch you to the secure HTTPS (Hyper Text Transfer Protocol Secure) version of a website if you try to go to a non-secure HTTP address, the EFF (Electronic Frontier Foundation) offers another option.
Its HTTPS Everywhere add-on has been protecting users for over a decade now, and automatically sends your browser to the secure version of a site if it exists. Thanks to a new partnership with privacy-focused search engine DuckDuckGo, the tool is about to get even better at redirecting users.
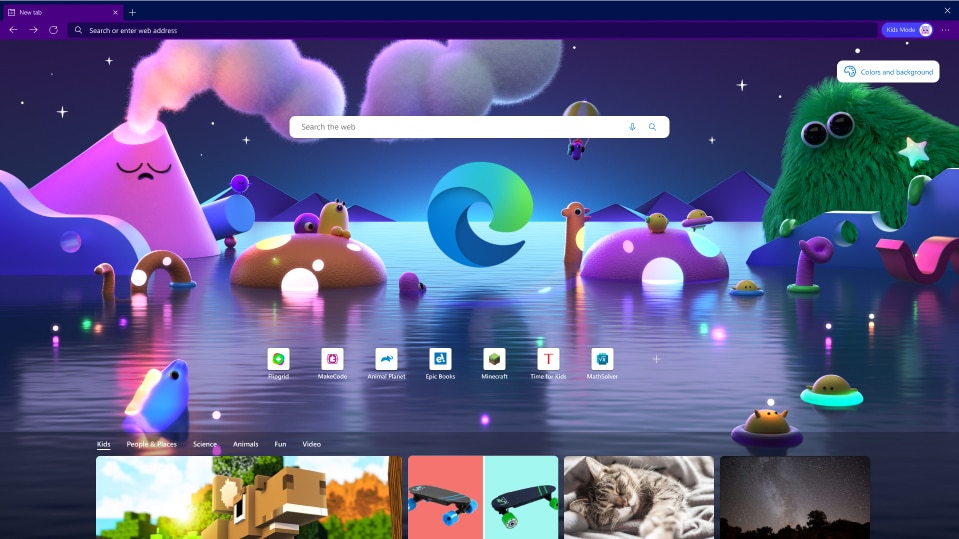
Microsoft adds Kids Mode to its Edge browser -- Here's how to launch it
Yesterday, Microsoft released two new updates for Windows 10 that, among other things, killed off the legacy Edge browser. There’s no question that the Chromium-based successor to that browser is a huge improvement, and today the software giant makes it even more useful for families.
The new Microsoft Edge Kids Mode gives parents more peace of mind when their offspring are browsing the web, which is great news as children are online more than ever these days.

Patriot launches VIPER VP4300 M.2 2280 PCIe Gen4x4 solid state drive for PC gaming
The transition to PCIe 4.0 is in full effect, with more and more computers and motherboards having the new standard. Whether or not the user truly needs the benefits of PCIe 4.0 is debatable, but it is still cool regardless. After all, it is important to continually push boundaries. "To Infinity and Beyond!" as the great Buzz Lightyear says.
One of the best aspects of PCIe 4.0 is faster solid state drives. For instance, today, Patriot launches a new such SSD under its VIPER gaming brand. Called "VP4300," this speedy M.2 2280 PCIE Gen4x4 SSD comes with interchangeable heatsinks -- a very neat cooling option. Essentially, you can opt for the thicker aluminum heatsink if it fits in your computer, or the thinner graphene heatsink if space is tight -- both come included in the box.

Save 60% on the updated Avast Antivirus 21.3 which boasts better scanning performance, Rescue Disk improvements and more
Avast Antivirus 2021 has just received its April update, and it's an important one. In addition to the usual array of bug fixes and improvements, there are also some serious changes and additions to enjoy. Chief among these are big improvements to scanning, helping to boost the overall performance of the software.
There have also been changes to the way notifications work in the app. While you, of course, want to be made aware of things that need your attention, an overload of notifications can be annoying. And it is with this in mind that the latest version of the app will no longer show you pop-up messages when you have the antivirus tool open. But it does not end there.

Get 'The Innovation Ultimatum: How six strategic technologies will reshape every business in the 2020s' ($17.00 value) FREE for a limited time
Most businesses identify six key digital technologies -- artificial intelligence (AI), distributed ledgers and blockchain, the Internet of Things (IoT), autonomous machines, virtual and augmented reality, and 5G communication -- as critical to their relevance and growth over the coming ten years. These new disruptive technologies present significant opportunity for businesses in every industry.
The first businesses to understand automation and these transformative technologies will be the ones to reap the greatest rewards in the marketplace. The Innovation Ultimatum helps leaders understand the key technologies poised to reshape business in the next decade and prepare their organizations for technology-enabled change.

CISOs face rising security debt as attacks increase
CISOs are facing a battle to secure their organizations against an increasing volume of attacks by well-armed criminals and are facing a rising ‘security debt’ in doing so.
But a new report from cyber security provider F-Secure in conjunction with Omnisperience finds security teams are turning away increasing volume of attacks and preventing more of them from becoming breaches or compromises.
Microsoft pushes improved Windows Terminal 1.7 to the stable channel
After a period of testing, Microsoft has now launched the stable version of Windows Terminal 1.7. There are various notable changes in this release, particularly the arrival of a proper UI for editing settings.
The idea behind the introduction of a settings user interface in Windows Terminal v1.7.1033.0 is that it makes life a great deal easier for anyone who is not familiar or comfortable with JSON file tinkering. Significant as this is, it is not the only change to be found in this new stable release.

Microsoft is making Windows 10's Timeline feature far less useful
With the release of the latest insider preview of Windows 10, Microsoft has made a key change to the way the Timeline feature works. The idea behind Timeline was to not only provide a web browser-style history option for general computing activities, but to synchronize this history across devices via the cloud.
Now Microsoft has decided that the cross-device synchronization side of things is not needed, and the company is getting rid of what was arguably the most useful feature of Timeline. While currently only deprecated in the Windows 10 Build 21359 preview, this is a change that will ultimately roll out to all Windows 10 users.