Celebrity chef Jamie Oliver serves up an unpleasant malware surprise
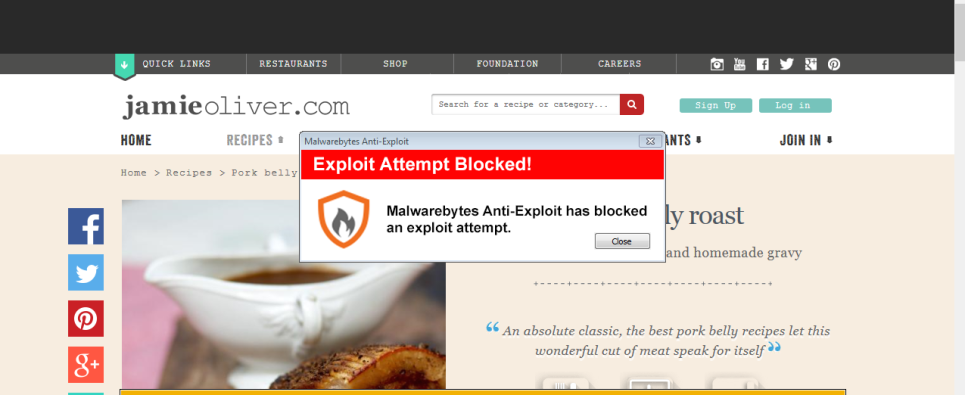
Most web-based threats come from malicious adverts placed on websites (aka malvertising), but Malwarebytes has discovered a well hidden malicious injection on the official website of Jamie Oliver which redirects unsuspecting visitors to an exploit kit.
The compromised site -- www.jamieoliver.com -- is currently ranked 519 in the UK (5,280 in the world), according to Alexa, with around 10 million visitors a month, which makes it a valuable target for hackers.
According to Malwarebytes, the malicious JavaScript injection creates an iframe and uses a second compromised site to redirect visitors to an exploit kit landing page where at least three exploits (Flash, Silverlight and Java) are launched. If the PC is not fully patched, a malicious dropper (Malwarebytesidentifies this as Trojan.Dorkbot.ED) downloads and runs.
Once infected, users face search engine hijacks, and the danger of being tricked into downloading malicious software updates.
As to how the compromised JavaScript found its way onto the site in the first place, Malwarebytes isn’t sure. "It could be a legitimate script that has been injected with additional content or a rogue script altogether" says senior security researcher Jérôme Segura. He also speculates that the cause might not be a plug-in at all but "perhaps stolen credentials".
You can find out more about the discovery on the Malwarebytes Unpacked blog.