Why employees should aim to fail in 2018

As children, most of us learned the hard way not to touch a hot stove. The instant searing pain and the lingering bite that followed and lasted for at least a couple days is the bitter reminder that we had messed up. But ask yourself, have you touched a hot stove since?
The lesson learned here still follows us throughout our lives because learning from failure is the quickest path to growth. The first time one falls for a phishing email is no different.
While companies are being targeted by hackers now more than ever, employees can greatly improve incident response efforts when they report real phishing attempts promptly in real-time.
Phishing defenses rely heavily on the users and their ability to spot and report potential phishing emails. The best way for users to learn what a phishing email looks like is to expose users to a learning environment where it is safe to fail, thereby empowering them to strengthen the overall security posture of their organization.
How does it work?
IT teams cannot just send random emails to their users to train them to spot phishing emails, rather the emails must look as close to the actual threat as possible. The idea of a phishing simulation program is to condition users to recognize and report suspicious emails, so the security team can examine them and, if they’re malicious, respond. Organizations that implement phishing simulation programs have a susceptibility rate as low as 5 percent according to recent research.
This "learn from failure" approach works in two ways. First, overtime organizations will see their overall phishing susceptibility decrease. Research demonstrates that companies using simulation training reduces their susceptibility rate year over year. Once a user clicks on a phishing email, the best approach is to provide materials that stress reporting while outlining the type of phishing email, the consequences that could have resulted if it had been a real threat, and what to look for in the future.
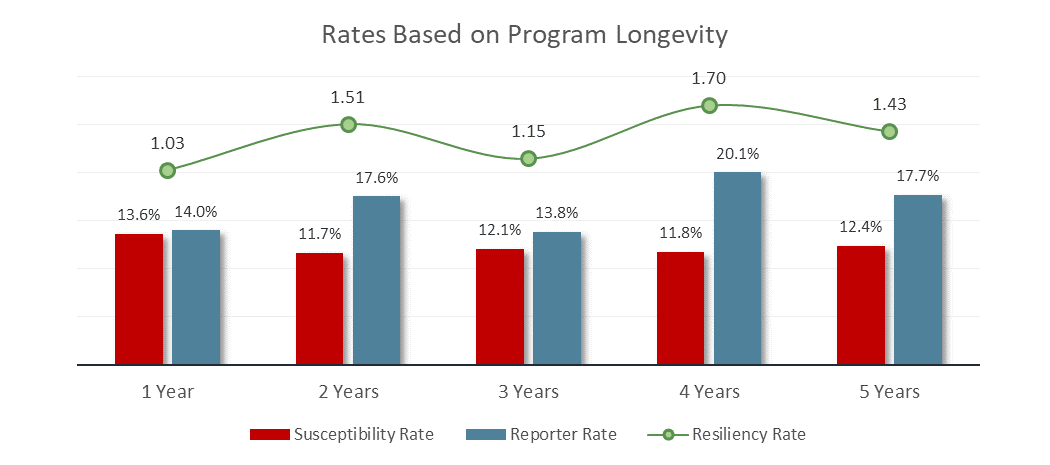
Source: PhishMe 2017 Enterprise Phishing Susceptibility and Resiliency Report
Secondly, organizations’ resiliency to all types of phishing attacks increases. Additional research indicates that 91 percent of cybersecurity attacks start with a phishing email, so it is crucial that employees be able to fail when there is a safety net to learn from their mistakes.
Similar to how threat actors can improve their cyber hacking skills over time, employees that are subjected to phishing emails improve their susceptibility rate. Research shows that employees that are challenged and kept up to date on the latest phishing tactics are less likely to fall for them.
The best way to go about continuing to improve susceptibility rates, beyond repeated exposure, is to up the ante on the difficulty to spot phishing emails. Once employees have mastered the basics, subjecting them to more complex phishing simulations will boost their ability to detect a phishing threats. Although tougher simulations may cause resiliency to dip, it rebounds over time as repetition sharpens learning.
Other ways for organizations to boost resiliency is by frequently launching simulations. The ideal frequency is 8 to 12 times per year. By exposing employees to the latest phishing threats regularly, organizations are instilling good cyber habits. Employees get into the habit of always being on the lookout and reporting possible threats, which allows their organizations to play on the offensive side of cybersecurity efforts.
Across Industries: Who’s at risk?
No matter the industry, every organization is at risk of being exposed to a real phishing threat. The good news is studies show that resiliency to phishing emails is improving across most industries. Organizations that have higher susceptibility rates, like education, are often impacted by lower cybersecurity budgets and BOYD programs. Unfortunately, according to a recent survey of IT professionals across industries, a mere 10 percent or less of IT budgets is spent on cybersecurity.
Driving Positive Change
Change won’t happen overnight, but change also won’t happen without positive feedback. It is important that employees don’t feel as though they’ve been tricked or berated in simulations. Security pros recommend that with every failed attempt, there be added encouragement that accompanies the correction.
In the end, organizations want to drive cultural change turning a weakness into a strength through individual growth. Organizations’ first line of defense is their staff so it is critical to take the time and spend the money to adequately train staff in detecting phishing threats.
Image Credit: wk1003mike / Shutterstockhis
 Lex Robinson has over 30 years of experience in information technology with a strong focus on strategic planning and program delivery. He is responsible for PhishMe Professional Services delivery strategy and provides hands-on program consulting, as well as customized results analysis and recommendations for clients seeking to reduce their organizations’ susceptibility to phishing attacks.Prior to PhishMe, Lex’s professional career has included consulting and management of product and service delivery teams for small businesses, global Fortune 20 organizations and Government Agencies.
Lex Robinson has over 30 years of experience in information technology with a strong focus on strategic planning and program delivery. He is responsible for PhishMe Professional Services delivery strategy and provides hands-on program consulting, as well as customized results analysis and recommendations for clients seeking to reduce their organizations’ susceptibility to phishing attacks.Prior to PhishMe, Lex’s professional career has included consulting and management of product and service delivery teams for small businesses, global Fortune 20 organizations and Government Agencies.