The phishing tricks that break through standard email filters

Some phishing emails are easy to spot: the spelling is bad, the spoofed email is clearly a fake, and the images are too warped to have possibly been sent by a reputable brand. If you receive one of these low-quality phishing emails, you’re lucky. Today’s phishing emails are extremely sophisticated, and if you’re not well trained to spot one, you probably won’t.
Email filters have long relied on fingerprint and reputation-based threat detection to block phishing emails. A fingerprint is essentially all the evidence a phisher leaves behind -- a signature that, once identified, will be recognized on future phishing attempts and the phishing email or webpage blocked. Examples of a fingerprint include the header, subject line, and HTML.
Reputation refers to phishing URLs and IPs or domains where phishing emails and webpages originate. An IP or domain that is identified as a sender or host for phishing emails and webpages is, like the fingerprint example above, identified and then blacklisted. The same goes for the phishing URL.
Once a tried and true method to stop phishing, hackers have developed new techniques to get around these outdated methods.
Fingerprint bypassing
They say every human fingerprint is unique. Likewise, the best way to evade fingerprint-based detection is to continually change elements of the email and web page so that each has a unique fingerprint -- and therefore is not blocked.
In a funny, yet telling example, one phishing campaign randomly inserted quotes from the movie Pulp Fiction as comments in the HTML code. These HTML comments were meaningless in the sense that they didn’t impact the look and function of the phishing email whatsoever. However, because each email contained a different quote, they all had unique signatures.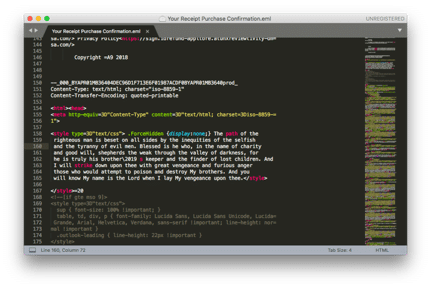
Another simple way that phishers bypass fingerprint-based detection is to make subtle modifications to colors. For instance, one email might use a shade of blue with the hex code #2188D7 while the next uses #1F88D8. The difference is imperceptible to humans, but will result in unique signatures for the emails.
Reputation bypassing
Email filters with reputation-based threat detection scan for abusive IPs, or IPs that are known for sending phishing emails and lots of them. Snowshoe attacks involve sending low volumes of phishing emails over a wide range of IPs that have a relatively good, although not always perfect, reputation. Snowshoe attacks are not new, but combined with other methods they confuse filters and improve the likelihood of a phishing campaign’s success.
Hackers also abuse legitimate domains, spoofing the email addresses and in many cases hurting reputations in the process. Microsoft and PayPal, for example, are the top spoofed brands in phishing attacks. Adding a simple extension to the Microsoft (Microsoft.com.co) or PayPal (PayPay.com.ca) domains are sometimes enough to fool filters.
In a literal hacking example, phishers will also hack legitimate websites and send phishing emails from the websites’ domains without the companies’ knowledge. This helps to avoid being detected by domain-name blacklisting.
If a hacker infiltrates a corporate email domain, detection becomes even more difficult. Office 365, for example, has seen an increase in compromised accounts resulting from phishing campaigns. Once a hacker is inside, they can send phishing or spear phishing emails to staff and customers or clients. Email filters that don’t scan internal email traffic would not detect any phishing emails sent within the company’s Office 365 account.
Image manipulation
Low-resolution, pixilated, or otherwise warped brand logos images are a tell-tale sign that an email or webpage is a fake. But quality images are only important to users. Email filters cannot see emails -- they can only scan the images’ meta data. If a hacker changes the code only slightly, the image looks the same but the attack signature has changed, making it a new, harmless email to the filter.
This presents two issues: First, a user could potentially receive the same phishing email more than once, if not several times. Second, if the user recognizes the threat and reports it, yet continues to receive the same email, they might assume that the email filter, or IT, or both, isn’t doing its job.
Slight image modifications are enough to fool a filter looking for an attack signature, but not sufficient to bypass a Deep Learning algorithm that can view and interpret images. Today, we’re seeing a variety of advanced methods to bypass those algorithms, including placing logos on colored backgrounds and on top of other images. This makes it more difficult for the algorithm to make the match.

Microsoft logo obfuscated by background color
Defending against sophisticated phishing attacks
Cybercriminals are aware of the technologies being deployed to stop them, and they’re actively honing their techniques to stay ahead of security vendors. Artificial intelligence makes a hacker’s work more difficult, although not impossible.
Trained with legitimate and illegitimate emails, machine learning models are trained to identify unique features of a phishing attack, including URLs, webpages, and content, as well as fingerprint and reputation evasion techniques.
Deep Learning models with Computer Vision analyze images rather than text. Properly trained, they can identify a brand logo or image in a phishing email whose attack signature has changed. Traditional algorithms might think the email is new, but the Deep Learning model can see that it’s the same email.
AI algorithms require a large dataset of threat intelligence and consistent fine-tuning to keep up with new threats. Businesses that are considering an AI-based solution should educate themselves about AI and the latest phishing threats and whether the proposed solution is capable of blocking the threats.
Photo credit: wk1003mike / Shutterstock
 As Vade Secure's Chief Solution Architect and CEO of Vade Secure North America, Adrien Gendre owns all aspects of the business that directly impact customer experience. His responsibilities include formulating the company's product strategy and roadmap, overseeing integration with security vendors, and managing the global Solutions Architect, Training, Documentation, and Customer Support Teams
As Vade Secure's Chief Solution Architect and CEO of Vade Secure North America, Adrien Gendre owns all aspects of the business that directly impact customer experience. His responsibilities include formulating the company's product strategy and roadmap, overseeing integration with security vendors, and managing the global Solutions Architect, Training, Documentation, and Customer Support Teams