Scan running processes for malware with CrowdInspect
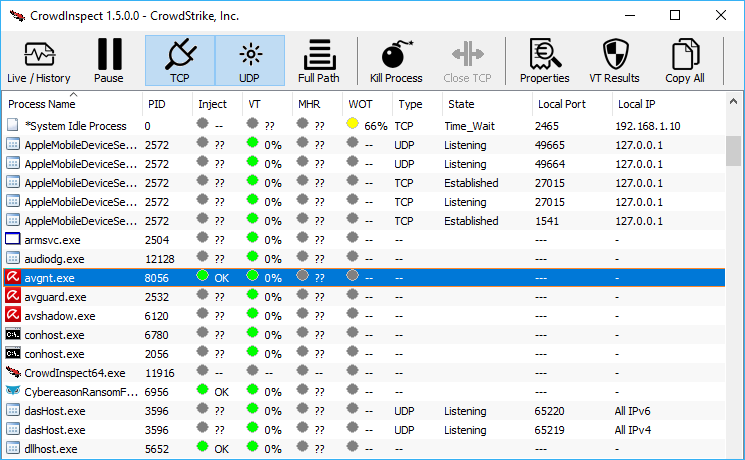
CrowdStrike has updated its Windows malware hunter CrowdInspect to version 1.5. The new version now scans all running processes for malware, not just those communicating over the network, quickly displaying a detailed report.
The most immediately useful feature is a column representing the VirusTotal score for each file. It’s color-coded to quickly highlight likely threats, and a right-click option provides a link to the full web report.
If a process has network connections open then CrowdInspect will list their type (TCP/ UDP), state, local and report ports, and local and remote IPs.
A "WOT" column displays the Web of Trust score for each remote IP. This might help you spot an unwanted connection even if it hasn’t been initiated by malware.
A "Live/ History" button toggles a history view which displays all internet connections for the time CrowdInspect has been running.
We’re less sure about the "Inject" column. This is supposed to warn you if code injection has been detected for a process, but we don’t know how reliable it is.
The program also checks the process file against the Malware Hash Registry, but this is an old service and no longer seems to do anything useful.
Do you need CrowdInspect? Process Explorer also gives you a VirusTotal report on running processes, and is far better for manual malware-hunting. But CrowdInspect is simpler, and the Web of Trust integration is a small plus. As it’s also tiny, portable and free, we’d recommend you grab a copy and check it out for yourself.
CrowdInspect is available for Windows XP and later.
