How millions of Android devices could be at risk of total takeover

Originally developed as a digital camera platform, Android has definitely come a long way. It just surpassed Windows to become the most popular operating system for Internet usage in the global digital realm.
This has been established through a report by StatCounter, which states that the global OS Internet usage market share of Android (37.93 percent) is 0.2 percentage points ahead of Windows (37.91 percent). You can check out the global operating system market share map, here. This is a huge win for Android, which accounted for a mere 2.4 percent of the worldwide Internet usage almost five years ago. Interestingly, Microsoft had been leading this market since 1980.
The reason behind this not-so-sudden hyper-popularity of the Android has been the advent of the smartphones on such a large scale. Usage of traditional PCs and computer sets has marginally declined since the larger segment of public started to buy these smartphones. Not to mention, Microsoft still rules the global desktop OS market.
However, the popularity of Android has also been met with parallel security threats, every now and then. This time around, the latest threat to brace Android devices is the probable hacking of your device through Wi-Fi signals.
In this post, we will comprehensively discuss how a proof of concept attack has put forward the possibility of millions of Android devices being at a complete risk of total takeover through nasty hackers.
The latest Android security threat
The latest threat has come into the light through the work of a Google’s Project Zero researcher, Gal Beniamini. The security issue is targeted on Android mobile devices which can be taken over through malicious Wi-Fi signals.
These attacks were introduced through Broadcom’s Wi-Fi chipsets used in many Android and iOS devices. Attackers can easily access these chipsets to allow the execution of their malicious code over Wi-Fi signals, without prompting the device user to take any action.
The issue was disclosed to Broadcom and, eventually, Apple was swift enough to release a patch to remove this security threat. However, affected Android users will still have to wait for this patch bundle, which will be apparently rolled out to select devices only.
It is advisable to not connect to public Wi-Fi hotspots to somewhat mitigate the risk. If the need is, one should employ VPNs (best VPNs for android are ExpressVPN & NordVPN) to secure their connection over a public Wi-Fi. However, this is just suggestive and as per the security reports, a previously hacked device might still be prone to data capture.
Why the threat exists?
Broadcom’s Wi-Fi SoCs are the most commonly used Wi-Fi chipset in the devices and this is the standalone reason as to why so many users are at the receiving end of this security risk where hackers can completely take over their device.
Generally, the chipsets rely on standalone complex layers; either the physical layer or the MAC layer. Since the use of Wi-Fi SoCs on mobile devices has seen so much market traction, chipset manufacturers are now putting up things together in a single chipset. The "FullMAC" Wi-Fi chipsets process all kind of layer management. This development was brought about to help the device’s operating system to function independently without having the need to process complex Wi-Fi features; hence imparting a better battery life to devices.
These FullMAC chipsets also brought about vulnerability along with the convenience they offer to the device’s OS. For the tech geeks reading this report, here is the hardware architecture behind the Wi-Fi chipset, as published by the researcher.
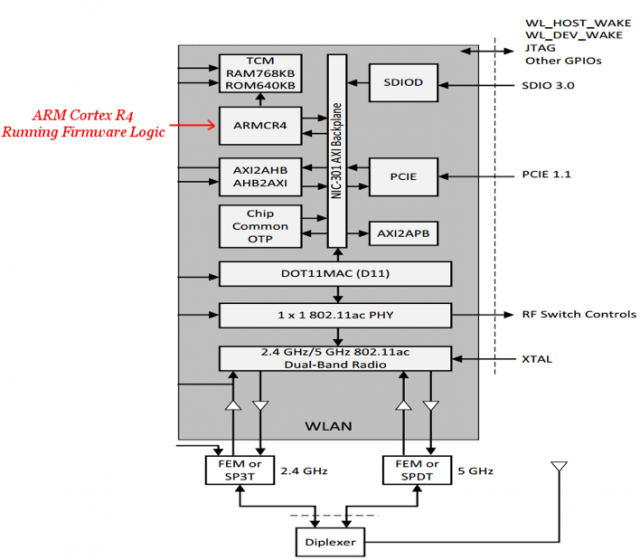
Gal Beniamini exploited Broadcom’s SOC Stack in a manner that it overflowed due to the introduction of irregular values used by him in the Wi-Fi frames. He then used arbitrary shellcode to overwrite some parts from the memory of the device. Beniamini thus stated that attackers can likewise access this entry point to enter the users’ devices and take complete control over them.
Beniamini’s proof-of-concept attack also explains how the lack of secure software and hardware platforms in the SOCs tempt attackers to seek action. After a little set up, these vulnerabilities are easy to exploit.
Towards the end of his detailed report, he says: "We’ve seen that while the firmware implementation on the Wi-Fi SoC is incredibly complex, it still lags behind in terms of security. Specifically, it lacks all basic exploit mitigations -- including stack cookies, safe unlinking and access permission protection (by means of a Memory Protection Unit)."
In this direction, Broadcom has planned newer versions of the chipsets that employ the Memory Protection Unit and implementation of exploit mitigations. Since the manufacturers are looking into this issue, we hope that the future versions will be more secure and pose minimum threats for the common users from around the world.
The two blog part detailed series by the researcher is still to roll out the second post where the exploit will further showcase the taking over on other operating system permissions. If you want to go through the complete exploit details furnished by the researcher, you can visit this link.
Since the security patch for Android devices will be initially rolled out to some major devices, this threat will continue to bother other device users who are not sure of receiving this bundle. However, the way Apple redressed this Wi-Fi threat bug is commendable.
 John Mason is an Internet privacy/security enthusiast. He's the head analyst at TheBestVPN and also writes content for TripWire.
John Mason is an Internet privacy/security enthusiast. He's the head analyst at TheBestVPN and also writes content for TripWire.
Photo credit: Alex Mit / Shutterstock
