Cross-Site Request Forgery: How to protect your app from CSRF attacks

The rise of cyber-attacks in the last few years is stunning. The list of targeted organizations includes big name retailers like Macy’s, social sites like Twitter, banks, hospitals, utility companies, governments, military installations… no organization is exempt from this growing threat.
It’s a massive -- and expensive -- problem to fix. The cyber security market is predicted to grow from $150 billion in 2018 to $250 billion by 2023, to help protect apps and businesses from these risks. One of the most common, yet potentially highly dangerous, risks is known as Cross-Site Request Forgery or CSRF.
What is Cross-Site Request Forgery?
Cross-Site Request Forgery (sometimes called Sea Surfing or Session Riding) is an attack that aims to trick the user into clicking on a link that launches an unsafe or unwanted action on an authenticated website or app.
What’s the danger? A CSRF attack can be disastrous both the user and the organization being targeted. It can result in unauthorized actions for the user such as unwanted bank transfers or changed passwords and account info. It also exposes the company to further security risks, especially if the victim (the user) has administrative privileges on the app. And it adds massive risk to the company’s reputation if the breach becomes public or widespread.
Understanding how a CSRF attack occurs
A CSRF attack is typically executed with the help of social engineering -- say a message sent via email or social media -- that tricks the target into clicking on the link.
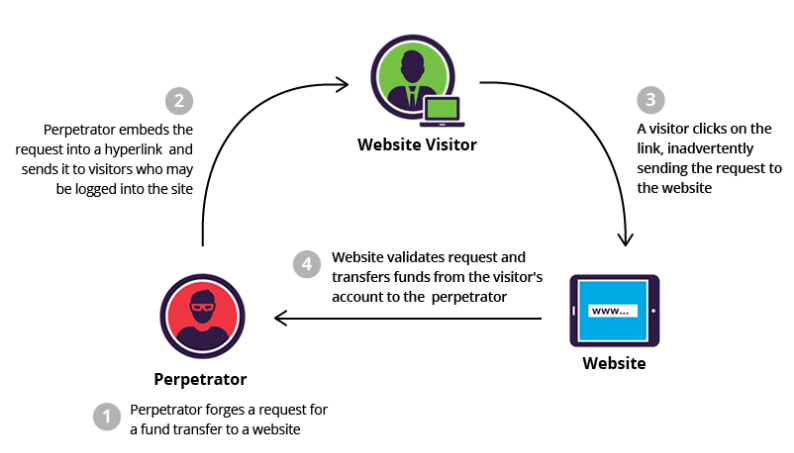
Image source: Imperva
First, the perpetrator creates a forged request to an action (for instance, transferring funds from a user’s bank account to their own) and embeds that request into a hyperlink that is sent to a user who is logged into that site.
The user gets a link from what looks like a familiar site, and clicks it. This sends the fraudulent request to the website, which authenticates and validates the request because it appears to be coming from the logged-in user. Thus, it is tricked into processing the forged request since the request was seemingly sent from the user’s browser with the correct authorization credentials.
Why CSRF Attacks are so Dangerous
What’s so insidious about CSRF is that the user is already logged on to the site or app, and the attack happens from his recognized computer and IP address. Because the request looks like it’s coming from a valid user, the web server can’t distinguish this forged request from legitimate, user-initiative requests. CSRFs exploit the trust that a website or app places in a user’s web browser; to the app, the user is authenticated and legitimate. And to the user, they are completely unaware of the request being made when they click on the link.
How to Defend against CSRF Attacks
As CSRFs grow in popularity, it’s imperative to apply preventive measures to protect your site and your users. Let’s explore the options.
Synchronizer Tokens
The most popular defense against CSRF is using a challenge token that is unique for a specific user and is commonly sent as a hidden value in all state-changing forms. This token is known as an Anti-CSRF Token or a Synchronizer Token.
The web server generates, stores and sends this token to the user as a hidden field in a request form. When a request is made by the user, the server compares the request token with the stored token and rejects the request in case of a mismatch. This stops the request in its tracks.
Same-Site Cookies
When requesting data from a site, the user’s browser sends any cookies they have on that site along with the request. So when the user is logged into your site, for example, their session cookie is sent along with their request to visit that page.
You can disable this behavior by applying the "SameSite" attribute for a cookie. It basically restricts sending the user’s session cookies to a third-party and potentially malicious website, effectively blocking the request from completing.
Cookie-to-Header Tokens
If the web app or site works using JavaScript, a same-origin policy proves useful. In this method, a cookie is set with a random token while initiating the user session. JavaScript on the client side reads this cookie and copies it to an HTTP header named "X-Csrf-Token" to make a request to the server. The server verifies its value against the original token and disregards the request if it finds a mismatch, since only same-origin code can access the cookie.
These techniques can all be useful, but they may not suffice to meet the security requirements of your app or site. In this case you may want to define custom security policies using a custom rules engine. For example, IncapRules from Imperva is a leading cloud custom rules engine that allows anyone to create and enforce custom rules for protecting sensitive functions and pages.
What is the Best Protection against CSRF?
Since the inception of digital communication, attackers are known to find and use any and all vulnerabilities to attack the system. The above preventive measures have some limitations if used alone, but combined, they form a solid layer of defense against CSRF attacks.
Of course, it’s not an easy task to deploy all these measures in your web app or site server. That’s why many companies are moving toward full-fledged security solutions that provide 360-degree protection against a multitude of attack vectors.
Solutions like Imperva’s FlexProtect plan offer a number of easy to deploy security tools that protect your web app or site against CSRFs. Its IncapRules custom rules engine and Web Application Firewall together provide multiple security measures such as CAPTCHAs to alert users, custom rules to protect sensitive content, and other protocol designed to stop CSRF in its tracks.
The risk is real, and the threat is growing. It’s imperative for apps and sites to protect their users -- and their own resources and reputation -- by instituting proven security protocols to keep the danger at bay.
Photo Credit: Profit_Image/Shutterstock
 Peter Davidson works as a senior business associate helping brands and start ups to make efficient business decisions and plan proper business strategies. He is a big gadget freak who loves to share his views on latest technologies and applications.
Peter Davidson works as a senior business associate helping brands and start ups to make efficient business decisions and plan proper business strategies. He is a big gadget freak who loves to share his views on latest technologies and applications.
