Netflix phishing tops all other attacks on streaming services

With nearly 151 million users worldwide, Netflix is the #1 streaming service in the world. It also has the distinction of being the most impersonated by hackers. For cybercriminals, Netflix phishing is a lucrative business. While other streaming services, including HBO NOW and Spotify, are also on the receiving end of phishing attacks, none comes close to Netflix.
Netflix’s 155 million subscriber base offers a lucrative supply of personal information, contributing to its favorability with phishers. In Vade Secure's quarterly Phisher’s Favorites report for Q2 2019, Netflix was the 4th most impersonated brand in phishing attacks, with 8.2 percent quarter-over-quarter growth in Q2 2019.
Some phishing campaigns are launched solely for the purpose of stealing personal data and selling it on the black market. Netflix accounts don’t fetch a high price -- around $1-$3 per account as of 2019. But when phishing emails are sent to the tens of thousands of subscribers in a single send, phishers stand to earn a decent payout.
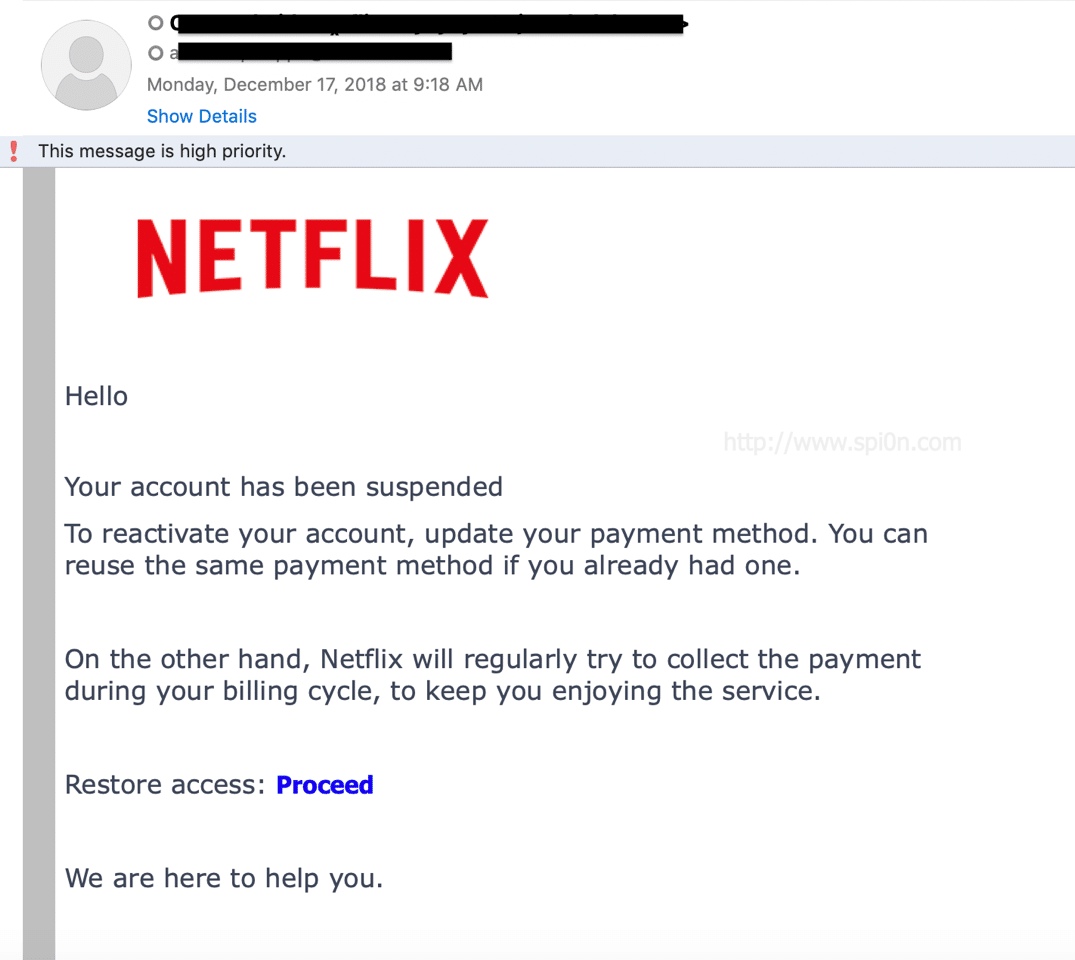
Netflix Phishing Email
While many hackers purchase black market Netflix accounts to access personally identifiable and credit card information, others do it simply to piggyback off the account, streaming movies and television shows for free like an ex who still has your password. You might not even notice until you start receiving out of character movie and television recommendations in your Netflix interface.
It’s easy to point to the subscriber count as the chief motivation for Netflix phishing, but there’s more to it. Phishing is a form of social engineering that relies on psychological manipulation to lure victims into divulging personal information. To manipulate a victim, a phisher needs to know what motivates them. When it comes to streaming subscribers, the answer isn’t hard to find.
How hackers lure streamers
Content is Netflix’s chief commodity. It’s what drives and retains subscribership. When Netflix adds new content, or when a new season of a popular show gets a release date, it’s big news. Over the course of the July 4th weekend in 2019, more than 41 million Netflix subscribers watched Stranger Things 3 -- and that doesn’t include subscribers who streamed on mobile and laptops.
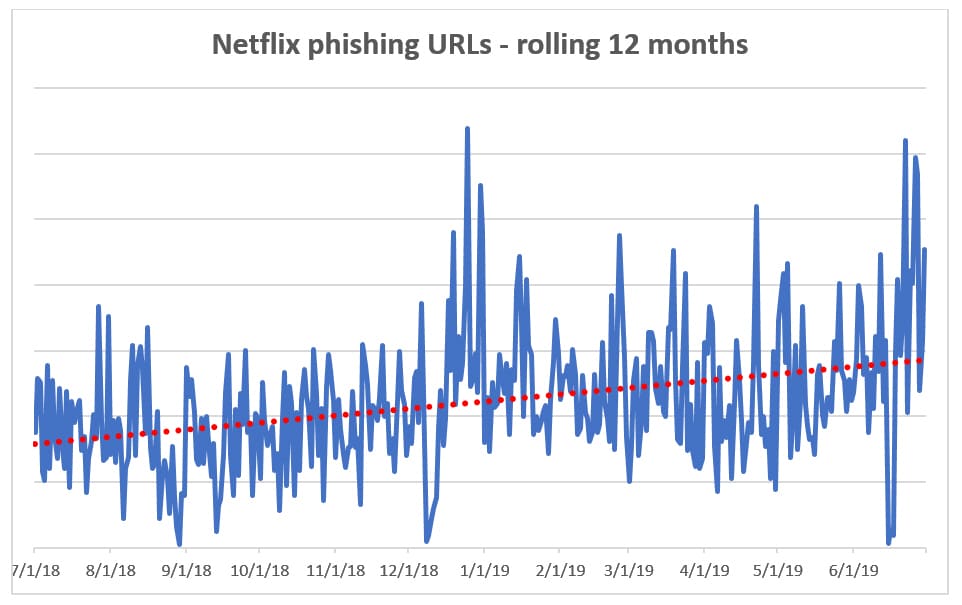
Spike in Netflix phishing in June 2019
The anticipation surrounding the release of the show had been building for months, and peaked in late June just before the release. This is a perfect scenario for a phisher -- the perfect time to send a phishing email telling subscribers their accounts are locked or need updated to avoid cancellation.
This "technique" worked well for phishers targeting HBO viewers in 2019. Seventeen million viewers tuned into the season premiere of Game of Thrones in April 2019. Around the same time, phishers lured Game of Thrones fans to phishing websites designed to look like fan sites. Many users provided personal and credit card information, thinking they were purchasing merchandise, singing up to stream the series for free, or registering for a prize giveaway. In another phishing scam, hackers impersonated HBO, claiming they had proof that victims had streamed the show illegally and asked for a copyright infringement payment.
In 2017, DirectTV users were targeted in a sophisticated phishing campaign that lured them with promises of a smaller monthly bill. Victims were asked to pay for the promotion with a pre-paid money card and directed to a phishing page to complete the transaction.
How do hackers know which shows subscribers prefer or which streaming services they use? Because we talk about and share content about our preferences obsessively. Millions of Game of Thrones fans battled it out on Twitter after the series premiere and throughout the life of the final season. In other cases, we complain endlessly on social media about our streaming services, from application performance and outages to billing issues. Our preferences and grievances are on display. Our contact information is spread across the web, making social engineering a simple enterprise.
Why third-party integrations are fueling phishing
In many cases, hackers exploit third-party app relationships to exploit and phishing victims. The OAuth 2.0 Authorization Framework allows users to grant access to their accounts to third-party applications. For example, you can sign in to tens of thousands of applications via Facebook and Google. Hackers exploit this by creating fake Facebook and Google login pages. The Apple Store is home to nearly 2 million apps, all of which are connected to an Apple ID. While some phishers actually compromise OAuth 2.0, it’s not necessary for them to do so. It’s only important for the victim to believe they are legitimately logging into a trusted app.
Spotify users were exploited in such a way in 2018. Hackers sent emails to Spotify customers confirmation a year’s subscription to Spotify. According to Wired, the email was intended to manipulate victims into thinking they’d been incorrectly charged. The phishing link led to a fake Apple ID page designed to steal the victim’s credentials.
Apple phishing saw 50 percent quarter over quarter growth in Q2 2019. A popular Apple phishing scam is the fake Apple receipt phishing email. The email includes a fake receipt for an app, movie, or music purchase. The phisher’s hope is that the victim will be alarmed at an erroneous purchase and divulge their login credentials on an Apple phishing page.
How to spot a phishing email
Riddled with typos and spelling mistakes, amateur phishing emails are easy to spot. Lately, phishing emails have been more sophisticated and can be difficult for the average user to detect. Always check the sender’s email address. Phishers use sophisticated spoofing methods to obfuscate the sender’s email address, including using Cyrillic characters and domain extensions (Microsoft.global.com). Other features to watch out for include subject lines that are intended to provoke fear or alarm ("Your subscription is cancelled!").
Finally, hover over any URLs in the email to see where they really lead. A Netflix URL will nearly always look like this: https://[something].netflix.com/[somethingelse]. "Netflix.com" must be before the 3rd "/". A phishing URL will look more like this: https://ntflxsecureplatform.com/accountsecurity/0e1422ea79781ee046484893ce0010c4.
Image credit: Allmy / Shutterstock
 As Vade Secure's Chief Solution Architect and CEO of Vade Secure North America, Adrien Gendre owns all aspects of the business that directly impact customer experience. His responsibilities include formulating the company's product strategy and roadmap, overseeing integration with security vendors, and managing the global Solutions Architect, Training, Documentation, and Customer Support Teams.
As Vade Secure's Chief Solution Architect and CEO of Vade Secure North America, Adrien Gendre owns all aspects of the business that directly impact customer experience. His responsibilities include formulating the company's product strategy and roadmap, overseeing integration with security vendors, and managing the global Solutions Architect, Training, Documentation, and Customer Support Teams.
