The journey from Microsoft Security Bulletin to Security Update Guides

For decades, the Microsoft Security Bulletins have provided IT administrators with a monthly list of vulnerabilities and accompanying patches. Much to the chagrin of the IT community, these Bulletins have been replaced by the Security Update Guides portal (SUG), which many administrators believe will be a lot more work for them, especially for patch management professionals who already have enough on their plate.
Moreover, the additional time to research and understand the security patches required for their unique environments will only lengthen the time to patch. While the portal is searchable by Common Vulnerabilities and Exposures (CVE), Knowledge Base (KB) article, product or release date, the change in process will impact the daily routines of IT administrators and security professionals around the world.
Microsoft on the other hand, believes that SUG has the functionality that users have been asking for, and that the portal allows users to customize it for their unique needs. Regardless, the change has generated concern about the impact on patch management activities.
A major part of the outcry against Microsoft relates to changes that companies will have to make to their IT processes. Security Bulletins have been around for years, and administrators have built their processes around the predictable and consistent delivery of these Bulletins. Microsoft’s format changes are inconvenient for patch management professionals and may require more time spent on researching and identifying the security patches required for their unique environments.
The long and short of this development is that companies relying on Microsoft Security Bulletins that must now change their processes, and find alternative solutions to streamline and improve efficiency.
Old versus New
Here’s an example of this format change: a vulnerability in Adobe Flash Player, which Microsoft distributes to its users. The older format looked like this:

It is one security bulletin that could be read and IT administrators could quickly determine what Windows platforms and products were affected.
Now, using the SUG, the same vulnerability information is broken out into separate listings on the Website per platform. This same Adobe Flash Player vulnerability now looks like this:
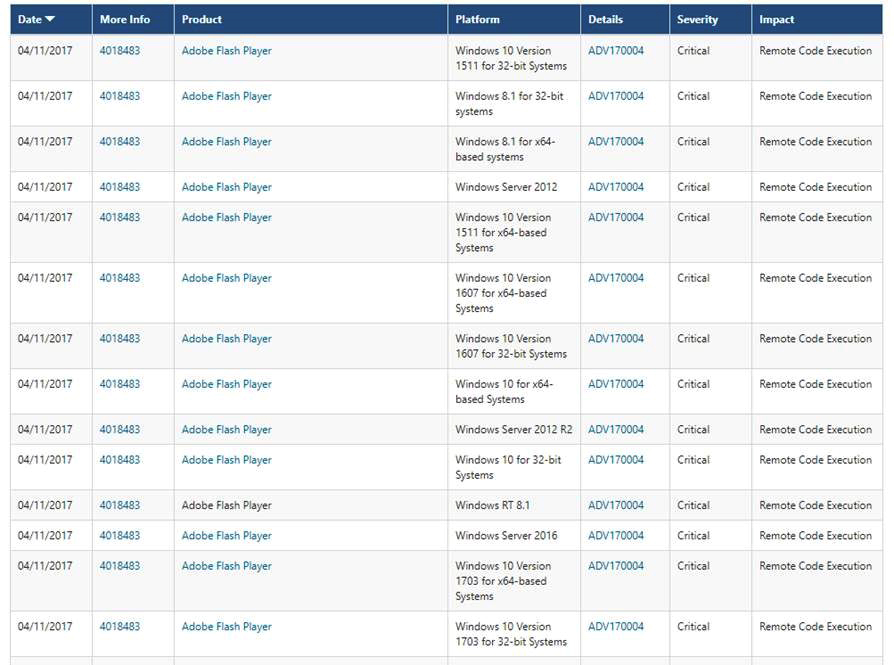 The good news is that despite the lack of Security Bulletins, vulnerability information from over a thousand sources -- including vendors like Microsoft and Adobe -- can still be pulled today. It is possible to consolidate all this information into an easy-to-understand advisory that shows all the products that are affected and the CVE references that are related, along with the vendor solution for the groups of vulnerabilities.
The good news is that despite the lack of Security Bulletins, vulnerability information from over a thousand sources -- including vendors like Microsoft and Adobe -- can still be pulled today. It is possible to consolidate all this information into an easy-to-understand advisory that shows all the products that are affected and the CVE references that are related, along with the vendor solution for the groups of vulnerabilities.
Vulnerability Ratings
The criticality of a vulnerability is based on the assessment of the vulnerability’s potential impact on a system, the attack vector, mitigating factors and if an exploit exists for the vulnerability and is being actively exploited prior to the release of a patch. The vulnerability ratings follow:
- Extremely Critical (5 of 5): Typically used for remotely exploitable vulnerabilities that can lead to system compromise. Successful exploitation does not usually require any interaction and exploits are in the wild. These vulnerabilities can exist in services like FTP, HTTP and SMTP or in certain client systems like email applications or browsers.
- Highly Critical (4 of 5): Normally used for remotely exploitable vulnerabilities that can lead to system compromise. Successful exploitation does not typically require any interaction, but there are no known exploits available at the time of disclosure. Such vulnerabilities can exist in services like FTP, HTTP and SMTP or in client systems like email applications or browsers.
- Moderately Critical (3 of 5): This rating is also used for vulnerabilities allowing system compromise on LANs in services like SMB, RPC, NFS, LPD and similar services that are not intended for use over the Internet. Usually used for remotely exploitable Denial of Service (DoS) vulnerabilities against services like FTP, HTTP and SMTP, and for vulnerabilities that permit system compromises but require user interaction.
- Less Critical (2 of 5): Usually used for cross-site scripting and privilege escalation vulnerabilities. This rating is also used for vulnerabilities allowing exposure of sensitive data to local users.
- Not Critical (1 of 5): Typically used for very limited privilege escalation vulnerabilities and locally exploitable DoS vulnerabilities. This rating is also used for non-sensitive system information disclosure vulnerabilities (e.g. remote disclosure of installation path of applications).
Considerations Beyond Criticality Ratings
Additionally, IT administrators also need to consider the following:
- Impact -- what the vulnerability can affect (System Access, DoS, Release of Sensitive Information, etc.)
- Where -- from where the vulnerability can be exploited: Local System, Local Network or Remote (outside of network)
- Solution Status -- is there a patch or other method that migrates the vulnerability?
- CVE references -- uses of industry standard CVE to aid in communication across groups
- Products affected -- can show if the advisory is for one product or multiple ones (in this case, the vulnerabilities affect multiple operating system versions)
- Advisory details -- summary of the issue
- Solution details -- how the vulnerability can be mitigated
There’s No Need to Panic!
Yes, Microsoft used to publish the Security Bulletins, which helped IT professionals understand patches that closed multiple vulnerabilities, patches closing vulnerabilities affecting multiple products, and so on. While many businesses are concerned about Microsoft changing the way they release vulnerability information around their products to the world, the thing to bear in mind is that there are solutions available today that achieve a similar view -- more than making up for the lack of Security Bulletins. All is not lost! Perhaps the panic has risen from many years of habit of doing patch management a certain way. Thankfully, the options available today are equally suitable.
Image credit: Goran Bogicevic / Shutterstock
 Ken Hilker is Senior Product Manager, Flexera Software. Ken has more than 15 years of experience helping developers and IT administrators create, manage, and deploy software installations, updates, and security patches.
Ken Hilker is Senior Product Manager, Flexera Software. Ken has more than 15 years of experience helping developers and IT administrators create, manage, and deploy software installations, updates, and security patches.