Sextortion is back and this time it looks personal

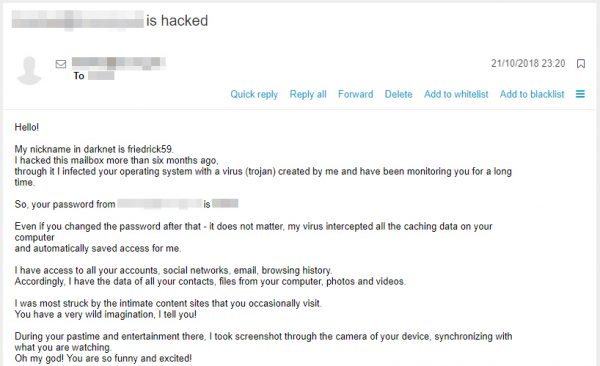
Over the last few weeks you may well have received an email that quotes an old password you once used. It tells you that your account has been hacked, that malware has been placed on your machine to capture data and that you’ve been recorded watching porn.
It then demands that you cough up some Bitcoin -- amounts vary -- to prevent this webcam video from being made public on your social networks.
It is, of course, a classic sextortion scam. There is no malware and no video, they just want to scare you into thinking there is in the hope that you'll pay anyway. The clever part here is that the hackers have used publicly available breach data to make the message look genuine by including a real-life old password.
Many of these passwords appear to date from the large scale LinkedIn breach of 2012 which, if nothing else, demonstrates that data has a long shelf life on the dark web. However, using data that's at least six years old does mean there's less chance of these details still being in use and consequently less chance of you falling for the scam.
Researchers at the Cisco Talos threat intelligence group have today released the results of their analysis of these attacks. One campaign began on August 30, and a second campaign began on October 5, both are still active. The researchers find that more than half of them originate from just five countries. Vietnam accounts for 15.9 percent, Russia 15.7 percent, India 8.5 percent, Indonesia 4.9 percent and Kazakhstan 4.7 percent.
Over 233,000 email messages have been sent as part of these campaigns, however, the number of unique recipients is fairly low. Talos has found only 15,826 distinct victim email addresses, meaning many people will have received multiple messages.
Talos has also identified 58,034 unique BTC wallet addresses associated with these spam campaigns. This works out to an average of more than three sextortion messages per BTC wallet. Only 78 wallets have positive balances, but they add up to a combined value of $143,429.38 which shows that at least some people are paying up. Had data from a more recent breach been used chances are that the cybercriminals behind the scam would have netted much more.
Some variants of the messages have used phone numbers rather than passwords as the convincer, but the basics of the campaign remain the same. Other variations include threatening to disclose supposed evidence of cheating on a partner, or offering to sell evidence of a partner cheating on you.
You can read more about the scams and how they work on the Talos blog.
Photo credit: Olena Zaskochenko / Shutterstock
