How to cope with Stagefright

Earlier this week we reported on the Stagefright vulnerability that could affect 95 percent of Android devices. It has arisen as a result of code vulnerabilities which could have been detected and resolved earlier.
Application security company Checkmarx has been looking more deeply into Stagefright and what it means for users and developers.
Stagefright can infect a device by simply downloading an MMS message -- which happens automatically in most cases. Once infected, the hacker has full control over the phone's data. The scary thing is that the Android device just needs to receive an MMS message. The user doesn't have to open it in order to get infected.
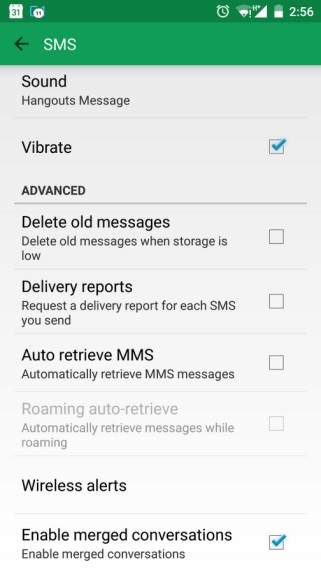
First of all there's a temporary workaround to avoid infection. Open the Hangouts app, go to Settings from the hamburger menu, select SMS, choose Hangouts as your default SMS app and uncheck Auto-retrieve MMS. There's usually an option to turn off auto retrieval of MMS in other messaging apps too, so check your settings.
Google was notified about the vulnerability and the numerous bugs quite a while ago and after a couple of days introduced a fix to the software. That, however, doesn’t mean everyone is safe. It means that all the different mobile-phone makers need to implement the fix in their versions of the Android OS and distribute a patch to their users. This may take some time, however most mobile phone companies have already stated that they are working on it while others have announced availability of a patch or have already addressed the issue when it was reported to Google.
Amit Ashbel of Checkmarx writing on the company's blog says, "It is clear by now that the Stagefright vulnerability was a result of one or more code vulnerabilities. It is also clear that these could have been detected at an earlier stage of the development and resolved at that stage. What is not yet clear is what the exact vulnerability is however that should become clear within the coming days after the full information about the CVEs reported are disclosed".
Checkmarx's CxSAST for Mobile delivers code security analysis for Android, iOS and Windows applications. This helps eliminate code vulnerabilities during the coding process rather than waiting for them to appear at a later stage.
Image Credit: Christos Georghiou / Shutterstock