AutoCAD worm is serious example of suspected industrial espionage
The new, targeted, high-tech, military grade malicious code such as Stuxnet, Duqu and Flamer dominates security news. So imagine our surprise when an AutoCAD worm, written in AutoLISP, the scripting language that AutoCAD uses, suddenly showed a big spike in one country on ESET’s LiveGrid two months ago, and this country is Peru.
We have seen other small number of infections of ACAD/Medre.A in other countries, but they are all in regions that are near Peru or have a large Spanish speaking contingent. The odd one out in the infection table would be the People’s Republic of China, but not quite so weird when we started to analyze the worm based on this sudden spike. More about China will follow later.
Why (mainly) Peru? Of course it does not mean much that we see high detection numbers because they may not all be live infections. But watching ESET’s LiveGrid, where we can also see detections at specific URLs., which made it clear that a specific website supplied the AutoCAD template that appears to be the basis for this localized spike as this template was also infected with ACAD/Medre.A. If it is assumed that companies that want to do business with the entity have to use this template, it seems logical that the malware mainly shows up in Peru and neighboring countries. The same is true for larger companies with affiliated offices outside this area that have been asked to assist or to verify the, by then, infected project and then infecting their own environment. Other information that is described later also points to live infections.
So what exactly is ACAD/Medre.A doing?
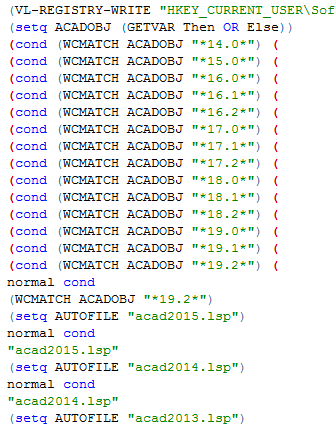
The sample is able to infect versions 14.0 to 19.2 of AutoCAD by modifying the corresponding native startup file of AutoLISP (acad.lsp) by being named as the auto-load file acad.fas. It employs Visual Basic Scripts that are executed using the Wscript.exe interpreter that is integrated in the Windows operating system since Windows 2000. The author assumes that his code will even work for future versions of AutoCAD as it has support for the AutoCAD versions that will be released in 2013, 2014 and 2015.
 After some configuration, ACAD/Medre.A will begin sending the different AutoCAD drawings that are opened by email to a recipient with an email account at the Chinese 163.com Internet provider. It will try to do this using 22 other accounts at 163.com and 21 accounts at qq.com, another Chinese Internet provider. Remarkably, this is done by accessing smtp.163.com and smtp.qq.com with the different account credentials. It is ill advised to have port 25 outgoing allowed other than to your own ISP. Obviously the Internet Providers in Peru do allow this. Also it is reasonable to assume that the companies that are a victim of this suspected industrial espionage malware do not have their firewalls configured to block port 25 either.
After some configuration, ACAD/Medre.A will begin sending the different AutoCAD drawings that are opened by email to a recipient with an email account at the Chinese 163.com Internet provider. It will try to do this using 22 other accounts at 163.com and 21 accounts at qq.com, another Chinese Internet provider. Remarkably, this is done by accessing smtp.163.com and smtp.qq.com with the different account credentials. It is ill advised to have port 25 outgoing allowed other than to your own ISP. Obviously the Internet Providers in Peru do allow this. Also it is reasonable to assume that the companies that are a victim of this suspected industrial espionage malware do not have their firewalls configured to block port 25 either.
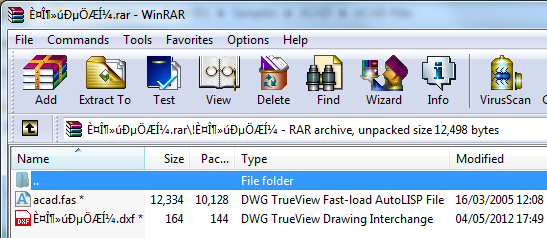
Besides the drawings that are sent, ACAD/Medre.A will create a password protected RAR-file containing the drawing and the requisite “acad.fas” file and a “.dxf” file and send it separately by email. The password used, just one character long being “1”, on the RAR-file brings back some memories (you may remember that Win32/Bagle used the same password on RAR-files).
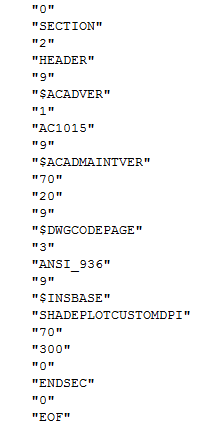
The included .DXF file is generated by ACAD/Medre.A and consists of information that the recipient needs to load the stolen drawing into the right system with the right language:
 For a technical details of ACAD/Medre.A refer to Robert Lipovsky’s blog post and the description in ESET’s Threat Encyclopedia.
For a technical details of ACAD/Medre.A refer to Robert Lipovsky’s blog post and the description in ESET’s Threat Encyclopedia.
When our analysts looked into the email accounts used by ACAD/Medre.A, they noticed that the Inbox for each of them was already full (over 100,000 mails). All of the messages In the Inbox were error-messages as the Inbox of the final recipient is full. And there were still almost 5,000 emails to be sent.
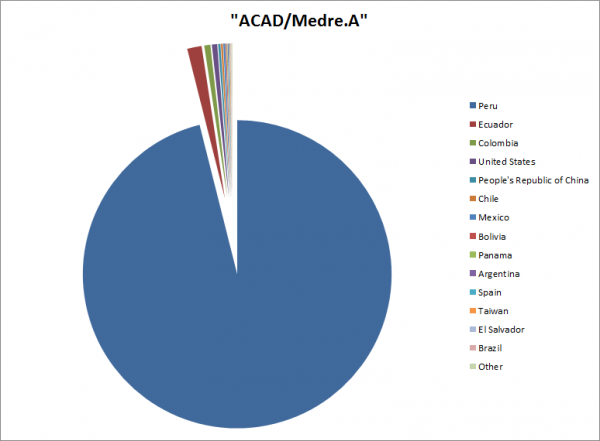
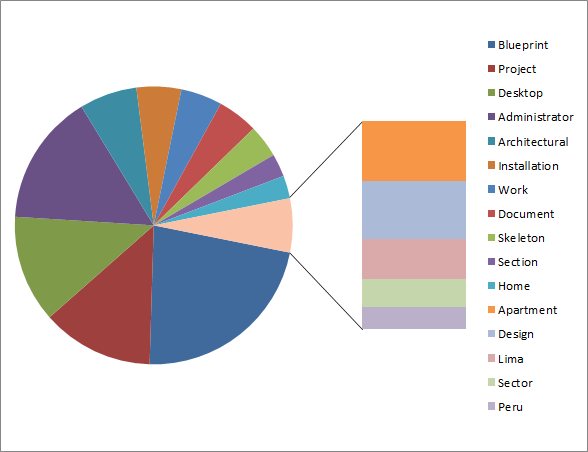
As the path and filename are sent with the attachment, we could do some analysis just based on the location where the drawings are stored and their possible content. Our analysis also shows that several people actually use an Administrator Account or store their projects on the Desktop. The pie-chart does not reflect all the different possibilities, just the most frequently used ones.
From our analysis of all the used email accounts we can derive the scale of the attack and conclude that tens of thousands of AutoCAD drawings (blueprints) leaked. This is a significant amount of data leakage and we felt it called for further action. Upon realization of the magnitude of the problem ESET reached out to Tencent, owners of the qq.com domain. Due to swift quick action on the part of Tencent the accounts used for relaying the emails with the drawings have been blocked and thus no further leakage will occur. We would like to express our appreciation to the distinguished team at Tencent’s Desktop Security Business Division for their cooperation and their prompt action.
ESET has also reached out to CVERC, the Chinese National Computer Virus Emergency Response Center, and they also responded quickly by word of the First Deputy Director of CVERC, who also assisted in getting the accounts removed.
There is code in ACAD/Medre.A that will check to see if either Outlook version 11.0, 12.0 or 13.0 is present or Foxmail. If Outlook is present the worm tries to email PST files found on the computer to the final recipient in China via the qq.com relays. Outlook PST (Personal STore) files contain email, calendars, contacts, and more. If Foxmail is present, there is code in ACAD/Medre.A that is designed to exfiltrate the Foxmail Address Book and the Foxmail Send Folder, but errors in the code cause that this does not happen.
After the discovery of ACAD/Medre.A, ESET decided to make a free stand-alone cleaner available. The utility can be found here. We established contacts with Autodesk, producers of AutoCAD, who immediately took the problem seriously and full assistance was given.
ACAD/Medre.A is a serious example of suspected industrial espionage. Every new design created by a victim is sent automatically to the authors of this malware. Needless to say this can cost the legitimate owner of the intellectual property a lot of money as the cybercriminals will have designs before they even go into production by the original designer. The attacker may even go so far as to get patents on the product before the inventor has registered it at the patent office. The inventor may not know of the security breach until his patent claim is denied due to prior art.
If there is one thing that becomes obvious from our experience with this piece of malware it is that reaching out to other parties to minimize damage is not only the right thing to do, it really works. We could have tried to clean up the problem without the assistance of Autodesk, Tencent and CVERC and solely focus on removal of the malware from the infected machines. By working with Autodesk, Tencent and CVERC, we were able to not only alert and inform users but also defeat the e-mail relay system used by the attackers and deny them access to the e-mail boxes, so the damage is now contained.
Reprinted with Permission
 Righard Zwienenberg is a senior research fellow at ESET, where he joined in February 2012. He started researching computer viruses in 1988 after encountering the virus problems on a system at the Technical University of Delft.
Righard Zwienenberg is a senior research fellow at ESET, where he joined in February 2012. He started researching computer viruses in 1988 after encountering the virus problems on a system at the Technical University of Delft.