Meraki MX Firewalls: Why cloud managed networking simply rocks [Review]
Two of the largest network gaming services, Xbox Live and PlayStation Network, took unplanned hiatuses on Christmas Day 2014. And for their credit, both Sony and Microsoft were not the culprits for the outages. Newly infamous hacking group Lizard Squad used DDoS attacks against the gaming networks to chalk up part publicity stunt and part targeted advertising for their new DDoS-for-hire service.
At this point, the who and why of this story aren't anything new if you've been watching IT news the last few weeks. But something that hasn't gotten as much attention is the "how" of Lizard Squad's Xmas Day barrage last year.
Security analysis website KrebsonSecurity was one of the first to divulge the fact that LS didn't need powerful servers of any sort for their mayhem. Their weapon of choice? Compromised routers that were injected with malware which targets Linux.

Many network security professionals pledge allegiance to firewall mainstays like the Cisco ASA 5505 series. But even these firewalls represent an outdated model for front-line network security. Large majorities of these devices in the wild are running months, if not years, old editions of firmware. Keeping up to date on firewall software, especially in Cisco-land, is a laborious mix of licensing and careful maintenance. We left this entire mess behind when we moved over to a Meraki stack. (Image Source: TigerDirect)
But it wasn't just the home variety of routers that were the sole victims here, as many media articles focused on. KrebsonSecurity claims that the botnet which took down Xbox Live and PSN included numerous devices identified as commercial units, the kinds that businesses and organizations depend on for their first level of network security.
Per KrebsonSecurity:
The botnet is not made entirely of home routers; some of the infected hosts appear to be commercial routers at universities and companies, and there are undoubtedly other devices involved. The preponderance of routers represented in the botnet probably has to do with the way that the botnet spreads and scans for new potential hosts. But there is no reason the malware couldn't spread to a wide range of devices powered by the Linux operating system, including desktop servers and Internet-connected cameras.
While router models and families weren't specifically identified by the site, it's not hard to assume the devices that were potentially hit. Cisco small business firewalls? Cisco ASAs? Junipers? Sonicwalls? Watchguard Fireboxes? Take your pick, honestly -- it could be a mixture of all of the above.
While the aforementioned attack worked solely against devices that never had their default logins changed, it's not hard to extrapolate how these hackers could take their "router botnet hunting" to the next level, specifically looking for devices running older firmware which have known bugs exposed in the wild.
What's my point here, you may be wondering? Most of the tech news media seems to be brushing the common faulty denominator under the rug here: the status quo for firewall appliances (and home routers) related to network security is fundamentally broken. The IT industry needs a complete cleansing of its definition of "enterprise grade security" as far as I'm concerned.
The management, maintenance, and security model represented by most common network firewalls is irreparably antiquated already. At a time when Microsoft, Apple, and Google are patching their respective operating systems at blazing speeds just to keep pace with threats, how is it that the front lines of defense for our entire networks are being left to boxes running firmware which, in many cases, could be months or years old?
These swathes of firewalls and routers may be running minimalistic editions of Linux, reducing their attack footprint, but they are just as susceptible to eventual penetration, as cleverly exposed by Lizard Squad.
The Xbox Live and PSN attacks are just the tip of the iceberg. Lizard Squad has achieved proof of concept against the legions of insecure routers out there, and I must admit, there couldn't be a juicier target. These devices are known to run older Linux versions with known published exploits; there is no anti-malware software you can run on (most) routers; and without a doubt, there are few easy ways to realize you have been infected since most firewalls are sold with a notion of "set it and forget it."
This broken mentality is fundamentally flawed in light of cyber security realities that only continue to get worse. There has to be a better way of securing our virtual front doors.
Why The Firewall You Trust Could Be Your Worst Nightmare
If you've never put your hands on a cloud managed firewall like a Meraki MX device, then preaching its benefits by simply regurgitating a data sheet is meaningless. You can visit Meraki's website on your own if all you care about is specs and numbers.
There's a more important distinction that has to be understood before you can truly appreciate the concept of cloud managed networking. Because, as if it weren't already clear, I'm here to make the case that the "old guard" of firewalls out there (I'll refer to them as "legacy" devices, since that's what they represent in my eyes) are above all, security risks to your network.
You may be wondering how I could be labeling such devices like Cisco ASAs and Sonicwall TZ firewalls as security risks or "legacy" products. They're trusted by many network security experts and are some of the most popular in the commercial space today.
Well, popularity and price tags alone don't establish security benchmarks in my opinion. The groupthink of the IT industry as a whole has by and large allowed the status quo to fester into where it stands today.
Think about the following questions:
- Wouldn't it be smarter to have firewalls that didn't have any default credentials which hackers could easily cross reference?
- Wouldn't our networks be safer if firewalls had the same kind of automated patch routines which computers and servers enjoy?
- Wouldn't router administration and management be easier if we could access them securely anywhere via web browser, not just over CLI via a console cable?
- Wouldn't it be great to have the same powerful features of Cisco ASA and similar devices without having to learn complex CLI commands?
The above niceties aren't some kind of lofty thoughts we can only wish for. Meraki's entire line of firewalls already include all of the above aspects out of the box, and more.
For what it's worth, the traditional model of how firewalls are updated, maintained, licensed, and secured is flawed beyond repair at this point. Think about it. Routers/firewalls are nothing more than slimmed down computers running instances of Linux which are infrequently, if ever, updated.
As a managed services provider taking over for internal IT teams, I have yet to come across an IT staff that has had formal policies in place which include routine patching of their firewalls. None, zero, zilch. It's always an afterthought at best -- one which can cost them dearly with the right determined hackers at the other end.
I don't blame the IT staffs at these firms entirely. The firewall industry, especially in the commercial space, makes updating and maintenance a pain the rear. Cisco ASA devices, for example, can be updated in only one of two ways.
One involves the dreadful IOS command line, a CLI language exclusive to Cisco and which takes years to perfect as an IT pro. For the GUI crowd, there's the sole option of using Cisco's ASDM product -- a pitiful piece of software that must be locally installed and ironically runs on top of another ongoing, incessant security nuisance: Java. You just can't win in ASA land, which is why I am ridding them at customer sites as time goes on.
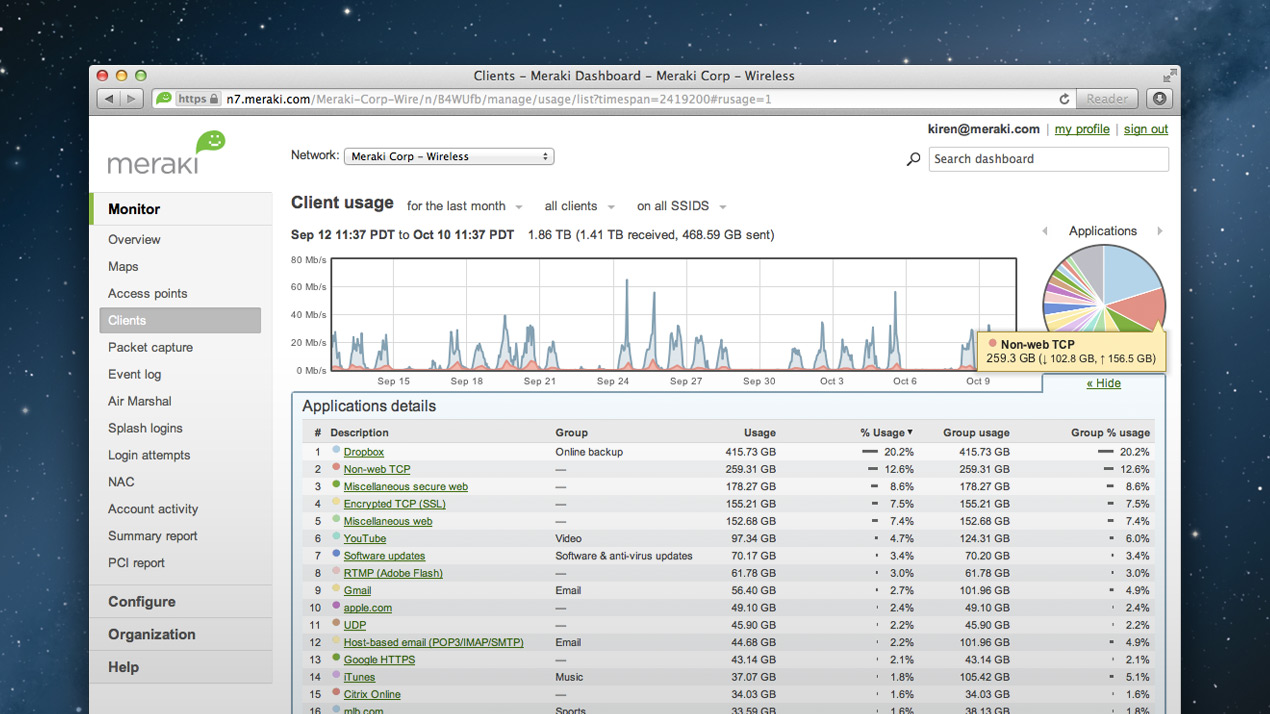
Say goodbye to confusing command line or tricky GUI interfaces (Sonicwall, ahem). All firewalls in the MX line from Meraki come with access to the holy grail of what sets Meraki apart: a clean, browser-based control console that administers (nearly) every aspect of Meraki units in a single pane of glass. It's extremely powerful, yet cleverly elegant. (Image Source: Meraki)
Another issue with the 'firewall status quo' today is that even if you run a device which managed to get infected, how would you ever detect the infection? Sure, some professionals may know how to watch egress traffic and monitor activity with other tools, but I have seen nothing out of the box that Sonicwalls and ASAs, for example, have to counter self-infection.
The anti-malware software landscape for Linux is fairly barren still, and literally non-existent for devices which run mission-driven editions of the kernel. It's the equivalent of picking up a terminal illness for which you can never detect or disinfect. Having a corporate network which depends on the blind trust that such an occurrence won't happen is just plain silly in 2015.
In fact, any customer wishing to bring my company FireLogic in as their managed services provider is now required to ditch their ASAs, Sonicwalls, etc in favor of a Meraki MX-based firewall. If we are going to be on the hook for their network security as a whole, we're going to require what we believe will give us the highest levels of security and management capability.
I didn't even mention the legions of units which run default admin credentials in production. I'm sure there are plenty of network admins guilty of this which don't even know it, either due to ignorance or due to delegation of duties to underlings which were never taught proper best practices. Especially if you're managing main offices with numerous branches, perhaps some you don't even have full control over, these could be ripe situations for login sets that never get changed.
In light of all the above, it's not hard to see why legacy firewalls are a broken category which have surpassed their usefulness.
My Initial Doubts about Meraki
As the owner of a managed IT services company, I get the luxury of putting my hands on all kinds of networking equipment. From firewalls, to access points, to switches and everything in between. Unlike most tech journalists that get the pleasure of playing with new gear merely in the luxury of their own home sandbox, we're busy dogfooding network gear knee deep in the field -- day in, day out. It provides the kind of discreet clarity for recommendations we can put our name behind.
So as you can imagine, I've seen my fair share of the usual faces in firewall security. Cisco ASAs? Been there. Sonicwalls? Done that. Fireboxes, Junipers, and even Untangle homebrews? Yes, I've seen them all, along with a plethora of other makes and models out in the wild.
While we've been fairly content with Cisco Small Business firewalls (RV042G and RV320 units, specifically), I've never been thrilled with them. They are more palatable than working with Sonicwalls or ASAs, but they don't shine in any fanciful way I can brag about. They work, they're fairly stable, and they get the job done -- which is why I've mentioned them in numerous articles over the last half year.
However, I'm never content with just skating by with the equipment we recommend. "Good enough" doesn't have the same veracity and comfort as "this thing rocks!" When I was first exposed to Meraki, I had some doubts about their claims of "cloud managed networking" as a whole, since I've always considered a firewall as a device which was updated and managed locally on the device itself.
Auto VPN, integrated malware/security scanning, and managing multiple disparate office networks in a single web dashboard? Nonsense, I thought. A gimmick at best -- and I've been a cloud champion for years already when it comes to email, collaboration, and VoIP services.
Upon recommendation from a good friend and industry colleague, we signed up for one of their webinars which tossed in a free Meraki access point upon successful completion of the session. What did I have to lose, I thought, and gave them an hour of my time. I was duly impressed, but couldn't make a full decision on how I felt until I could play with that AP they promised to send me (an MR12, if you're curious, which has since been retired).
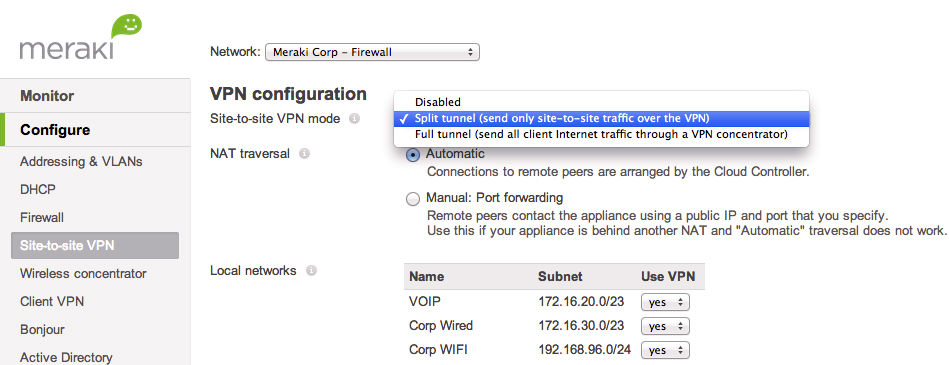
Traditional site to site VPNs are a messy affair full of preshared keys, algorithm matching, and other detailed trial and error. Meraki makes S2S VPNs easier than ever before, under a technology called AutoVPN. As long as branch offices are all on a Meraki MX-line device, establishing connectivity between two or more branches is a click-click affair. And for an industry first, you don't even need static IPs at your offices -- AutoVPN manages everything with a free integrated DNS hostname service. (Image Source: Meraki)
Nearly a year after my first taste of what Meraki had to offer, I can safely say that Meraki represents the face of the modern, scalable firewall -- v2.0, if you want to label it that.
After converting numerous high stakes clients, plus our own FireLogic office (and even my parents' home and my own condo) to Meraki firewalls, my view of every other staple appliance -- Cisco ASA, Sonicwall, Netgear, etc -- can be summed up with a simple statement.
In the words of the ever-so-honest-yet-blunt Kevin O'Leary (of Shark Tank fame), the non-Meraki fare is pretty much "dead to me" at this point. I'll hesitantly install Cisco Small Business or Sonicwall for those who insist on it, or don't want to pay for Meraki, but they won't be my first-line recommendations anymore.
I know full well I just dropped the jaws of many from the collective "old guard" as I call them. The IT folks who believe a real firewall doesn't deserve any kind of GUI beyond a command prompt. The ones who believe scripting changes over CLI is the only real way to administer network security devices. I probably won't change some of their minds, but then again, that's not who this review is targeted at.
I'm here to speak to the average IT person, or even the DIY business owner, who merely want enterprise class security without the cr*p that comes with usual Cisco or Sonicwall fare.
There is a large majority of IT pros out there who have zero interest in cornering their careers into merely learning the nuances of Cisco command line so they can install and manage Cisco ASAs and related devices. I don't blame them -- I've refused to go down the Cisco path for that very reason. If this were the year 2000, then that would have been a career suicide for a true networking professional.
But luckily, it's 2015, and network security as a whole has grown up, matured, and become more accessible as a whole. Competition is fierce and Cisco isn't the only kid on the block anymore.
Where MX Firewalls Really Shine
Our own company office in Park Ridge has been running on a Meraki MX60 device for slightly less than a year now. And the capabilities of the unit far outstrip anything we used to have on our former RV320 box from Cisco.
In fact, it's a night and day difference. We've been able to increase security, uptime, performance, and management in what seems to be a near tenfold increase. Things that were either buggy or unavailable before are now consistently operating as advertised. What does Meraki's magic juice look like in real life? Glad you asked.
Take, for example, something simple like proper logging. Some devices do it better than others. Our old RV320, for instance, was kind of pathetic. Logging was not turned on by default, and even when it was, there was no clear and common way to search for items like site to site VPN disconnect line items to troubleshoot connectivity issues in this realm. Tracking down problems of this nature was a downright nightmare in my experience.
Meraki's cloud dashboard for my MX60 not only allows me to view detailed historical logs for innumerable events like client DHCP leases, VPN issues, and security occurrences, but I can further filter down by event category, by timespan, and even by specific client device. Any filtered log can be exported in CSV and further manipulated and extrapolated for reporting or analysis purposes. Since Meraki's devices aren't limited by the memory inside the appliances, logging is extremely detailed and can be stored for far greater periods of time.
Another relatively basic feature, but very useful one in my eyes, is the Appliance Status page that every MX series device has available to it via the cloud control panel. This is the most informative "single pane of glass" within the MX area of the cloud dashboard since it displays numerous pieces of juicy info at a glance, including but not limited to:
- Network traffic and internet traffic passing through the device, in dynamically adjusting line chart format that refreshes every few seconds. Useful for seeing if a particular WAN pipe is taking load and how much overall strain is being placed on the firewall.
- Firewall connectivity history that allows you to see at a glance if there are any internet outages occurring; if so, what times they are happening and how long they last.
- Public IP addresses for all internet WAN ports at any given time; very useful for establishing site to site VPNs between branch offices that may not have the luxury of being on Meraki firewalls yet.
- Firmware update status for any firewall device, with a single-click link to force a firmware update on the fly to that given firewall on demand.
- Network connectivity and performance tools including firewall-facing ping, traceroute, DNS, and throughput tests which can quickly diagnose growing network problems right from the web dashboard.
- Reboot capability for any MX firewall; yes, no need to pull any power cords here. As long as the MX has internet, you can force a reboot with a single click anywhere in the world.
Another feature which I just love on the MX series devices is the deep functionality afforded in terms of addressing, DHCP, and VLANs. For example, the firewall can run a DHCP server for a number of address scopes, all with their own reserved static ranges and DHCP reservations. VLAN configs can be tied on a per-port basis, and also tagged onto different SSID signals for networks that either have WiFI capable firewalls (MX60W, MX64W, or Z1) or contain standalone WAPs like our go-to Meraki MR18.
Firewall features on the MX line are also very rich, allowing for easy web-based administration of port forwarding rules, Layer 3 outbound rules, as well as 1:1 NAT and 1:Many NAT rules. If your MX firewall has a cellular failover 3G/4G USB slot, you also have access to specific firewall settings that apply only to these connections -- useful if your organization has specific requirements for when sudden emergency scenarios on cellular arise.
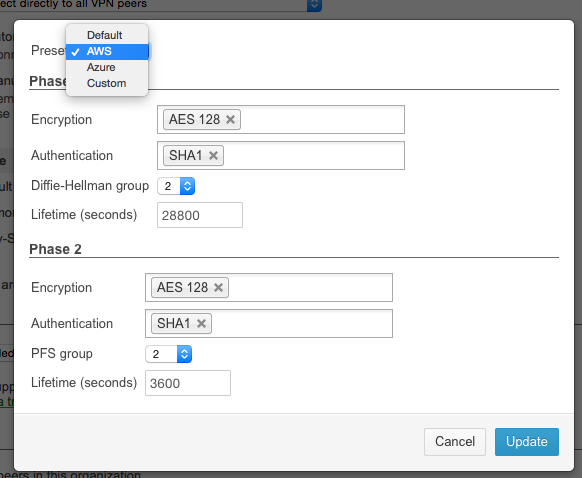
Putting virtual server workloads into Microsoft Azure or Amazon AWS? Site to Site tunnels between your on-prem network and these cloud giants is now easier than on any other firewall. Meraki has provided pre-configured dropdown settings for each of these providers' VNETs, enabling for wickedly easy tunnel creation. (Image Source: Meraki Blog)
One of Meraki's big selling points behind the MX firewalls is a capability exclusive to their devices (as far as I know) that is patent-pending called AutoVPN. The primary purpose behind AutoVPN is to simplify the VPN tunnel creation process between branch office firewalls. More succinctly, to make the process a zero-configuration-needed procedure.
Let's put this into a real world example I see often. Perhaps your company has a main office, two branches, and a few remote work-from-home users that telecommute every day. All of these endpoints need constant inter-connectivity over VPN so that branches and telecommuters can reach corporate resources easily. The way this used to be done was over devices like ASAs and soft clients such as Cisco AnyConnect -- a convoluted mess of hardware site to site VPN and client VPN using cludgy software.
Meraki's approach with AutoVPN is far cleaner, and easier to setup and maintain. As long as all endpoint locations are on MX devices (perhaps MX64's at the offices, and Z1 firewalls at the telecommuter homes) you can enable AutoVPN which a single click, and select which networks are part of the overall VPN chain. Networks can be tied in, or removed, with a single dropdown menu on the web, and tunnels are established between locations near instantly.
All of the above, mind you, can work with or without static IPs. While using static IPs is still considered best practice, home users without the ability to obtain statics don't need to be relegated to using soft clients like AnyConnect. A sub-$200 firewall like the Z1 can be used at home (which is what I have at my home condo) and tied into participate in the AutoVPN chain with no effort. This is because Meraki has built-in dynamic DNS hostname service that comes free of charge as part of your MX license.
No need to pay for separate DynDNS here, as was usually the case in these scenarios. A small savings, but a nice touch that just shows how serious Meraki is at making the MX experience a truly end to end offering.
For scenarios where client VPN is a requirement, such as when users cannot travel with a Z1 in hand, Meraki allows you to use license-free capability that tied into the native L2TP VPN connectivity that comes built right into Windows and MAC OS X these days. As opposed to Cisco AnyConnect or Sonicwall Global VPN software, which needs to be updated/configured/supported separately, native L2TP connections in Windows and MAC OS X are easy to setup and come with no extra software tentacles to deploy and maintain.
Client VPN connections on Meraki MX units can have authentication controlled in one of three ways. My foremost favorite, due to its ease of use, is leveraging the Meraki cloud -- which allows you to make Meraki.com logins for users which is what ties to their client VPN access. The other options are RADIUS tie-in for those who already invested in such infrastructure, or even good old Windows Active Directory if you wish.
Fight Bandwidth Problems with Logic -- Not More Bandwidth
"I need a larger pipe. Period." That's the conclusion many business owners or network admins come to, and it's one that becomes a necessity for the wrong reasons. A big part of the problem that forces this conclusion is because most organizations don't have the equipment that can fight traffic problems with proper logic -- QoS, traffic shaping, etc -- and they end up resorting to merely buying bigger pipes.
While bigger pipes easily mask the problems at hand, they aren't long term solutions to underlying traffic issues on your company network. There will either come a point where you can no longer buy more bandwidth, or the economics of larger pipes will bring this band-aid solution to a halt.
Meraki's firewalls come with numerous tricks that can bring even the most strained pipes under control; either staving off bandwidth purchases either for the short-term, or in many cases, permanently.
Take a real world scenario we just helped a customer solve. A firm that is on a Comcast Coax connection of decently large size (75-80Mbps down, 10Mbps up) was having problems with a mere 8-10 office users on cloud hosted VoIP phones. Choppiness, dropped calls, "fishbowl effect", etc. Out of incessant frustration, they wanted to increase their pipe, and I put into motion an alternate plan that would save countless dollars over the long run.

The newest flagship firewall for small-office usage from Meraki is the MX64W, with support for about 50 active users, 200Mbps of firewall throughput, and full gigabit integrated switch with dual gigabit WAN connections. The best part about this new firewall is its built-in WiFi capabilities, which include dual-band concurrent 802.11G/N/AC at both 2.4 and 5GHz. For a unit at under $800USD (unlicensed) in the wild already, this is an absolute bargain for an AC-enabled WiFi firewall. (Image Source: Meraki)
We purchased an MX60W for the office to replace an aging low-end Asus router, and along with configuring proper QoS rules that the VoIP provider wanted to see, we also turned on Traffic Shaping policies that were able to control some of the "bandwidth hogs" that were plaguing the network.
We were able to set per-client limits for all devices on the network to a pre-determined maximum level of upstream and downstream bandwidth consumption, which immediately prevented streaming media and even some online gaming services from sucking up our pipeline. QoS rules for the VoIP service were also given highest priority for specified port ranges.
Within a week of installing the firewall and the traffic rules, call quality problems were a thing of the past. All users were able to use their laptops, desk phones, and mobile devices without any roadblocks, and call quality was where it should be. We fought the misconception that more pipeline is the only answer -- and were spot on.
I've implemented the same policies in our own office at FireLogic headquarters. Since we use an MR18 as our primary access point in addition to an MX60 firewall, we go a step further and actually throttle guest WiFi users to a much lower level of consumption than my internal staff are allowed over our private WiFI SSID. Wired clients are given even higher limits, primarily because we are always finding ourselves downloading swathes of Windows Updates for client machines, which can otherwise take hours with policies that are too strict.
In addition to traffic shaping and QoS policies, we have dual WAN pipes that consist of a Comcast Coax line and a small ATT DSL backup line. We have our two internet lines configured in link aggregation mode, which is Meraki's codeword for what many call "load balancing" and active failover.
We can select a primary uplink line (Comcast, in our case) and yet still choose to have both lines working in a load balanced manner, with traffic flowing between both pipes depending on bandwidth rates that are manually specified for what each pipe can handle. The Meraki MX device simply passes traffic between both pipes based on calculations for how much load a line is taking at any given time per the up/down rates we have established.
In the event where our Comcast line goes out, for example, the ATT DSL line takes over in short order, with all traffic being passed over that pipe until Comcast comes back up. And of course, vice versa. This can cause some issues in some environments with particular software, especially in situations where you are internally hosting services. But traffic shaping rules can further allow you to specify which pipe should take all traffic for a specific function, like all VoIP calls or traffic related to an internal web server.
And for those with MX80 or larger firewalls from Meraki, they can take advantage of content caching, which can help reduce strain on smaller WAN pipes that have unusually large user counts. I have not used this in the field yet, but this would have come in handy at the former school district I worked in IT for, where we had growing numbers of computing users and an internet line which didn't grow at the same pace to keep up.
The Dashboard Concept & Licensing
Diving into the world of Meraki cloud networking requires a basic understanding of how devices are managed and overseen. Any Meraki equipment you may place into your growing network is controlled under a single pane of glass known as a Dashboard, which provides control over firewalls, access points, switches, and even MDM-enabled devices.
To put into simple terms, the world of Meraki views network device control in the following top down manner:
- All devices under your company's control will be placed into a common Dashboard. Since FireLogic is an MSP that manages numerous customers, we have many Dashboards we can flip between in a single click.
- A Dashboard can contain one or more Networks. A network is usually considered as a single office location on a common IP range (or several ranges) behind a given WAN pipe(s). Headquarters would be a Network; a branch is its own Network; and a home office would another Network.
- A Network then contains any number or mixture of devices such as a firewall, switches, access points, etc. A network as defined and managed by Meraki's cloud controller is limited to Meraki-branded devices only. If you have a Meraki firewall and Ruckus access points, you will NOT be able to manage the third party devices in Meraki's dashboard.
Once you have an understanding of how the world of Meraki functions, expanding your networks and tying in branches with AutoVPN becomes a natural concept.
The Dashboard for your organization is the place where you can manage all of your inventory of devices and matching licensing for your gear. Which brings me to another topic that you should know about: licensing.
Any gear that is Meraki-branded requires a working, legit license activated in your Meraki dashboard to function. This is no different than what nearly every other business grade firewall maker requires. Cisco's first party ASA gear has nasty licensing guidelines in my opinion, which dictates functions separately from support, to user counts that are supported per-device, and down to number of client VPN connections allowed.
It's such an old-style model of licensing which irks me a lot, which is why Meraki's approach is far more appealing. For their firewalls, for example, the licensing model is dirt simple. You pick between either Enterprise licensing or Advanced Security licensing, the latter of which merely enables a few extra features (malware filtering and IPS/IDS being the big ones) and then choose what kind of timespan you wish to license for.
You can go for as little as one year, all the way up to 10 years on some licenses. I find 10 years to be obnoxiously long, as no one can guarantee to be using the same box that far out, and do keep in mind that Meraki licensing CANNOT be transferred between parties. So DON'T over license your devices in the hopes of making that money back down the road. Meraki, as far as I know, will NOT allow the licenses to transfer between owners.
I usually license client Meraki devices for between 1-7 years, with 7 years usually being relegated for Z1 boxes which we are installing in home settings as routers. It is fair to assume that a home will use a router for that long, especially with the extremely high build quality of the Meraki devices.
What does an Enterprise license entitle you to? Quite a few things actually:
- 24/7 telephone support. During most hours of the day, aside from after-hours, this equates to US-based network engineer support. Wait times are in the 2-4 minute timeframe even during peak times, and these guys KNOW THEIR STUFF. I've had terrible experiences with Cisco Small Business and Sonicwall support, but *knock on wood* every call with Meraki support has been pleasant and resolved my issues in short order. None of that level 1, level 2 crud you deal with at most other companies -- the first person to pick up your call is the one solving your issue 99%+ of the time.
- Next day warranty replacement. For as long as you are licensed, Meraki is on the hook for shipping you a next day replacement device in the case your unit fails. None of that upcharged advanced replacement that is common among the other vendors. You get the fastest shipping without asking or paying more.
- Cloud management console. Yes, this is the Meraki "juice" that separates Meraki from everyone else. They host the console, they update it, manage authentication and accounts -- easy and simple.
- Consistent, automated firmware updates. The most out of date your firewall can become is, at most, one version old from what I can tell. Every Meraki device is placed onto an automated update schedule which you can fully configure -- or best yet, just force to update immediately when new releases come out. Stable firmware comes out about 1-3 times per month or so per device, adding in new features and fixing bugs alike. There is a beta channel you can jump onto with a simple selection if you wish to stay "bleeding edge" with your gear.
For those who want the whole nine yards, Meraki offers a higher level Advanced Security License that opens up malware filtering at the WAN pipe level, intrusion prevention and detection, search filtering, and content filtering along with a few other minor items.
We use this higher license at our office for the added security benefits, which play a large part into our need to stay HIPAA compliant internally.
Meeting HIPAA Compliance With Meraki Firewalls
Since our company is considered a downstream provider of IT services for medical offices, HIPAA compliance is a real big deal to us. We're officially Business Associates (BA) to numerous customers since we help maintain and support their own technical infrastructures as a managed services provider (MSP). As such, our own internal infrastructure needs to meet the highest levels of security and upkeep.
I've written about HIPAA IT compliance and its myths in the past, and judging by how much email I get about the topic, many IT pros are still very wary on the subject. But when it comes to securing your internal company network, one of the easiest ways to meet and preserve HIPAA compliance is by going Meraki. Here's why.
HIPAA asks covered entities (CE) and business associates (BA) to maintain strict role-based access to all core network infrastructure, with permissions being disabled as soon as staff leave positions that formerly required access to core gear. We can manage this with a single interface on Meraki's Dashboard, since access into any number of Networks tied to your Dashboard are controlled via a common interface for admins. If you fire a staff member, you can remove their access to your entire Meraki dashboard and all of the associated gear in one action.
HIPAA also has regulations surrounding maintaining proper uptime to systems that support and server data, especially ePHI (electronic patient health info). For covered entities (CE) like medical offices, this means sustaining internet uptime even when single pipelines fail since must or most of what is done these days relies on internet access. I already described how we use dual internet line at our office above; this same scenario is applied at customer sites that are under HIPAA guidelines. Meraki helps ensure stability and uptime with dual WAN pipes that are consistently being monitored.
When it comes to the security of the traffic coming to and leaving your network, this is where Meraki's Advanced Security license fits in. You can easily enable malware filtering (which gets updates once an hour) and intrusion detection/prevention for ensuring hackers aren't prying into your network. I know many other firewall brands offer similar functions these days. But Meraki's ease of enablement through a single license, and the excellent reporting capabilities on malware detections, intrusion detections, etc is paramount here.
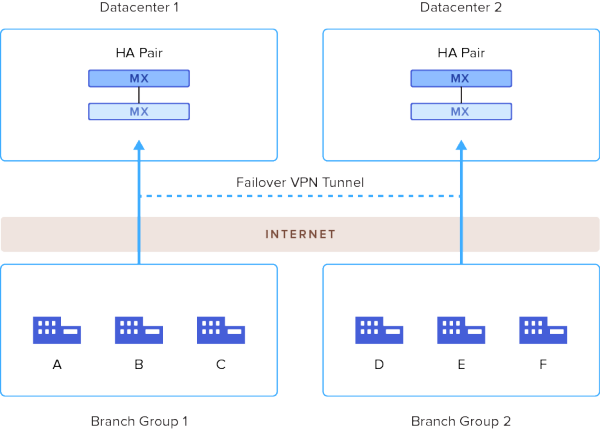
Even though Meraki's firewalls are very reliable in my real-world experience so far, there are use cases where extremely high uptime is required. As such, Meraki supports High Availability (HA) for MX hardware now so mission critical 24/7 scenarios like hospitals and production facilities can stay live at all times even in the face of firewall failure. (Image Source: Meraki)
A dual-protection approach we commonly use, therefore, is malware and IDP/IPS on the Meraki level, and then also place ESET Endpoint Antivirus on servers and workstations. This winning combo has yet to allow anything nasty, like crypto locker, onto systems we support. Never say never, but being proactively smart is really the bulk of what HIPAA guidelines are looking for.
Finally, in situations where WiFi is being used in HIPAA environments, we are able to not only offer SSID separation, but VLAN security for guest WiFI as well as subnet controls to completely isolate visitor traffic. All of these practices in unison ensure a 100% HIPAA compliant wireless network deployment that meets internal staff needs, but also allows waiting room guests to play on their smartphones and tablets in a secure fashion.
On top of the security benefits we get from SSID separation, we can also apply per-SSID traffic shaping to ensure that no visits come and suck down torrents on their laptops, for example. Everyone is forced to play fair so that normal office private traffic is given full priority to the bandwidth of even the smallest WAN pipes.
Will a Meraki device alone fix your HIPAA compliance ills? Absolutely not. But it's a great start for HIPAA covered entities or BAs where units like Linksys or DLINK routers are in place, potentially violating HIPAA regulations for the numerous reasons I listed above.
Meraki Z1: The Best Home Router You Never Knew About
I'm sure Meraki won't like me saying this publicly -- or perhaps they will, I'm not entirely sure. Regardless of how they intended the Z1 to be used (as a "teleworker gateway" to be exact), I'm going on the record and saying that this is by far the best sub-$200 firewall you can get for the home. Period. End of story.
Why do I say this? Well, for starters, the device comes with all the usual Meraki "juice" I've described above when it comes to the dashboard, 24/7 support, and next day replacement. You get the usual firmware updates which are automated and seem to follow the same schedule as the MX line of devices.
And something the old MX60W box didn't have (which cost more than twice as much, mind you) is dual band concurrent Wi-Fi on both 2.4 and 5GHz spectrums. It's only B/G/N, so no AC like the new MX64W, but again, at sub $200 with multi year licensing attached, this is an absolute bargain of a home router.
Manual firmware updates for your router are so 2004. With Meraki, you can easily set an update schedule for when firmware pushes happen, and even go on their Beta release channel. Or, if you're like me and want to force updates immediately, that's possible too. The days of running antiquated firmware are over. (Image Source: Meraki)
In fact, we've installed about 4-5 already for residential customer homes, and I've even put one in my own home condo, and at my parents home. The WiFi coverage is above average (doesn't touch what an MR18 access point from them can do) and can support as many devices as one can throw at it in a usual home setting.
The Z1 doesn't allow for any integrated malware filtering or IDS/IPS, as could be assumed, and it also foregoes the dual gigabit WAN ports of the MX60 and higher devices. It still keeps the 4 port gigabit LAN switch, and also tosses in a USB slot of 3G/4G failover. Useful for some, but I just don't depend on cellular failover in any way -- yet.
One lacking item that no Meraki firewalls can do yet is UPnP, which is critical for using gaming consoles like my Xbox 360 without the need to do DHCP reservations and port forwards for Xbox Live and such. Not a big deal, however, as my old router needed the same, but it would be nice if Meraki introduced UPnP at least on the Z1 boxes.
Until a competing device comes onto the market, Meraki or not, that offers the features and WiFi capability of the Z1, this IS my go-to device for high end home router needs. It can't be touched from a price/feature/performance mix standpoint. If it had external antennas like the MX60W/MX64W, it would be an absolute perfect 10, but it's a solid 9.5 where it stands right now.
My favorite aspect? When my parents call about internet problems, I can pinpoint whether it's the ISP or home network in a matter of seconds with no visit required. That's a keeper in my book.
Where Meraki Can Improve
Meraki, while a great company with some of the best firewalls I've put my hands on, has its faults. And I'm not afraid to shed light on them, as I feel they need to be addressed for this company to rise up in mindshare among the IT community.
One item that is causing consistent pain for my customers and their networks is a lack of complete visibility on non-Meraki based site to site VPN connections. In essence, VPN tunnels between Meraki boxes and other endpoints (like Cisco ASAs, Sonicwalls, etc). While Meraki does an awesome job of showing status, insight, and uptime for all Meraki peers, there is next to zero insight provided on these third party peer connections.
It should be noted that while you as a customer cannot look into individual tunnel status for your third party S2S connections, Meraki support interestingly can. I've been on countless support calls with their reps who had fantastic knowledge of what was going on with these tunnels and provided the expertise needed to solve issues, but this needs to change. Meraki cannot assume that all of its customers will be using solely Meraki MX/Z1 firewalls on all ends, especially when it comes to networks they have no control over -- like Azure or AWS in the cloud.
Another VPN related downside that surprisingly exists, which I recently uncovered, is that VPN tunnels between Meraki or non-Meraki boxes that require the use of a hostname (EXCEPT for Meraki peers in the same dashboard) cannot be established. A perfect example of this is between two Meraki boxes on different dashboards, which we had come up recently for sister companies that didn't want to share a single dashboard and didn't have static IPs at each office. Seeing as Meraki offers integrated hostname service for all firewall devices, this is silly that this technology cannot be used across dashboards.

The Z1, Meraki's cheapest firewall, is a sleek, all-gigabit, dual band concurrent 2.4/5GHz B/G/N device that is hands down one of the best home routers sub-$200 can buy. We use it at very small offices as well, but the bang for the buck this unit offers for residential customers is a much better value than any Asus or Linksys unit at similar price points. Sorry, Meraki, for letting this secret out of the hat! (Image Source: Meraki)
A small, but annoying, settings limitation also exists which only Meraki support staff can adjust. It relates to being able to control whether WiFi signals on devices like the MX60W or Z1 are allowed to use AES or TKIP for WPA2 encryption. By default, I believe these devices use mixed mode, but heavy Apple shops are notorious for having issues with mixed mode we have found. Forcing AES is the answer, but again, you cannot control this from your own dashboard without calling in for support. A small, but time saving, option that could be easily implemented into the dash.
My next qualm relates to how the Meraki purchasing process works. It's ridiculously rigid and old-school in my opinion. In all honesty, it represents completely the opposite of the ease of use that Meraki represents compared to its Cisco first-party cousins. All gear from Meraki seems to be stocked centrally in California and as such, has to be shipped from there, with expedited shipping for anything needed within a few day timespan. Since we are in Illinois, ground shipping for their devices rarely reaches us in a single work week.
Right now, there is no way for us as an MSP to stock or keep Meraki gear on hand for customer emergencies. A Sonicwall goes out and a client wants to move to a Meraki MX60 or Z1? Sorry -- unless they want to pay for rush shipping, there is no absolutely no way we can procure items locally, even from giants like Ingram Micro or CDW that we routinely do Will Call with. This is by far one of the biggest complaints we have for otherwise awesome gear. It just doesn't make sense why Meraki can't stock their gear across the USA, so we aren't forced to choose next day air shipping or just going with another vendor in an emergency.
Seeing as all of the licensing for Meraki gear is separated from the hardware anyway, this stocking problem Meraki has is even more problematic and irritating. This isn't an issue in deployments where we have time to procure items weeks ahead, but rush orders for emergencies are an unnecessarily difficult discussion with customers that are used to us obtaining gear from CDW or Ingram Micro locally in complete binds.
As a Meraki partner, one item that is also sorely lacking from Meraki is proper training and certification programs for their equipment, especially the kind that their parent company Cisco affords its first party gear. The amount of power and capabilities afforded to Meraki gear is large and diverse, and merely learning the platform as an experienced IT pro took me a good 3-4 months -- and that was real world experience, not sandboxed self-training in any way. Meraki needs to rethink how it handles partner training efforts so that everyone doesn't have to bootstrap their learning of the gear how we had to.
One last item, which I briefly touched on earlier, was the lack of ability to resell Meraki gear with licensing that can travel between owners. I know some other firewall brands allow this, but Meraki's gear doesn't, which is another painful future discussion I may need to have with someone that, for example, buys an MX64 with a ten year license and then decides to move to an MX80. The fact that licensing starts and ends with one customer is a short sighted decision that Meraki should seriously consider changing to stem any remorseful afterthought from companies that went all-in with their gear.
The Future of Networking is Cloud Managed, and It Simply Rocks
The old adage you've heard time and again rings ever so true for Meraki's gear. Once you try it, you'll never go back to the old way of installing and managing your network. Turning the notion of isolated firewalls that must be independently updated, managed, and configured on its head is quite refreshing.
As a managed services provider, we've taken a disparate array of firewalls used across customer sites and centralized onto Meraki units that come with varying degrees of functionality, but most importantly, a common concept of cloud-based management that is applied across the board. If you can learn how to manage a single Z1, you already know 85% of what it takes to manage MX firewalls, MR access points, and even the Meraki switch line (which I admittedly don't have much experience with yet).
This consolidation of efforts on our end to streamline our customer network firewalls onto Meraki units has not only allowed for considerable ease of administration, but also much higher levels of overall security, uptime, and overall network stability. Its the recipe for success that any customer wishes for their network operations.
Is Meraki gear for everyone? I would love to say yes, but I know many Cisco CLI diehards would never be caught dead in front of a GUI. But unless you have some deep rooted objections to GUI based administration, Meraki is absolutely worth a second or third look.
After being initially highly skeptical of Meraki's claims on cloud-managed networking, I'm now a full believer. I've put my money where my mouth is and fully deployed not only our entire office backbone on a Meraki MX60 and MR18, but also changed my own home network (and parents) over to a Z1 and couldn't be happier.
Those who said enterprise-level security and ease of use couldn't go together in a single sentence, have finally been proven completely wrong. Networking nirvana does exist, and for me, it's on an island called Meraki.