Shadow IT in the 'Age of Coronavirus'

"May you live in interesting times!" This is one of the expressions that has received a lot of airtime in recent months. Clearly as a society we weren’t prepared for a pandemic and all the collateral impact that has resulted. But spare a thought for the IT and security teams that have recently dealt with perhaps the "most interesting" times. Everything they knew and trusted about their environment changed overnight. Think: remote workers, new insider threats and challenges associated with shadow IT.
To be fair, shadow IT was already a problem before the pandemic; our research shows the typical organization is aware of less than 50 percent of the digital assets that exist in their environment. However, in their race to ensure access to data and systems needed while sheltering in place, many end-users (inadvertently perhaps?) added significantly to the shadow IT problem. All of this is occurring as attacks have escalated with adversaries trying to take advantage of the chaos. So, what’s a security team to do about it?
Shadow IT and the Impact on Security
Why is shadow IT even a problem? It goes back to the idea that you can’t really defend what you don’t see -- or worse, don’t even know exists. Shadow IT assets are often intended to bypass the very organizational security policies intended to keep data secure. These devices typically don’t have any security software by default, so traditional endpoint or log-based solutions that rely on pulling telemetry of the device are rendered ineffective. Finally, the shadow devices can provide a backdoor into the network or be used to exfiltrate data, sometimes long after the employee who set them up has left the organization.
How Has COVID-19 Impacted Shadow IT?
In early March, as states and organizations made the decision to shelter in place, many employees presumably started thinking about how they could continue to be productive while working from home. Here are two real-world examples observed within our customer environments that clearly show that transition:
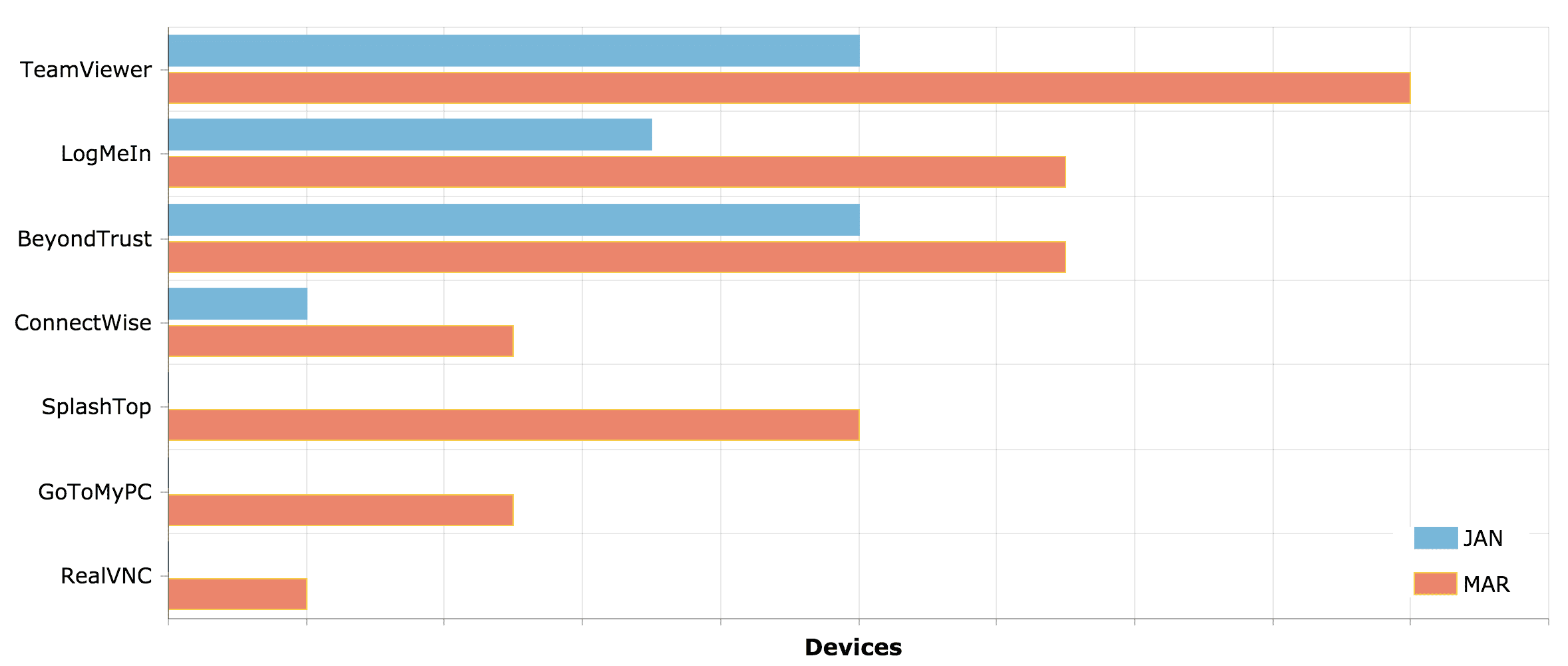
Remote Access Tools (RATs)
Remote access tools (RATs) like TeamViewer, LogMeIn and GoToMyPC are legitimate tools that are used to connect one computer to another one. The scenario here is connecting to a workstation in the office from a home computer. Many of these applications excel at doing so in ways that bypass corporate controls like firewall rules etc., which challenges any attempts to block these tools or monitor their usage. As you might expect, this increases the attack surface exposing the entire network through lateral movement from a compromised shadow IT device. In fact, a quick scan shows thousands of systems running TeamViewer are internet-accessible with only weak authentication controls, and many of these appear to sit in enterprise environments.
In fact, across our customer universe we observed a 75 percent increase in RATs between January and March. Many new tools showed up that didn’t exist in the environment prior as the graph below indicates.
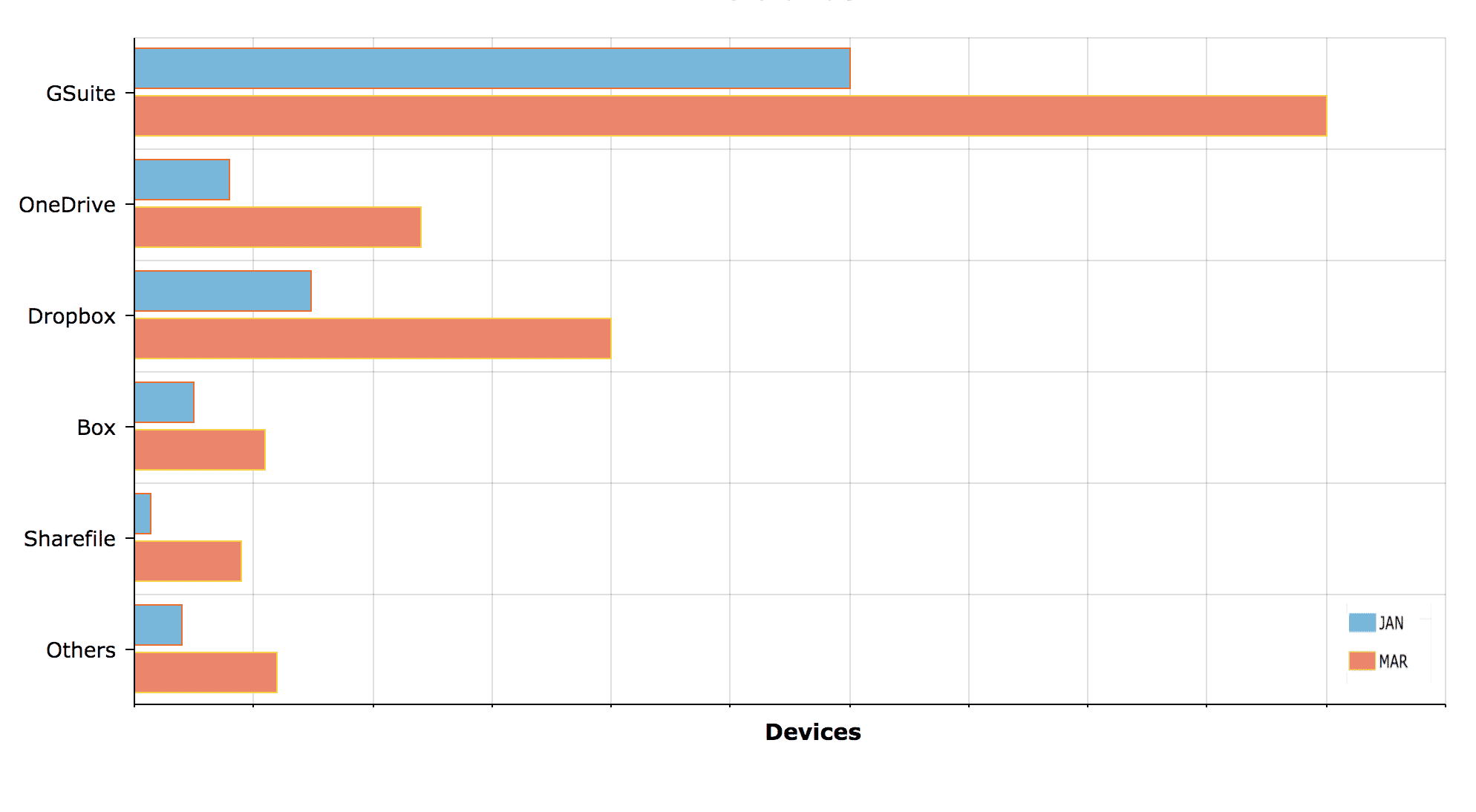
Cloud Storage and File Sharing Services
Another shadow IT spike we recently observed was with cloud-based services for file and data sharing. Think about it: you are asked to go remote and you really need access to those customer or supplier files to do your job. Someone suggested the files be uploaded to Dropbox, Google Drive, etc. so they can be download from home computers. Of course, you can delete them later… or so the plan goes. As the graph below shows, we saw a 65 percent spike in the use of these services during the January to March timeframe. Moreover, 40 percent of the traffic was headed to systems that were not approved for use at all within the organizations.
What should you do about it?
Start with visibility. Do you have the right tooling and processes in place to monitor shadow IT? As mentioned above, endpoint and log-based systems are unlikely to be useful here. Instead, network detection and response systems, proxies and cloud access brokers are better equipped to provide security teams with this visibility. Secondly, it’s important to understand what tools are approved within the organization and which are not. Data science approaches are useful here to spot deviations from the norm. Finally, from a security operations perspective, it is important to hunt for activities that appear to be accessing key digital assets and/or moving them around the network. This combination of visibility, detection and ongoing threat hunting can help mitigate the risk from shadow IT -- regardless of if COVID-19 or another phenomenon is causing a spike.
Photo Credit: Hans-Joachim Roy/Shutterstock
 Param Singh is VP of Security Research & Operations at Awake Security. He is a security innovator and thought leader with over 17 years of experience ranging from Threat Hunting, Threat Intelligence, researching APTs, Intrusion Detection, Big-Data Analytics, Penetration/Vulnerability Assessment, Security Audits and Secure Network Design.
Param Singh is VP of Security Research & Operations at Awake Security. He is a security innovator and thought leader with over 17 years of experience ranging from Threat Hunting, Threat Intelligence, researching APTs, Intrusion Detection, Big-Data Analytics, Penetration/Vulnerability Assessment, Security Audits and Secure Network Design.