Formjacking is the new cash generator for cybercriminals

The latest Symantec Annual Threat Report reveals that cybercriminals are continuing to follow the money, but as ransomware and cryptojacking show falling returns they are turning to other techniques.
One of these is formjacking -- essentially virtual ATM skimming -- where cybercriminals inject malicious code into retailers' websites to steal shoppers' payment card details.
On average, more than 4,800 unique websites are compromised with formjacking code every month. Symantec has blocked more than 3.7 million formjacking attacks on endpoints in 2018, with nearly a third of all detections occurring during the busiest online shopping period of the year -- November and December.
While a number of well-known retailers' online payment websites, including Ticketmaster and British Airways, were compromised with formjacking code in recent months, Symantec's research reveals small and medium-size retailers are, by and large, the most widely compromised.
There's big money involved too. Just 10 credit cards stolen from each compromised website could result in a yield of up to $2.2 million each month, with a single credit card fetching up to $46 in the underground selling forums. With more than 380,000 credit cards stolen, the British Airways attack alone may have allowed criminals to net more than $16 million.
"Formjacking represents a serious threat for both businesses and consumers," says Greg Clark, CEO of Symantec. "Consumers have no way to know if they are visiting an infected online retailer without using a comprehensive security solution, leaving their valuable personal and financial information vulnerable to potentially devastating identity theft. For enterprises, the skyrocketing increase in formjacking reflects the growing risk of supply chain attacks, not to mention the reputational and liability risks businesses face when compromised."
Other findings from the report are that misconfigured cloud workloads or storage instances could cost a company millions of dollars or land it in a compliance nightmare. There are easily-accessible tools that allow attackers to identify misconfigured cloud resources on the internet.
It also reveals the rise of living-off-the-land (LotL) techniques that allow attackers to maintain a low profile and hide their activity in a mass of legitimate processes. For example, the use of malicious PowerShell scripts increased by 1,000 percent last year.
The Internet of Things continues to be a target, though the focus of attacks is changing. Although routers and connected cameras make up the largest percentage of infected devices (90 percent), almost every IoT device has been proven vulnerable, with everything from smart light bulbs to voice assistants creating additional entry points for attackers.
With the recent Cambridge Analytica data scandal and the Facebook data privacy hearings, plus the implementation of GDPR, privacy is in the spotlight too. According to Symantec 45 percent of the most popular Android apps and 25 percent of the most popular iOS apps request location tracking, 46 percent of popular Android apps and 24 percent of popular iOS apps request permission to access your device’s camera, and email addresses are shared with 44 percent of the top Android apps and 48 percent of the most popular iOS apps.
The full report with lots more detail is available from the Symantec site there's a summary of key findings in the infographic below and you can register for a webinar to discuss the findings to be held on March 28.
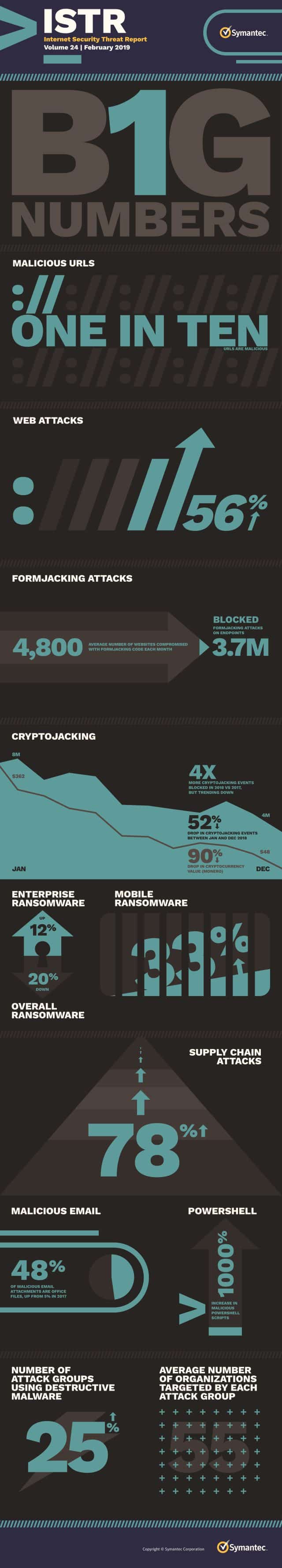
Image Credit: carlos_bcn / depositphotos.com